Android Malware impersonates Google Update Application with old traits
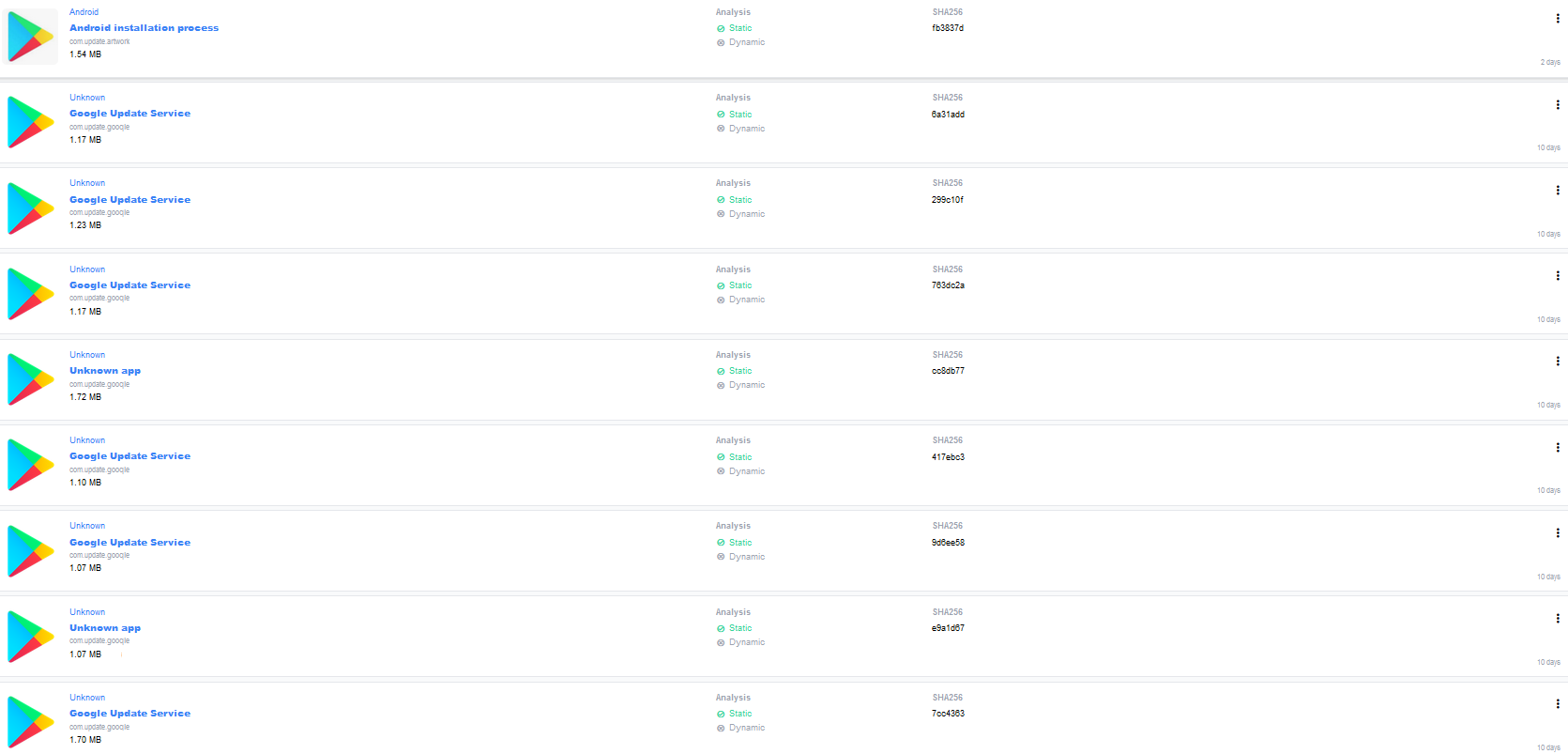
SonicWall Capture Labs Threats Research team has been regularly sharing information about malwares including spyware targeting Android devices. SonicWall has tracked down a huge number of fake applications disguised as legitimate Google update applications.
Fig 1. Fake Google Update applications
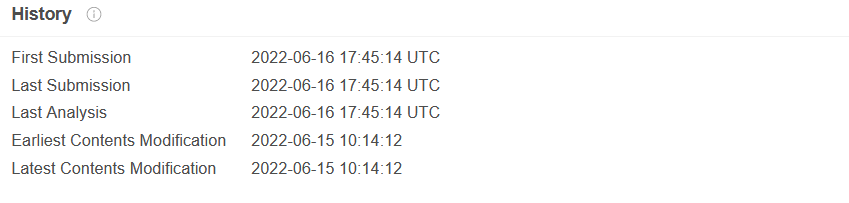
The new version of the spyware is recently available on malware-sharing platforms like VirusTotal.
Fig 2. VirusTotal submission history
Infection Cycle:
Most of the fake malicious google updater apps have some common activities of spyware and a few of them work as banking trojan as well.
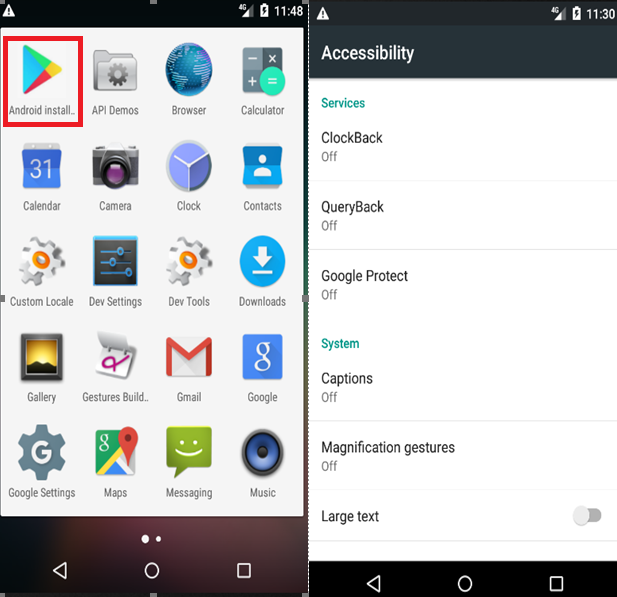
After installation, the apps ask for Accessibility permission and then hide from the app drawer.
Fig 3: App Installation & Accessibility permission
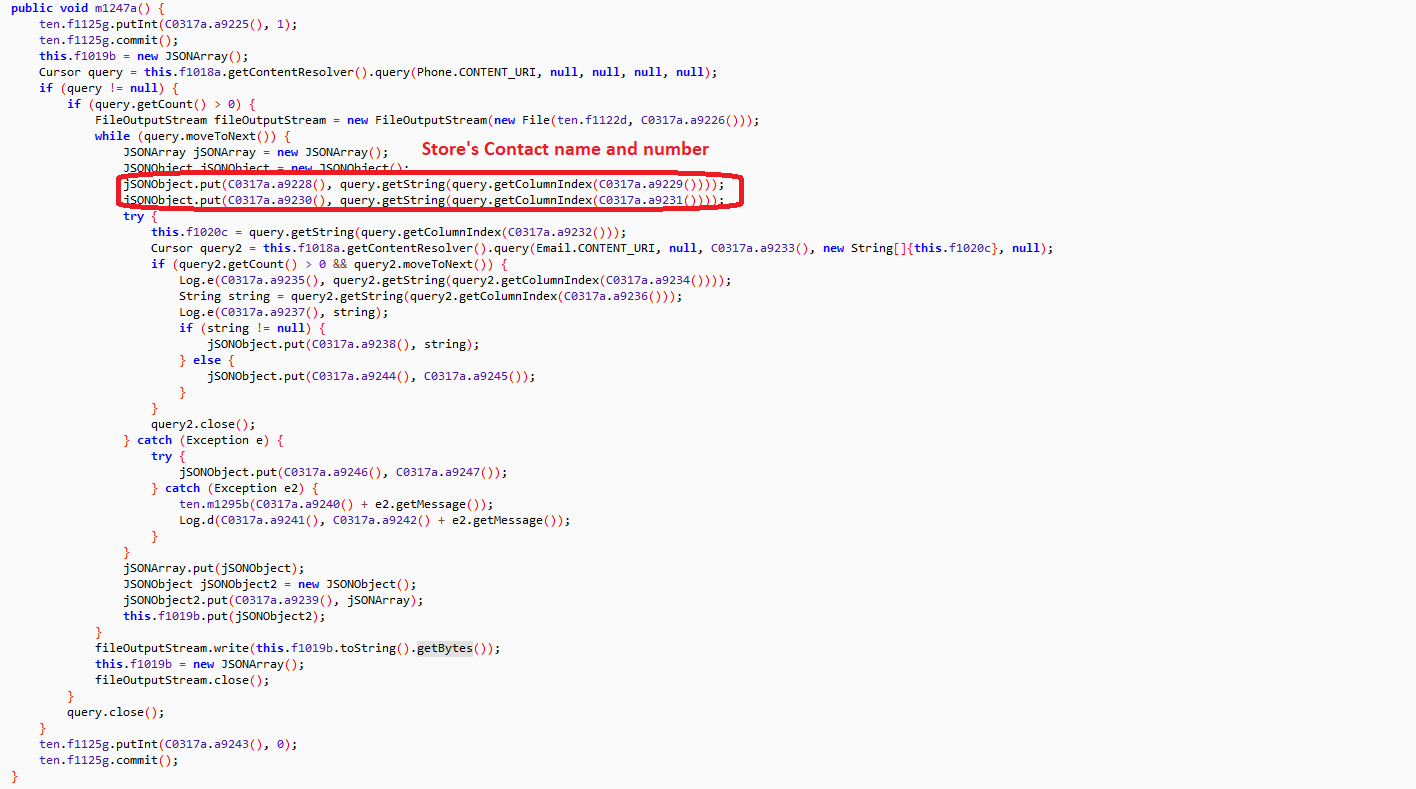
It accesses the following activities on the device and tracked information is saved in the corresponding .json file and establishes a socket connection with C&C server “help.domainoutlet.site” and shares the device information in JSON file.
