WordPress websites plagued by fake ransomware
A number of WordPress websites have been infected with what appeared to be ransomware. The infected websites show a warning on its homepage saying the site has been encrypted and listing a bitcoin address on where to send payment to restore the site. But further analysis finds that the warning was fake and was just meant to scare and extort money.
Infection details:
Websites that are infected show a warning sign on their homepage:
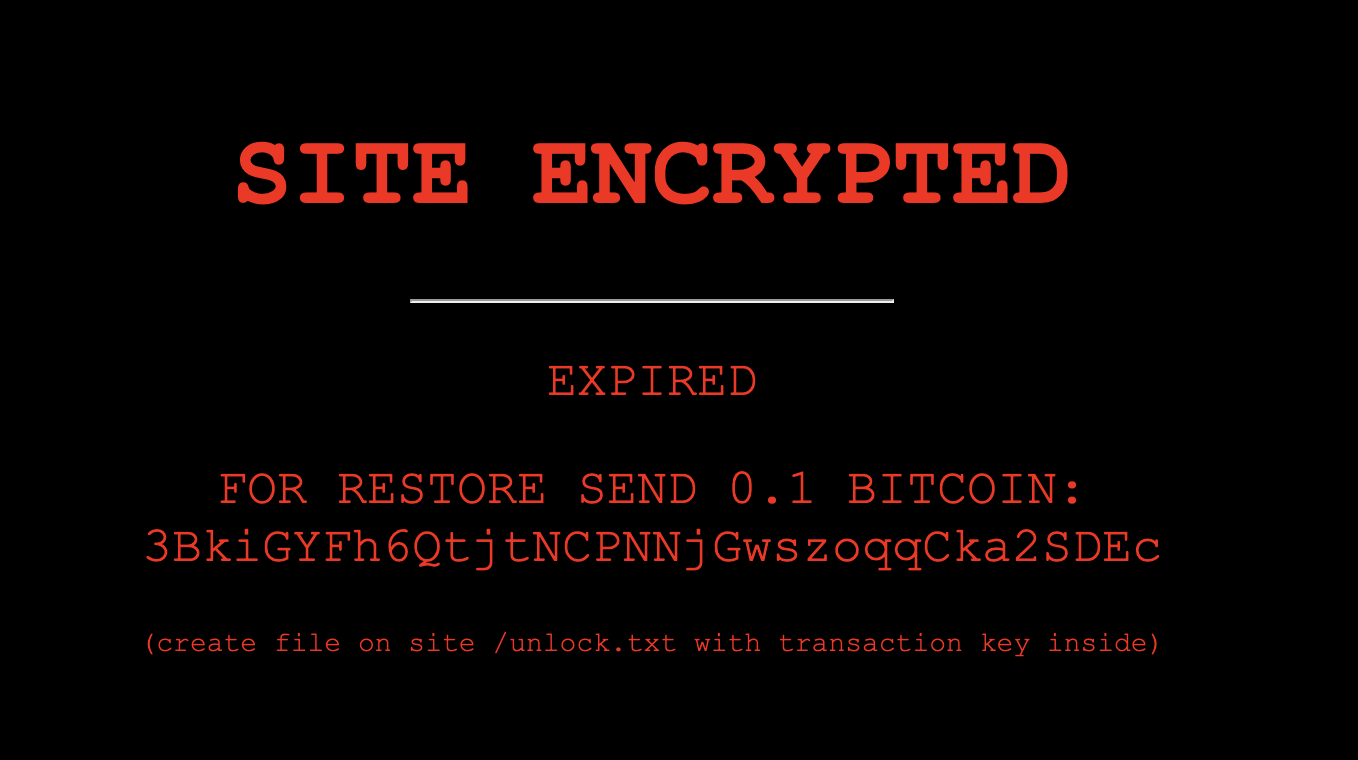
But this warning turned out to be bogus and is just a simple html page.
