AtomSilo hits large Brazilian company in $1M double extortion scheme
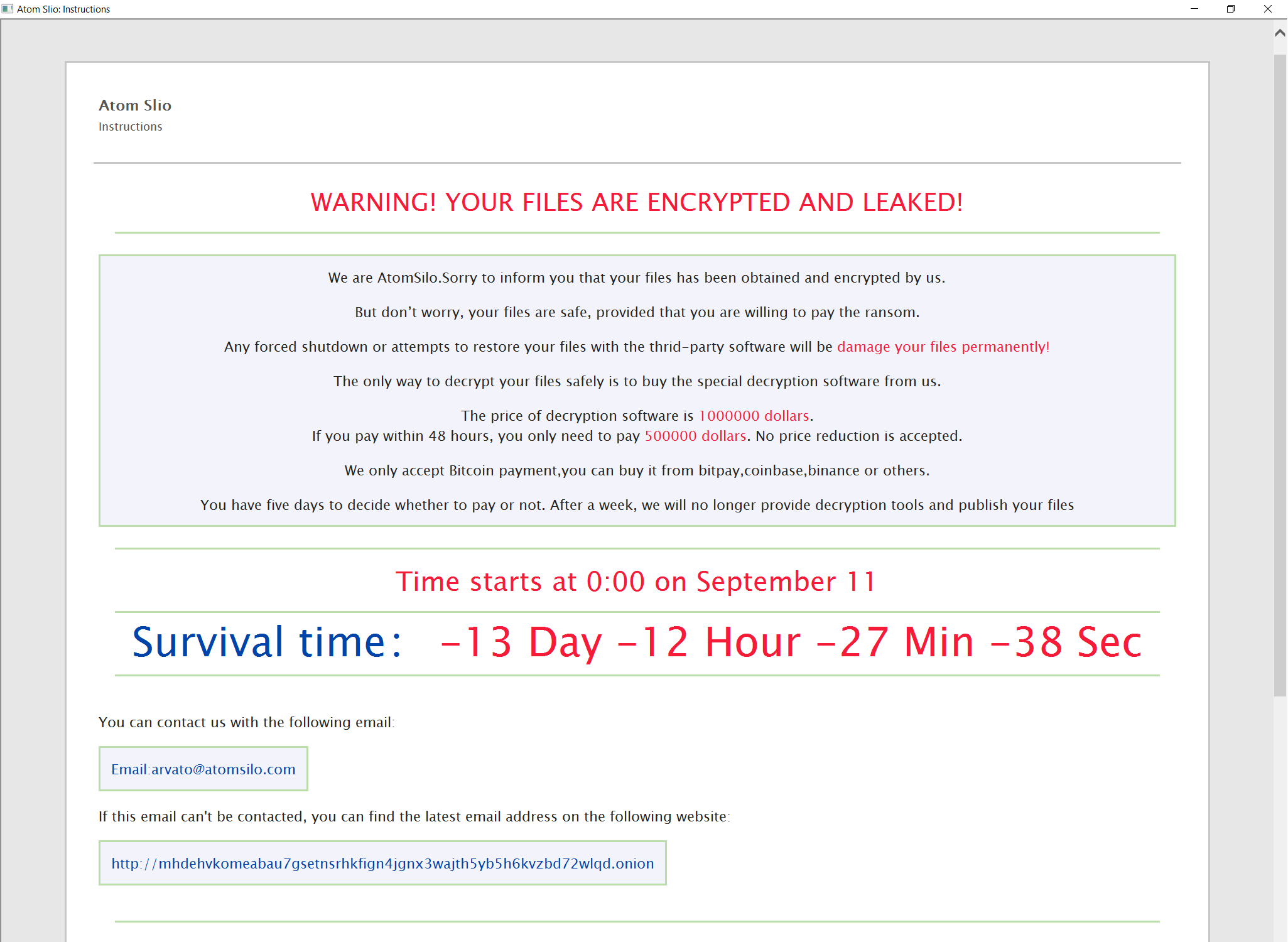
The SonicWall Capture Labs threat research team has observed a continued increase in ransomware used in double extortion schemes. The operators of ransomware known as AtomSilo have recently infiltrated a Brazilian pharmaceutical company. The malware installed has encrypted their files and obtained 900GB of very sensitive scientific data and even immigration and contact information of its employees. A $500,000 ransom is offered for 48 hours. After this, the ransom is increased to $1M in Bitcoin. Failure to pay will result in the sensitive data being released to the public.
Infection Cycle:
Upon infection of the ransomware component, files on the system are encrypted. Each encrypted file is given a “.ATOMSILO” file extension.
