Clipboard Hijacker Dropped By STOP Ransomware
Recently we have seen multiple droppers dropping infostealers or banking trojans along with ransomware. Few weeks ago our researchers at SonicWall labs observed a clipbanker i.e. Clipboard Hijacker being dropped by djvu(STOP) ransomware.
Behaviour:
The Clipboard Hijacker malware was downloaded from URL hxxp://acacaca[.]org/files/1/build3[.]exe at path <Appdata>\Local\<UuId>\build3.exe. The dropped malware first uses dynamic API resolution to load APIs needed for further operations. It also makes sure that there is no other instance running by creating mutex “M5/610HP/STAGE2”. The name might implicate that this is the next stage of attack after ransomware execution.
It creates self copy at path <AppData>\Roaming\Microsoft\Network\mstsca[.]exe. This self copy is later executed using a scheduled task “Azure-Update-Task”. Task is scheduled to run every minute. The malware terminates itself after completing setting up scheduled task.
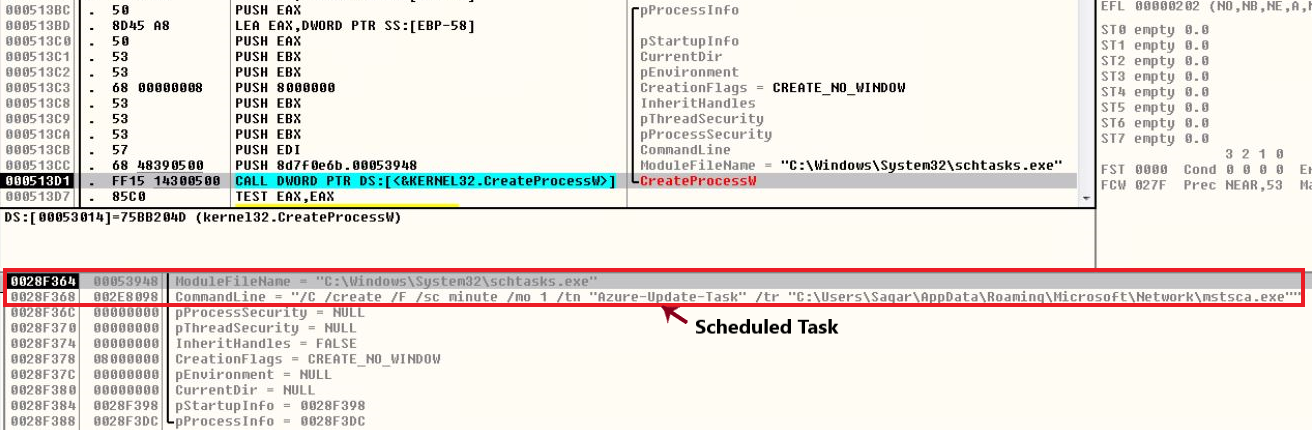
Fig 1. Scheduled Task
The mstsca[.]exe does the main clipboard hijacking activity. This again checks for mutex “M5/610HP/STAGE2” to confirm single instance is running at a time. The clipboard data is retrieved using GetClipboardData API. This data is then checked for string terminatore to check for separate strings in data.
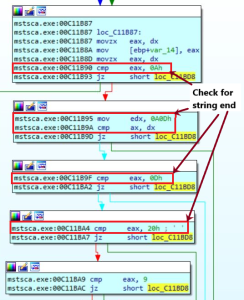
Fig 2. String Check
Once found a string, length of string is calculated and cross-checked with the length of desired wallet address lengths.
After confirming desired length it checks for starting characters of the expected wallet addresses. In some cases few wallets have same length but these are differentiated based on initial characters. Below mentioned is the code snippet checking for bitcoin wallet address(Native SegWit addresses start with bc1q).
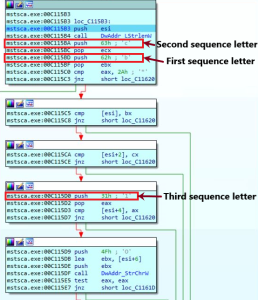
Fig 3. Bitcoin Wallet Check
This address from the retrieved clipboard is replaced by the address of same cryptocurrency already present in the binary. It continues to check for presence of other addresses till the clipboard data ends.
The replaced wallet addresses are copied to the current clipboard. The clipboard is cleared using EmptyClipboard and then the new data containing malware’s wallet addresses is copied to clipboard using SetClipboardData.
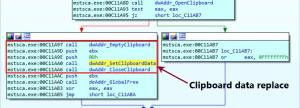
Fig 4. Clipboard Data Replace
After this, it sleeps for very short time and continues to check for clipboard data.
The malware has multiple wallet addresses of different wallets. One of the binance wallet from the list was mentioned in a magazin’s tweet(hxxps://twitter[.]com/westafricaweek/status/1471631329829834753). For this address, we have mentioned last one month’s amount received in below table.
Wallets:
|
Address |
Wallet | Amount Received($) |
|
1My2QNmVqkvN5M13xk8DWftjwC9G1F2w8Z |
bitcoin | 1,224.97 |
|
3NLzE3tXwoagBrgFsjNNkPZfrESydTD8JP |
bitcoin | 0 |
|
bc1qx8vykfse9s9llguez9cuyjmy092yeqkesl2r5v |
bitcoin |
0 |
|
bnb136ns6lfw4zs5hg4n85vdthaad7hq5m4gtkgf23 |
binance | 63,337,185 |
| DBbgRYaKG993LFJKCWz73PZqveWsnwRmGc | dogecoin |
0 |
|
0xa6360e294DfCe4fE4Edf61b170c76770691aA111 |
ETH | 918.67 |
|
LLiNjWA9h4LxVtDigLQ79xQdGiJYC4oHis |
LitCoin |
0 |
| MBD2C8QV7RDrNtSDRe9B2iH5r7yH4iMcxk | LitCoin |
0.23 |
|
ltc1qa5lae8k7tzcw5lcjfvfs3n0nhf0z3cgrsz2dym |
LitCoin | 0 |
| t1VQgJMcNsBHsDyu1tXmJZjDpgbm3ftmTGN | Zcash |
0 |
|
Ae2tdPwUPEZDqNhACJ3ZT5NdVjkNffGAwa4Mc9N95udKWYzt1VnFngLMnPE |
Cardano | 482.80 |
|
addr1qx4jwm700r2w6fneakg0r5pkg76vu7qkt6qv7zxza3qu3w9tyahu77x5a5n8nmvs78grv3a5eeupvh5qeuyv9mzpezuq60zykl |
Cardano |
6,683.23 |
Monero:
42UxohbdHGMYGPvW5Uep45Jt9Rj2WvTV958B5G5vHnawZhA4UwoD53Tafn6GRmcGdoSFUfCQN6Xm37LBZZ6qNBorFw3b6s2
89SPVUAPHDLSq5pRdf8Eo6SLnKRJ8BNSYYnvPL6iJxGP4FBCBmkeV3CTSLCbk6uydxRnub4gLH6TBRycxSAQN2m1KcnhrSZ
Although the malware has smaller functionality it may cause huge financial losses to victims. SonicWall Capture Labs provides protection against this threat via the SonicWall Capture ATP w/RTDMI.
IOCs:
Stop Ransomware(parent file):
327224ab99915741b54b4e5b836ea8248cf2fe90d2113271422095cea8211d96
Clipboard Hijacker(dropped):
hxxp://acacaca[.]org/files/1/build3[.]exe
8d7f0e6b6877bdfb9f4531afafd0451f7d17f0ac24e2f2427e9b4ecc5452b9f0(build3.exe)





