Malicious Embedded Office File inside PDF is delivering REMCOS RAT
SonicWall Capture Labs Threat Research team has observed a malicious PDF file, comes as an e-mail attachment, detected by SonicWall RTDMI ™ engine which is delivering REMCOS RAT as the final payload.
The PDF file has a malicious embedded doc file, which is dropped and executed from %temp% folder. PDF file has an OpenAction tag, set to a javascript which is embedded in PDF. On opening the PDF file the script is executed. Embedded DOC file name is “has been verified. However PDF, SVG, xlsx, .docx”.
The DOC file has a reference to an external URL, which is a RTF file. It loads the RTF file from “hxxps://shortener[.]vc/fSpur”, whose final redirected URL is “hxxp://45[.]85[.]190[.]156/receipt/290.doc”. This RTF file has a CVE-2017-11882 exploit, which further downloads an .Net executable at “C:\Users\Public\vbc.exe” and executes it.
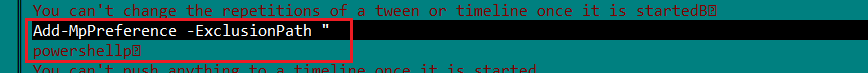
The .Net executable ‘vbc.exe’ makes a copy of itself in %APPDATA% as ‘doc.exe’, and creates RUN registry entry for it as ‘wix’. And then executes doc.exe.
The .Net executable file has a compressed .Net DLL file in its ‘AppPropsLib.Documents.resources’ resource object named as ‘_22’. It decompresses the resource and loads the obfuscated DLL(internal name of the DLL is Periodicity.dll) in the memory and calls its second export, and passes it three string arguments “5374617469634172726179496E69745479706553697A65”, “7157624F” and “AppPropsLib”. First argument is “StaticArrayInitTypeSize” (passed in hex format) name of another Bitmap object present in the doc.exe resource, second argument is the decryption key “qWbO” (passed in hex format) and third argument is the resource name in doc.exe.
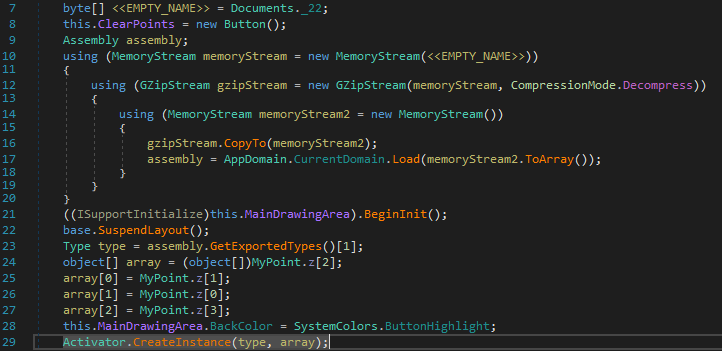 Then Periodicity.dll loads the bitmap resource present in doc.exe and extracts ARGB values for all the pixels in an array. It then gets the encrypted data size from the first pixel ARGB value and copies the encrypted data into another array, then starts decrypting it using the key passed as an argument and the last byte of the encrypted data array.
Then Periodicity.dll loads the bitmap resource present in doc.exe and extracts ARGB values for all the pixels in an array. It then gets the encrypted data size from the first pixel ARGB value and copies the encrypted data into another array, then starts decrypting it using the key passed as an argument and the last byte of the encrypted data array.