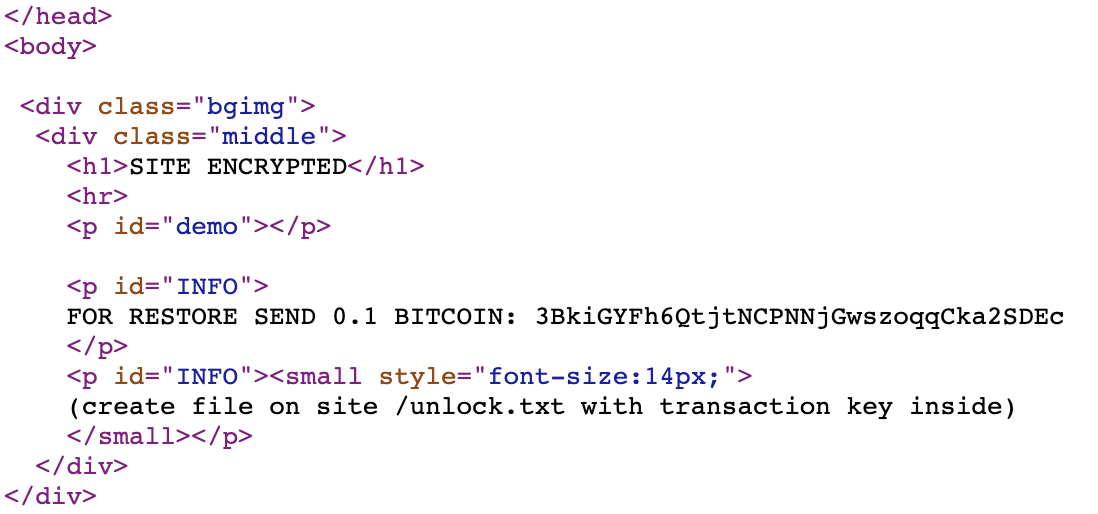
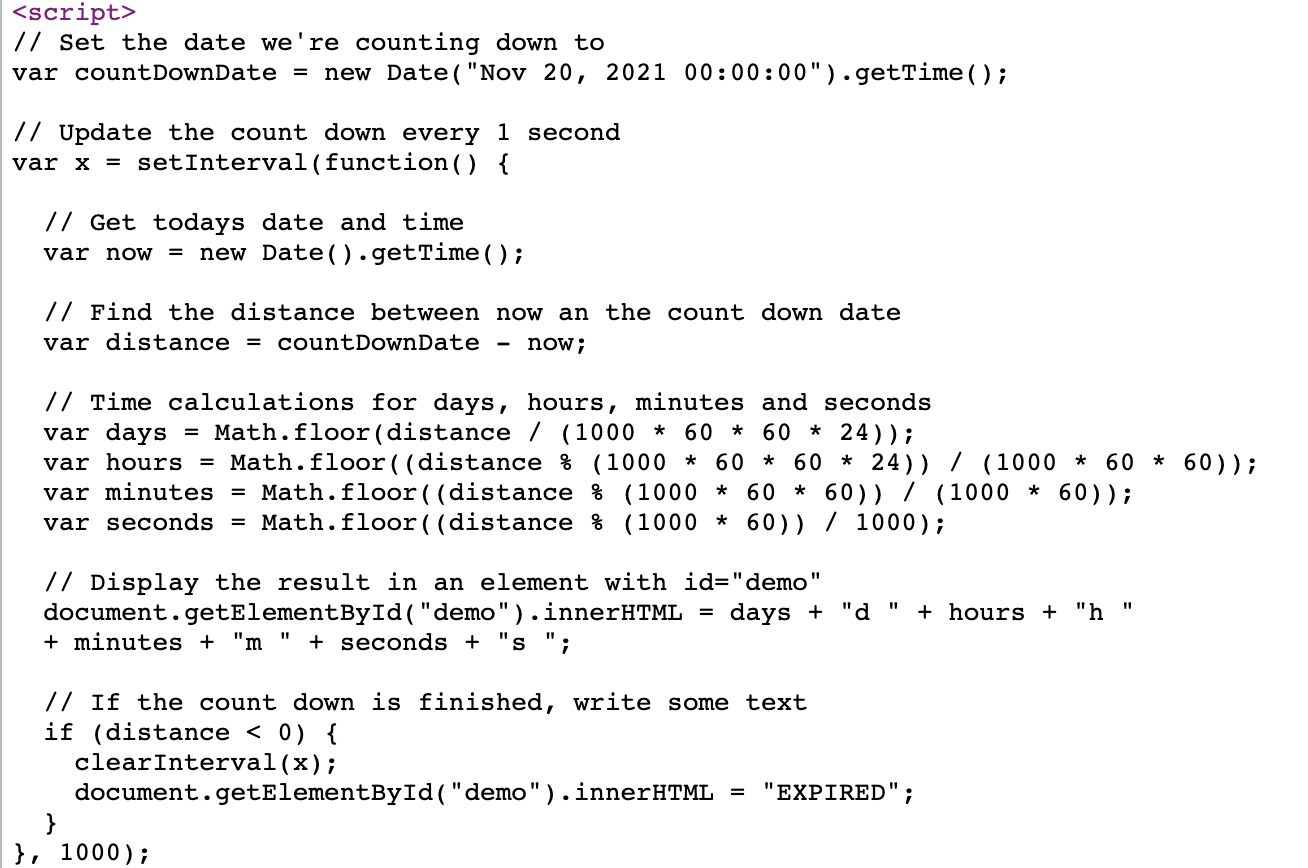
It also includes a simple script to add a countdown timer to add a sense of urgency and make it more believable.
