Coinminer employing LOLBins and distributed with multiple unstained components
SonicWall Capture Labs Threat Research team has observed a Coin Miner using multi-component approach.
Infection Cycle
Malware is delivered to victims as a self-extracting archive file which drops following two files:
-
- nur.bat
- wmine.exe (GNU wget tool)
nur.bat starts initially and makes provision for additional malware download and execution besides removing infection footprints. It uses wmine.exe to download OS specific additional malware file from remote location:
- noloadXP.exe (Windows XP)
- noloadnof.cab (OSes above XP)
noloadnof.cab contains a Base64 encoded executable file named “noloadn.crt” which is decrypted onto local storage as noloadn.exe, then executed.
Following command used to decrypt noloadn.exe :
- certutil.exe -decode noloadn.crt noloadn.exe
Here noloadn.exe is an archive file packed using UPX 3.95. This noloadn.exe contains files such as, grim20.ime, grim40.ime, inst.bat, intl.bat, intlu.exe, mnzk12.dat, msletni.ime, nirco.exe, Resmin.exe, restr.exe, Ring, vget.exe.
Additional file information:
- Resmin.exe and restr.exe are archive files, while grim20.ime, grim40.ime , msletni.ime are encoded cab files which later will be decoded by certutil tool and spawns executable out of it.
- Vget.exe is a non-interactive network retriever Wget tool same as wmine.exe , malware author simply renamed Wget tool as wmine.exe and Vget.exe.
- Nirco.exe is nothing but nircmd tool.
By running NirCmd with simple command-line option, you can write and delete values and keys in the Registry, write values into INI file, dial to your internet account or connect to a VPN network, restart windows or shut down the computer, create shortcut to a file, change the created/modified date of a file, change your display settings, turn off your monitor, open the door of your CD-ROM drive, and more. - Ring is a .sys file which is later moved to system32 folder by renaming it as “WinRing0x64.sys”

Fig1: commands present in nur.bat
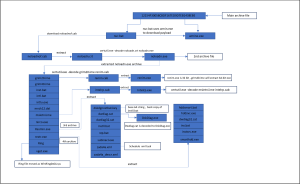
Fig2: Relationship between coin miner’s multiple components
System modifications
Following modifications are observed on the system after execution:
Files added:
Registries added:
SonicWall Capture Labs provides protection against this threat with the following signature:
- GAV: Cheetah.MNR
Indicators of Compromise (IOC):
- MD5: 12154f30058cbdf167ed9d7eb1438ebe
- SHA256: 4845254ed0e2d162d0e3bb95323ef106bd75bf24dc6d7b2371bab6704ae1c13c
Following are multiple components dropped by malware:
| FileName | Md5 |
| nur.bat | 8eefcaeed48be4eb4d6470330ccc24bf |
| wmine.exe | a9ff569c7cc92998180b0a5f9acac852 |
| intelrp.exe | 11831c3dc5941b909a86d83211f0d591 |
| renim.exe ( 32 bit ) | 34611952dbbac503d1f1bdda5f5e5522 |
| renim.exe ( 64 bit ) | 4f0fca816bedb8f99ce764c1bff2e7df |
| grim20.ime | 5dcbf2fb0043e0e7432f916ecbdd11e0 |
| grim40.ime | 425c2312cc45d22a187ee433a09f4179 |
| inst.bat | 95e74880eb068314055507540b25a0a0 |
| intl.bat | a322567b0553638fc9b9bd8d74e112c5 |
| intlu.exe | f3ca8234f60eba24604b5a9390d2fed5 |
| mnzk12.dat | 7829cb080d780f419ade0f031a66a985 |
| msletni.ime | b3bf512ffa11df457ed8c0c9b3c8133d |
| nirco.exe | ba07f81d94c84bfbae096b304a3a9206 |
| Resmin.exe | e88cd2ecd091f6170e70eb73e90f8900 |
| restr.exe | b5cacef347a785d9cabbf0385a3c2717 |
| Ring | 0c0195c48b6b8582fa6f6373032118da |
| vget.exe | 8eba146792a8a68c6e6992fee2071e23 |
| dskdgnostbat.key | 4ac6e2af5db82b97717c4f1ab45bd1c5 |
| dwdiag.cat | 6745b4829fa9f0195c730d849f6500ba |
| dwdiag32.cat | b9c240251c245f8e0ca7c1f54a6cdb5d |
| instll.bat | d3033eb75ff326cf03bcde41a75b3c7d |
| stp.bat | 79eb6c6f34ebc5c73fffea30cdcd7af2 |
| subinacl.exe | 53cdbb093b0aee9fd6cf1cbd25a95077 |
| zada4a.xml | 306d973bf0751c337e6239a58e35ff36 |
| zada4a_descr.xml | e0d29c37965bf8e40363113d02c3dd3d |
| hddsmart.bat | 31c029b19aa8b23223319e0f01a12545 |
| hddsvc.exe | f3ca8234f60eba24604b5a9390d2fed5 |
| ins.bat | ded0a61a14b906b69fd9dc5fc46110a2 |
| instsrv.exe | 7bc1928cd1d6ea2bce5fdb1fdeac0b3d |
| smarthdd.exe | 6eddcf70df22cd65b1cfa26de2513f32 |
| DskDiag32.exe ( 32 bit) | cbfdfcf530147abb18d9af84bb1736ae |
| DskDiag.exe ( 64 bit ) | 7c74c7e6f478e28453e085adf6c2b298 |




