A look at PartyTicket Ransomware targeting Ukrainian systems
The conflict between Russia and Ukraine has quickly escalated from the ground onto the cyberspace. Last week, the Sonicwall Capture Labs Research team has analyzed the HermeticWiper malware attack that was targeting Ukraine in this article. This week we take a look at the ransomware that was believed to have been deployed in conjunction with the aforementioned data wiping malware.
Infection Cycle:
The ransomware arrives as a Windows executable. Once executed it spawns conhost exe which then spawns cmd exe to carry out its functionality.
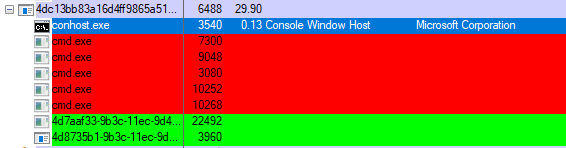
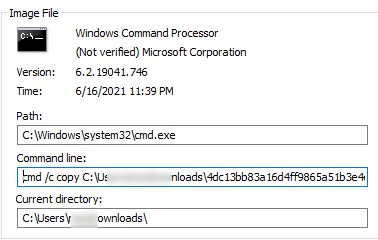
Cmd creates a temporary copy of the ransomware which then encrypts a target file.
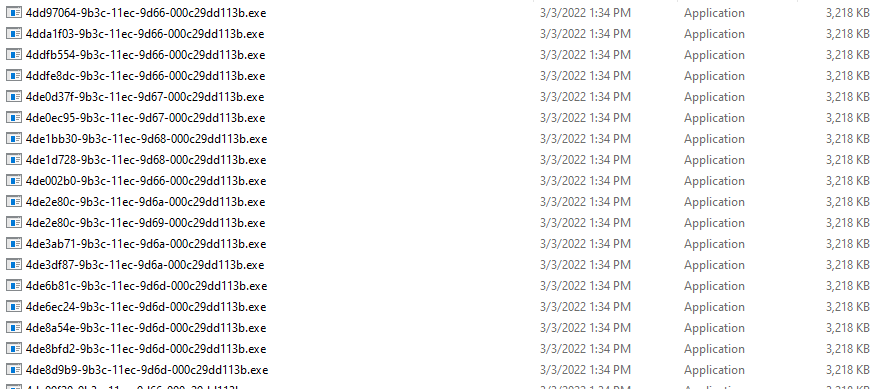
This simultaneous action of create, encrypt, delete bogs down the system and just makes the entire process really slow. Below is an example of how many copies of itself was created in a span of a few minutes trying to encrypt a system.
The following file extensions are targeted for encryption:
acl.avi.bat.bmp.cab.cfg.chm.cmd.com.crt.css.dat.dip.dll.doc.dot.exe.gif.htm.ico.iso.jpg.mp3.msi.odt.one.ova.pdf.png.ppt.pub.rar.rtf.sfx.sql.txt.url.vdi.vsd.wma.wmv.wtv.xls.xml.xps.zip
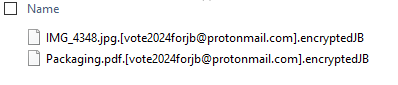
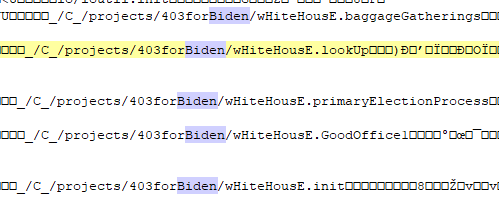
Encrypted files have an appended file extension of “[vote2024forjb@protonmail.com].encryptedJB”
A ransom note named “Read.me.html” is added on desktop.
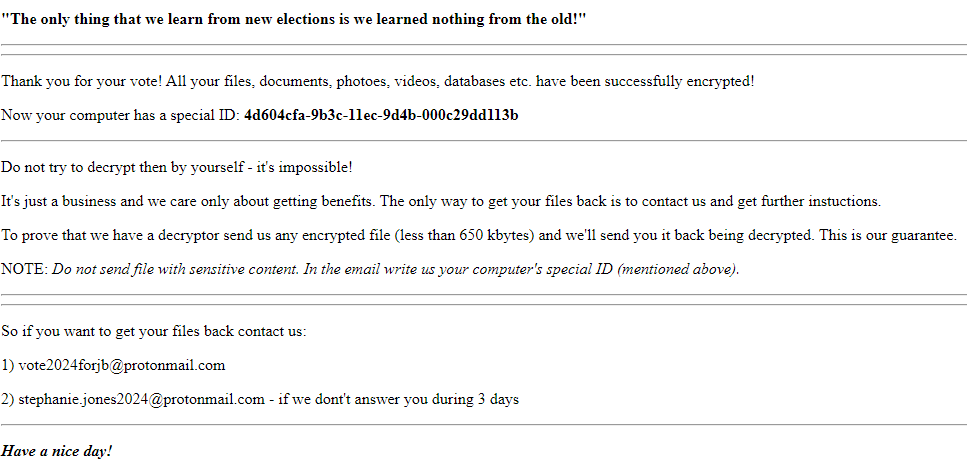
There are references to the US President in the module/project names used in the file as evident in the strings below possibly to obscure the real source of malware or mislead researchers.
Overall this is an unsophisticated ransomware that appears to be created in a rush.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: PartyTicket.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.