It appears that an infected directorist_base.php was responsible for the bogus warning page. But nothing was encrypted.
Although another file named “azz_encrypt.php” is being referenced but the file cannot be found in the system. Presumably this file can be used for encrypting the system given the filename.
These compromised websites had no serious damage and these cybercriminals just wanted a quick buck using a simple hack. However, the fact that these cybercriminals were able to get access and deploy this rather effortless scheme means they could have done more damage had they used a more sophisticated malware.
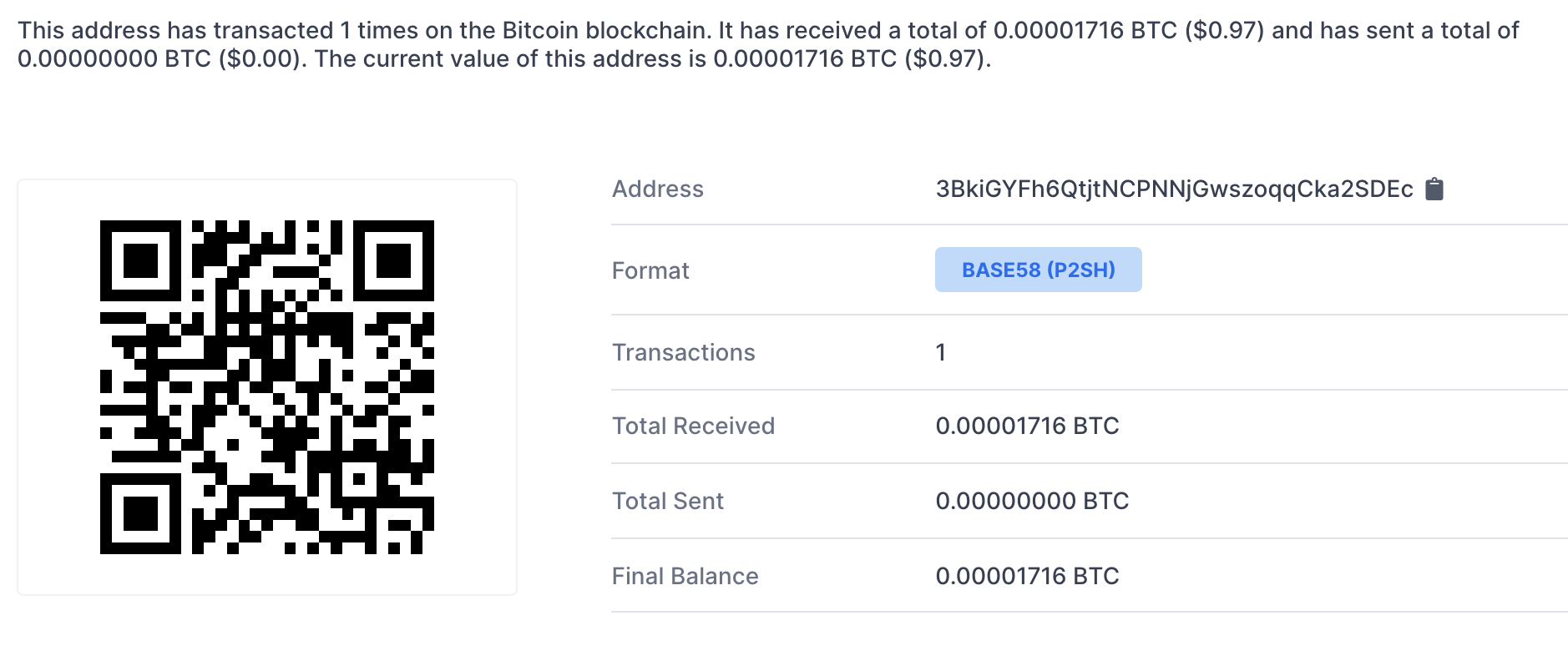
A quick google search for the phrase “FOR RESTORE SEND 0.1 BITCOIN:” turns up quite a few websites that are infected with this malware. However, it appears that none of them had been scared enough to pay the demand since the bitcoin address specified on the warning has not received any payment yet.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV:FakeWP.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.