Exploit in the wild for Apache HTTP vulnerability
The Apache HTTP Server, also called Apache or httpd is a free and open-source HTTP server. Apache is the most popular web server on the Internet for over two decades. Apache’s core functionality is to process HTTP request/response and dispatch data to threads and processes using it’s Multi Processing Module (MPM). A wide range of modules (mods) available to extend the core functionality.
Apache module mod_md is used to manage domains across virtual hosts, automate SSL certificate provisioning using the ACME protocol.
A null pointer dereference vulnerbility has been reported in the mod_md module of Apache (CVE-2018-8011). This is due to insufficient validation of input requests. A remote unauthenticated attacker could exploit this vulnerability by sending a crafted HTTP request to a vulnerable Apache. Successful exploitation of this vulnerability can lead to denial of service.
CVE-2018-8011 :
Apache httpd can be configured to load the module mod_md. if Apache running with mod_md, module functions md_http_challenge() or md_require_https_maybe() get called subsequently. These functions deference the pointer to PATH string without checking for NULL. This leads to segmentation fault or access violation.
Standard URI: <scheme>://<host>:<port>/<path1>/<path2>?<quername>=<queryvalue>#<fragment>
If Request-URI is sent with no path component in the HTTP request as follows:
GET <scheme>:// HTTP/1.1
Host: <host>
md_http_challenge() gets called with r->parsed_uri.path as NULL. String comparison dereferences the NULL pointer leading to access violation.
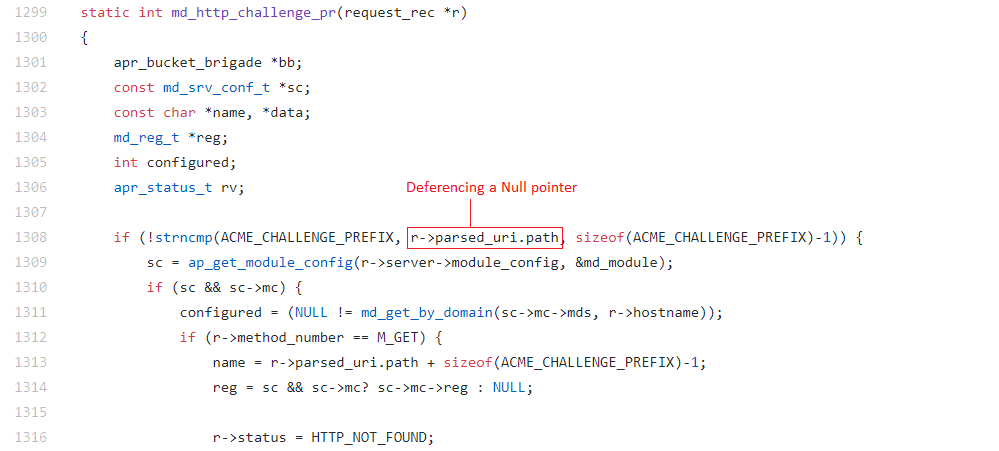
Fig:1 code snippet from mod_md.c
A remote attacker with no authentication can send a crafted HTTP request to a vulnerable Apache servers leading to Denial of Service (DOS).
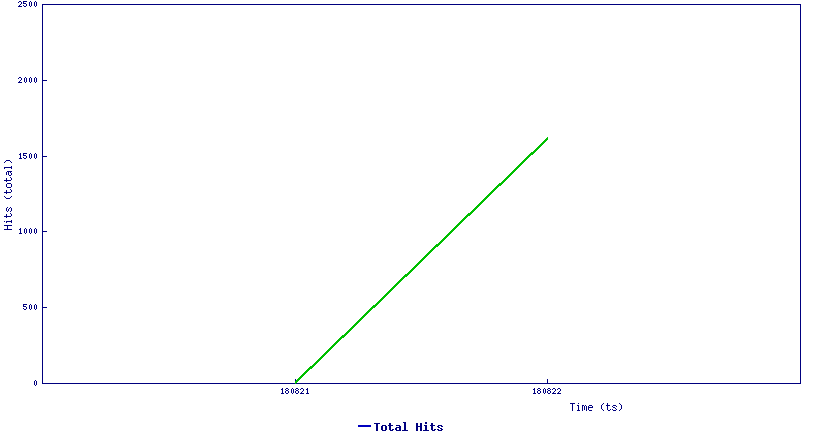
Trend Graph:
SonicWall has observed attackers actively leveraging this vector as you can see below the total no of unique hosts hit by this on just a day.
Patch:
Apache Software Foundation httpd 2.4.30 to 2.4.33 are affected by this vulnerbaility.
This is patched in httpd 2.4.34
Shodan search engine tells us that >1% of Apache servers on the internet (~300,000) are vulnerable to this, if they are configured to use the module mod_md.
SonicWall strongly recommends customers using Apache to update to the latest version.
If you continue to use the affected version, configure firewall access rules to block unauthenticated access.
Sonicwall Threat Research Lab provides protection against this exploit with the following signature:
- IPS: Suspicious Request URI 26
- IPS: Suspicious Request URI 27
- WAF: Protected. No new signature required.
