Microsoft InformationCardSigninHelper Class ActiveX control (CVE-2013-3918) exploit spotted in the Wild (November 20, 2013)
Dell Sonicwall Threats Research team has found In The Wild exploit utilizing the InformationCardSigninHelper Class ActiveX control Vulnerability (CVE-2013-3918).
The attacks that contain a specially crafted HTML page specifically target Internet Explorer.
We were able to successfully exploit Windows XP System running IE 8.
Following are the details of the attack.
We can see the vulnerable clsid instantiated using an object tag. The attack uses both javascript and vbscript interchangeably and calls vulnerable function while setting up ROP gadgets.

The code above gets translated to following ROP chain in the memory.

The ROP chain leads to VirtualProtect

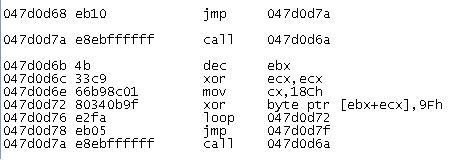
We can see the bytes are further XORed with 0x9f
Following shows how rundll32 process is created.

On successful execution, the process tries to make tcp requests to IP address 111.X.X.93 and its port 443.
We have a couple of signatures that cover the attack.
- IPS 7600 InformationCardSigninHelper ActiveX Instantiation (MS13-090)
- SPY 4736 CVE-2013-3918
