WordPress WooCommerce Plugin SQL Injection
WooCommerce Blocks offers a range of Gutenberg blocks you can use to build and customize your site. Designed to work with the new Block Editor introduced with WordPress 5.0, WooCommerce Blocks offers a range of blocks you can use to build and customize your site. A SQL injection vulnerability exists in the WooCommerce Blocks feature WordPress plugin.
Sql Injection
SQL injection attacks are a type of injection attack, in which SQL commands are injected into data-plane input in order to affect the execution of predefined SQL commands. A SQL injection attack consists of insertion or “injection” of a SQL query via the input data from the client to the application. A successful SQL injection exploit can read sensitive data from the database, modify database data and execute administration operations on the database.
WordPress WooCommerce Plugin SQL Injection vulnerability | CVE-2021-32789
All WooCommerce sites running the WooCommerce Blocks feature plugin between version 2.5.0 and prior to version 2.5.16 are vulnerable to sql injection.This vulnerability could be exploited via a carefully crafted URL exploit against the ![]() endpoint. A successful attack could lead to sensitive information disclosure. No authentication is needed to execute this attack.
endpoint. A successful attack could lead to sensitive information disclosure. No authentication is needed to execute this attack.
Typical attack looks like this

This query will pull all the table schema information from the database.
![]()
This query will return admin users.

The query will return associated database fields with hashed passwords.
This vulnerability is patched.
SonicWall Capture Labs provides protection against this threat via following signatures:
- IPS 15661: WordPress WooCommerce Plugin SQL Injection
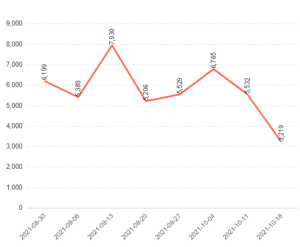
Threat Graph