The decrypted data is yet another .Net highly obfuscated DLL file whose internal name is Thookinieng.dll. The .Net DLL has encrypted resources, one of which is REMCOS RAT. Its decrypted data has some interesting string :
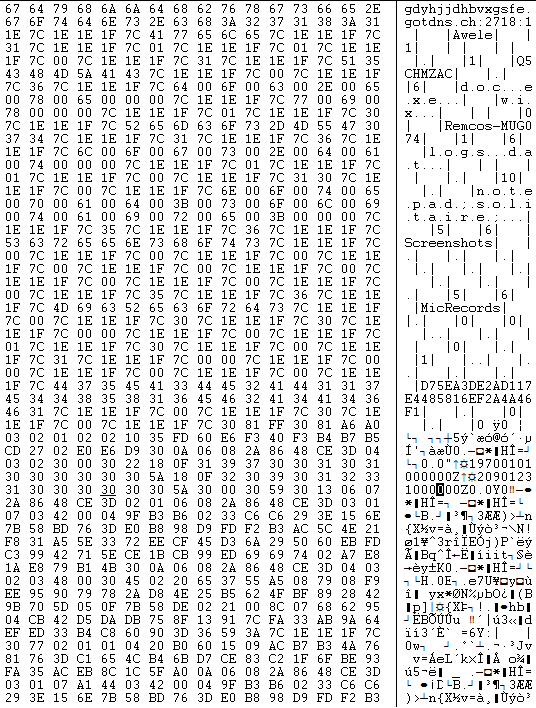
REMCOS keeps the configuration information in the resource named as settings. The very first byte tells us the RC4 key size, followed by RC4 key which is further followed by the encrypted configuration information:
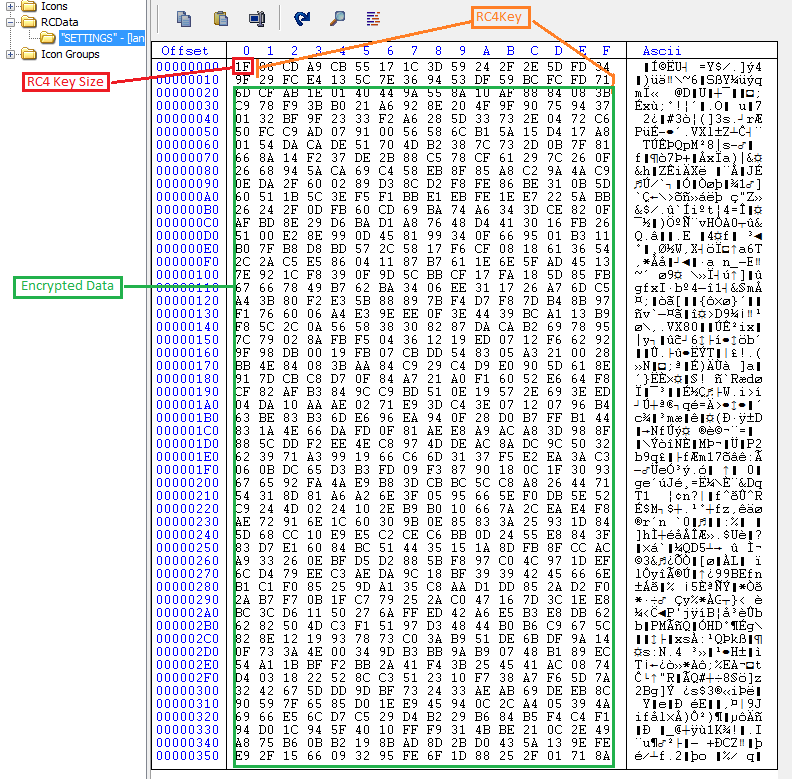 The version of REMCOS Rat payload is ‘v3.4.0 Pro’ .It reads the key from the resource and decrypts configuration data using RC4 algorithm which contains Command and Control (C&C) server’s IP address, port number, password, REMCOS executable’s name and key logging filename etc.:
The version of REMCOS Rat payload is ‘v3.4.0 Pro’ .It reads the key from the resource and decrypts configuration data using RC4 algorithm which contains Command and Control (C&C) server’s IP address, port number, password, REMCOS executable’s name and key logging filename etc.:
Malicious PDF hashes:
- f33170bbdf2c134c5de88cd931f850db16c093a9a26694040f889cea2c485cec
- 677011006f557a3c25befb217086f099708077c6d27e091e16be15f619fa9547
- 1f8a033bf8d5ab6d08b618980565c7f633985c154f5b8f6086f48b3d8304f906
- baa63cbb933cd6b69e18a9db664b95eb03902deb49767d94ab5b23322aeed650
- 3c29a03355bf0daea04e1c9f14523f71b88d839a3aab4ef52326f5632973d747
- d762702d22cbd585c26f778dd47cbb6807679f7a5b7e7b8eedb63676db0bcf71
The file is detected by few security vendors on popular threat intelligence sharing portal VirusTotal at the time of writing this blog, this indicates its spreading potential:
Evidence of detection by RTDMI ™ engine can be seen below in the Capture ATP report for this file:


 Infection Cycle:
Infection Cycle: