New WoodyRAT Malware Found in the Wild
A new type of remote access trojan (RAT) has been identified by several AV companies. Dubbed ‘WoodyRAT’ due to the debugging information string, it is a multi-featured payload with a list of capabilities. As with many attacks, Woody has been found attached to Word documents, namely Russian documents titled “Information security memo”[1] in phishing emails. Using CVE-2022-30190 (Folina vulnerability), the executable is dropped to the system and launched.
The main file observed is 687kb in size and named “WindowsInternalApp.exe”. It has no packer, protector, or encryption.
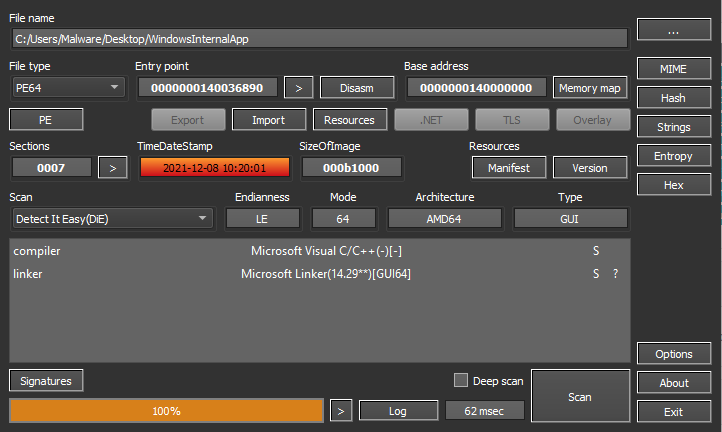
There are several items noted during analysis of the file. First, it has a non-standard section (_RDATA) listed.
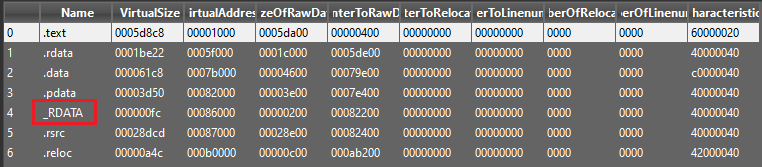
Second, the language listed for the file is in Russian; were the file legitimate, it would be English. There is also a lack of trademark icons, but the average user would probably not notice this.
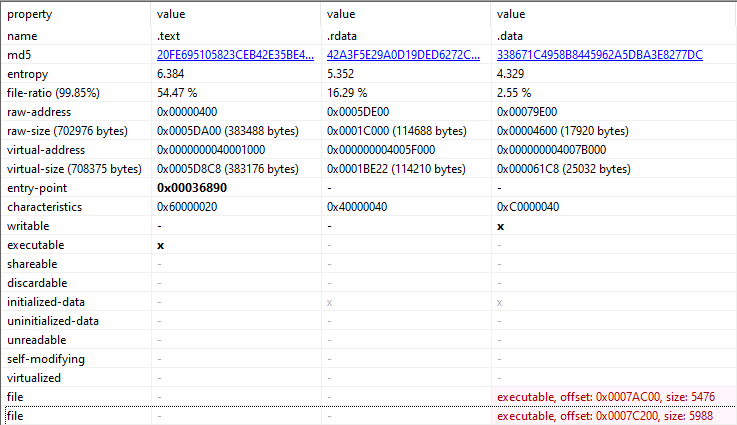
The third item is that there are two embedded executables in the .data section. This is very irregular and warrants investigation.
Looking through the strings of the file, there are very clear items that the malware is looking for. Antivirus programs, python and PowerShell versions, directory information, users, environment (OS), network connectivity, and permissions are among the data collected to be sent to the C2 address, which is also found and listed as hxxp://Microsoft-telemetry.ru/knock. As of this writing, the domain is no longer active. Since the strings are all in cleartext, the commands are listed as follows:
URL Commands: /knock, /submit, /ping
C2 Commands: _ACK, _CRY, _DAT, DMON, DNLD, _DIR, EXEC, INFO, INJC, PING, PSLS, PURG, _REQ, UPEX, UPPR, SCRN, SDEL, _SET, STCK, UPDM, UPLD
.NET Commands: DN_B, DN_D, PSSC, PSSS, PSSM
WoodyRAT also has a variety of anti-debug and anti-analysis tools. It will search for all major debuggers and disassemblers to try to prevent runtime analysis, as well as multiple antivirus engines. The embedded .NET and PowerSession files allow for more granular control from the C2, command storage using Base64 strings, and AV bypass.
Files
- WindowsInternalApp.exe
- md5: 243d0a9c1519df83c2d9122cb884f8d8
- sha1: b0799d496fe129e1b600e232897ee1d4796768e8
- sha256: 408f314b0a76a0d41c99db0cb957d10ea8367700c757b0160ea925d6d7b5dd8e
- imphash: Unable to generate
- DotNetExecutor.dll
- md5: 06FA1178578E5D72A6596A2B6B0CB8F0
- sha1: 5E66369BDDB1A29A3D0F84F3F111A9A4C9835D59
- sha256: 090B6D6D7E4950EED17D589179D34B88358C34AF749824D8B9525FAB7A406AB1
- imphash: 51C8A422DDBB923765C5E966868CD8DD
- Compiler-Timestamp: 0xCF53B7C4 (Fri Mar 22 21:57:24 2080| UTC)
- Debugger-Timestamp: 0xD200FB25 (Sun Aug 24 16:47:33 2081| UTC)
- Reference: https://github.com/JerrettDavis/DotnetExecutor
- PowerSession.dll
- md5: 074666CD14549003CA9A0A3F2310FD26
- sha1: BD2ACCF2CA4CDA0E330D87BFB3A64FB9684309D6
- sha256: AFB190B89DD98FCA76B66F27A80551142A8B78BE9EFB14CC5D3D45C20D67D109
- Imphash: FDBD1C9EE827DA590ABA590AA8E414D2
- Compiler-Timestamp: 0xD064136C (Tue Oct 15 12:05:00 2080| UTC)
- Debugger-Timestamp: 0xDF0FE3F6 (Tue Aug 03 08:36:06 2088| UTC)
- Reference: https://github.com/Watfaq/PowerSession
URL
Microsoft-telemetry.ru
Strings
- C:\Users\user\Desktop\woody_2\clone\SharpExec\DotNetExecutor\obj\Release\DotNetExecutor.pdb
- C:\Users\user\Desktop\dev\sharp-memory\PowerSession\obj\Release\PowerSession.pdb
- C:\Users\user\Desktop\woody_2\build\bin\WoodyNode.pdb
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: WoodyRAT.A (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.




