Attackers actively targeting vulnerable Dasan GPON home routers
SonicWall Capture Labs threat research team observed attacks exploiting old vulnerabilities in Dasan GPON home routers. DASAN Zhone Solutions is a provider of network access solutions for service provider and enterprise networks. The company provides a wide array of reliable, cost-effective networking technologies—including broadband access, Ethernet switching, Passive Optical LAN and software-defined networks.
Attackers are targeting following two vulnerabilities in GPON home routers:
Authentication Bypass Vulnerability
It is possible to bypass authentication simply by appending “?images” to any URL of the device that requires authentication. For example by the /menu.html?images/ or /GponForm/diag_FORM?images/ URI. Attacker can then manage the device.(CVE-2018-10561)
Command Injection Vulnerability
Command Injection vulnerability exists in Dasan GPON home routers via the dest_host parameter in a diag_action=ping request to a GponForm/diag_Form URI.The router saves ping results in tmp directory and displays them when user visits diag.html. This can be used to inject and execute commands.(CVE-2018-10562)
Following exploit is spotted in the wild


The attacker takes advantage of the above vulnerabilities to bypass authetication by appending “?images” to the POST request. Then the attacker downloads a malicious executable by injecting “wget” command. This is saved in the tmp directory and is executed when a user visits diag.html page.
SonicWall Capture Labs provides protection against this threat via following signatures:
-
- IPS 13340:Dasan GPON Routers Command Injection
- GAV:Mirai.H
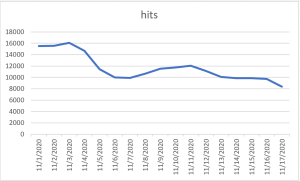
Threat Graph
IoCs:
59.99.45.126
117.213.46.186
117.194.165.174
112.27.124.174
42.234.109.14
2e4506802aedea2e6d53910dfb296323be6620ac08c4b799a879eace5923a7b6
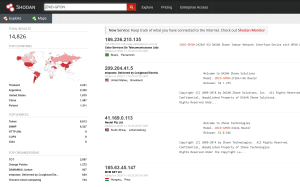
A quick look at Shodan reveals thousands of vulnerable devices