After encryption, the following message is brought up on the infected machine’s desktop:
The following files are dropped on to the system:
- README-FILE-{machine name}-{random 10 digit number}.hta (in directories with encrypted files)
The tOr web address (http://mhdehvkomeabau7gsetnsrhkfign4jgnx3wajth5yb5h6kvzbd72wlqd.onion) leads to the following page that is hosted by the operators:
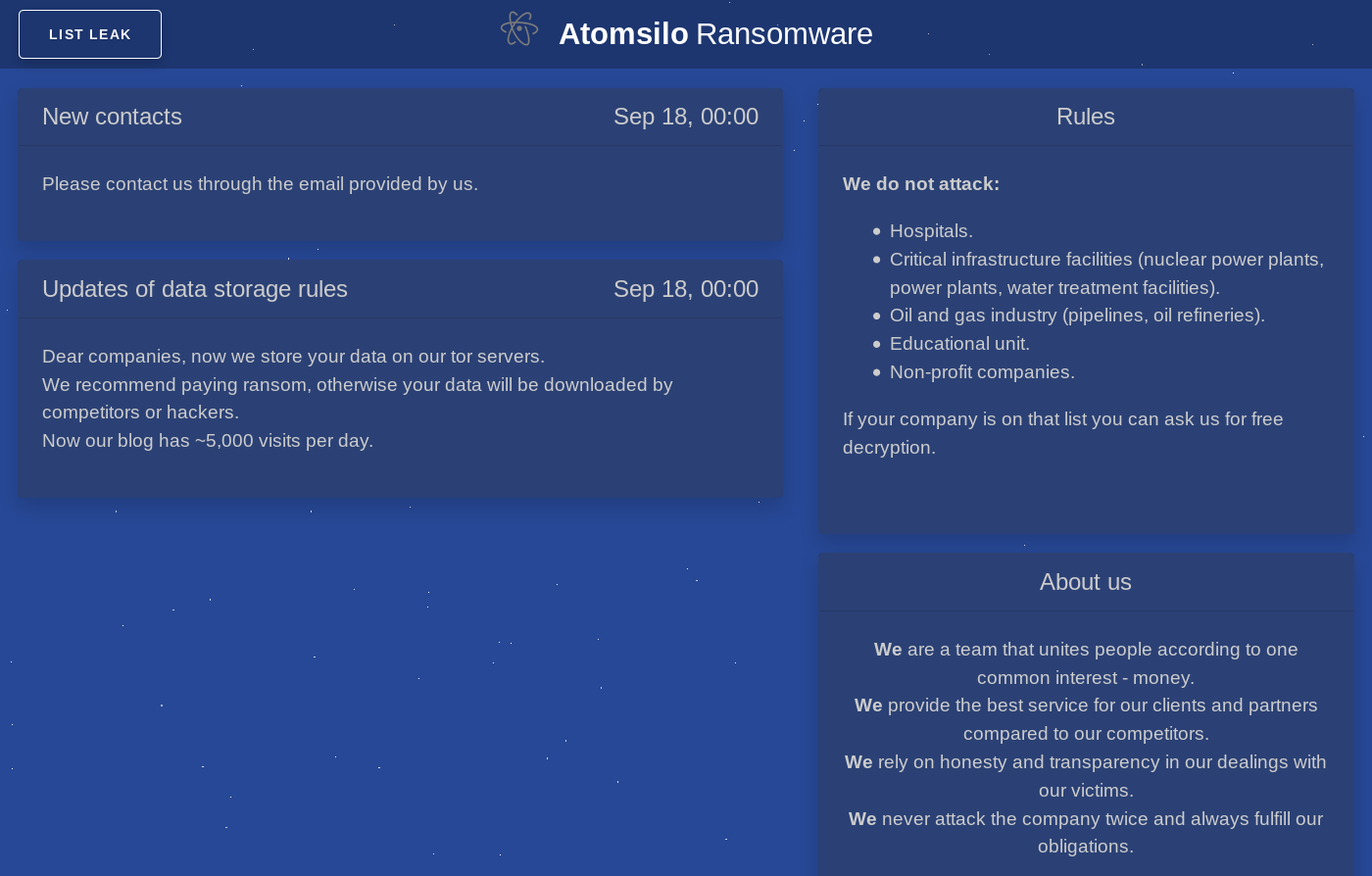
The “LIST LEAK” button shows a company that is in the process of being extorted by the operators:
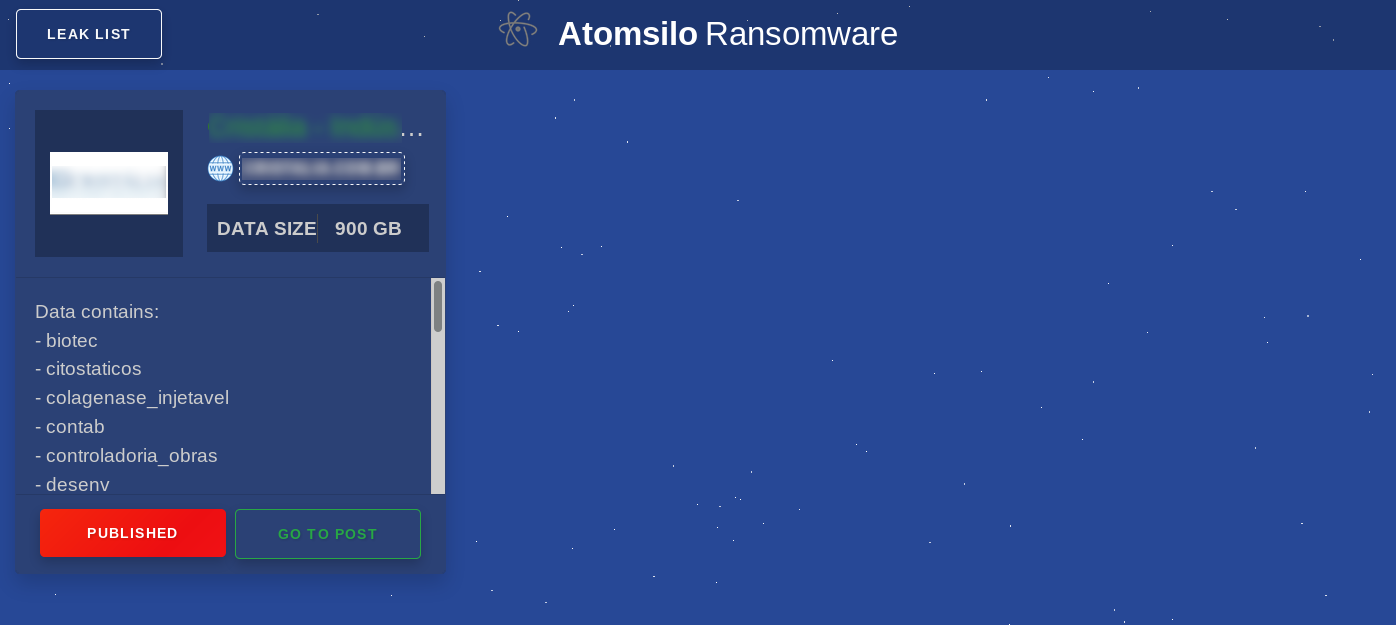
The “GO TO POST” button brings up a page that shows a summary of the data that has been obtained by the attackers:
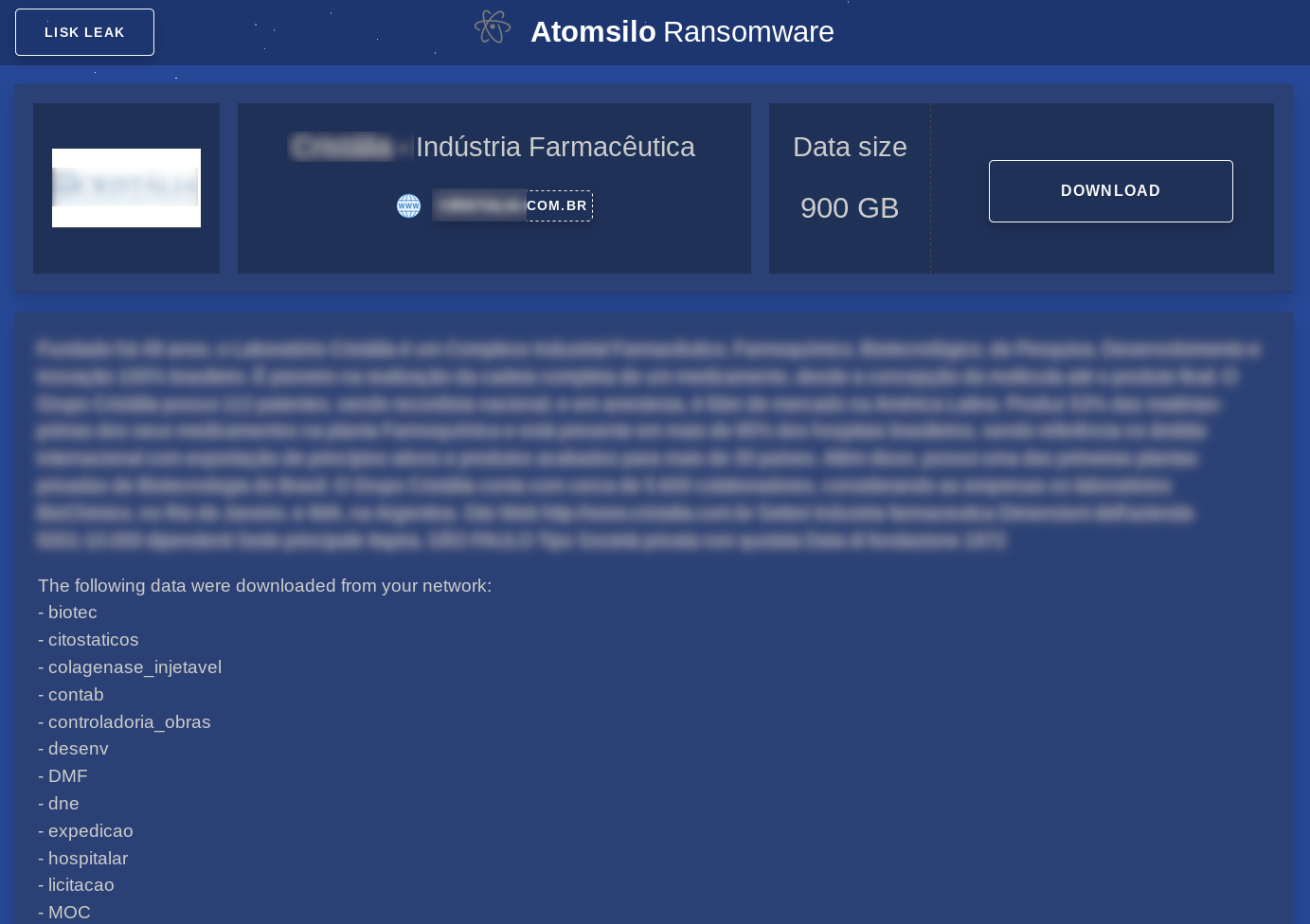
This page is very long and contains samples of the sensitive data that has been obtained:

The leak also includes company financial data and employee contact information:

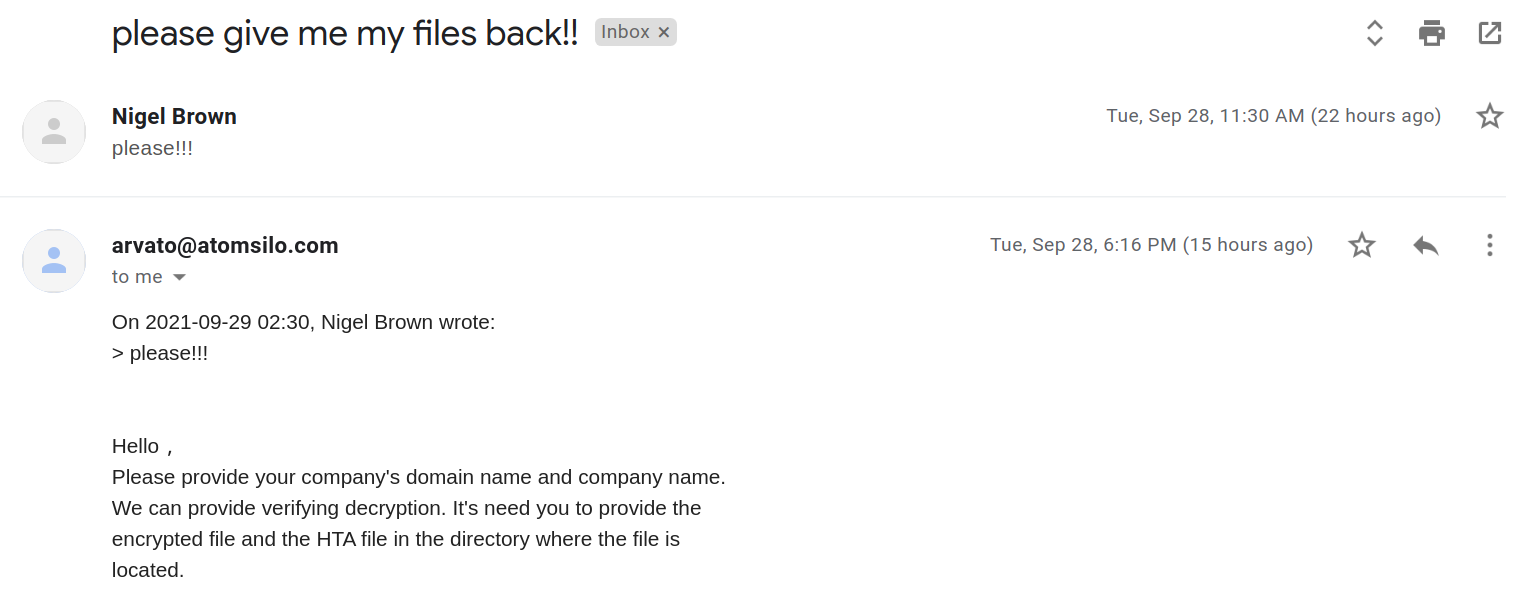
We reached out to the email address (arvato@atomsilo.com) provided in the ransom note and received the following response:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: AtomSilo.A (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.