- SMS
- Call logs
- Call Recording
- Device Info
- Location
- Keyloggers
- Device Contact
- Notification
Fig 4: Storing contact details in JSON file
In some cases, along with spyware activities it also acts as a Banking Trojan, like SHA-256 fb3837dc602c3f51939891b75a34d706bbefa73f822cffffeb1b863a6526bf95 .
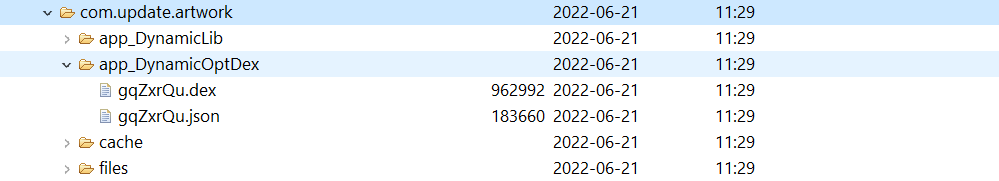
Dex file is dynamically loaded which contains the malicious banking trojan code.
Fig 5: Load Dex file
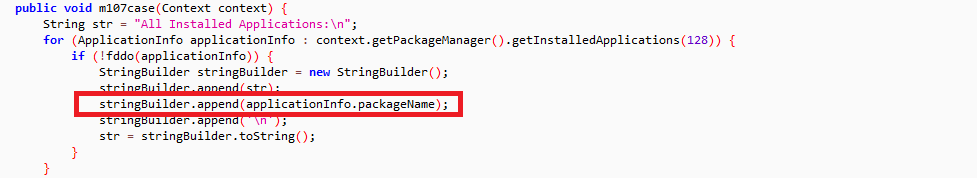
It checks for installed applications and compares them against specific package names preferably banking and Cryptocurrency apps (350+ apps). Once it determines that one of these apps is being used, it can carry out an overlay attack. In order to carry out an overlay attack, it places fake page over legitimate apps which looks similar to steal credentials.
Fig 6: Checking installed apps
Fig 7 : Load WebView for overlay attack
Fig 8: List of targeted apps
SonicWall Capture Labs provides protection against this threat via the SonicWall Capture ATP w/RTDMI.
Indicators of Compromise (IOC):
01d0e1996d0ba3ff4e0bac4747b0e0d955fe93ac3cca62caebc46dfd4f4b811f
1ac57a4bc06ebdd42ffed1d63e7731eade4a58c302641f3373f2a42298e461e2
299c10f9f438b8176b8f49654952d9189ddcf3b9e44e834c54db7410ac2af9f1
417ebc3a1dcc71f76d67b97adffd239399110b18eb644ef0da74061c7d569ef7
421f4aeedfec86eb756ac9acbb55014d973f2aa7136718cfd93829944998878a
65c9fd0fb77c08319ff8047f7c9302da843f8dcea9a8bad482850c9e3bd545cf
6a31addaad870460f0713fe057cb7a47fffe426f2217dcb2e0167b4257f356c0
763dc2a295d95ed24e2f9081ff192d079f9d6837f8e6ad15f6453542dd0c2ab9
85a710df11765d424f367abcbb61b70bbc42ef1969e7fd59968c784a8b5937da
8a15e9deb145e90cff2bf414842221afc04494c90d0a8af7e059e2273f661934
9d6ee58c17c62ef5ff8d586a6bea437dbaa856a0ac96c8e425063a55e23d6b11
c56862b2de6d04d15bc11f1dffed108099a3f0c92098383774580eadd551fc82
c745c5c4032e6b6036e25d1efad8f30470aee99f368a923509f570310e5d2644
cc8db772726e5d3d4ec680cd53587d79592c7a5a83148ff5b5ec0b7b7ce1781c
fb3837dc602c3f51939891b75a34d706bbefa73f822cffffeb1b863a6526bf95