Linux-based ransomware found targeting VMWare ESXi Servers
The Sonicwall Capture Labs threat research team has come across a linux variant of a ransomware early on this week. Avoslocker is another ransomware-as-a-service (RaaS) selling their ready-made ransomware to affiliates to carry out ransomware attacks. This linux variant was specifically made to target VMWare ESXi servers that more and more companies are switching their servers on to for easier management. It is a very valuable target for cybercriminals since one ESXi server can host multiple virtual machines and therefore host many critical services for a company.
Infection Cycle:
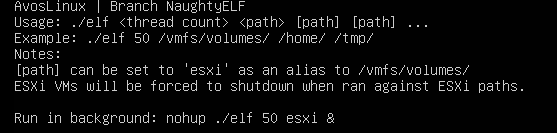
This variant comes as an ELF executable file. Upon manually running it, the user is presented with the following use options.
Once installed, Avoslocker will run the following command to power off all running virtual machines within an ESXi host.
esxcli –formatter=csv –format-param=fields==”WorldID,DisplayName” vm process list | tail -n +2 | awk -F $’,’ ‘{system(“esxcli vm process kill –type=force –world-id=” $1)}’
It appends “.avoslinux” extension to all encrypted files.
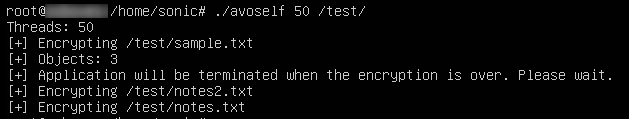
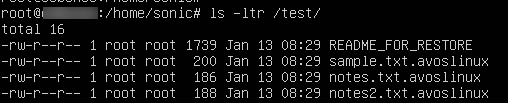
It also leaves a ransom note reminding victims to avoid shutting down their system to prevent any files being permanently damaged.
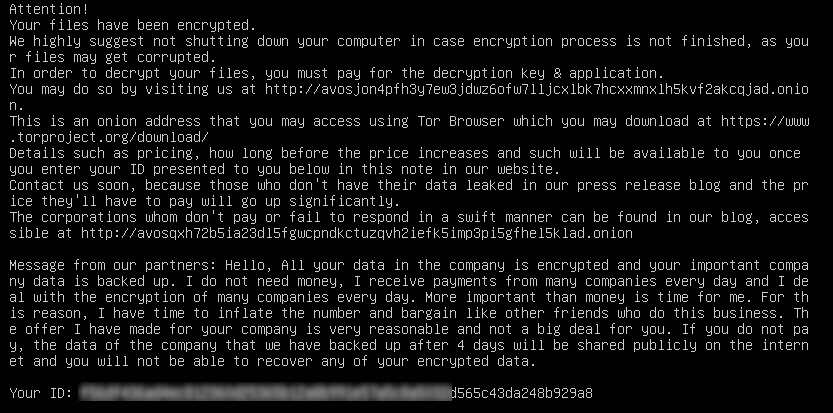
They provide a link to a website only accessible via a tor browser for further details on how to pay and retrieve encrypted files.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Avoslocker.RSM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




