Spammers piggybacking on the Kaseya server exploit
The recent Kaseya VSA server exploit incident has given an opportunity for cybercriminals to distribute fake Kaseya update programs. An unsuspecting user is tricked to downloading a program that appears to be from Kaseya but in fact runs malware.
Infection Cycle:
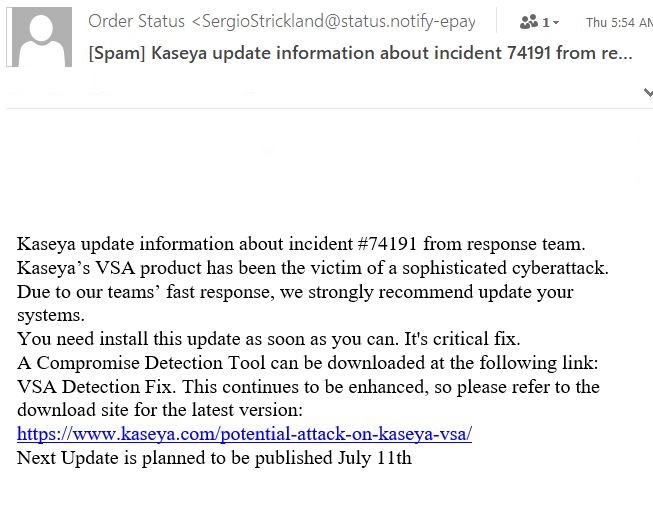
This Trojan arrives via a spam campaign. A user might receive an email similar to this screenshot below:
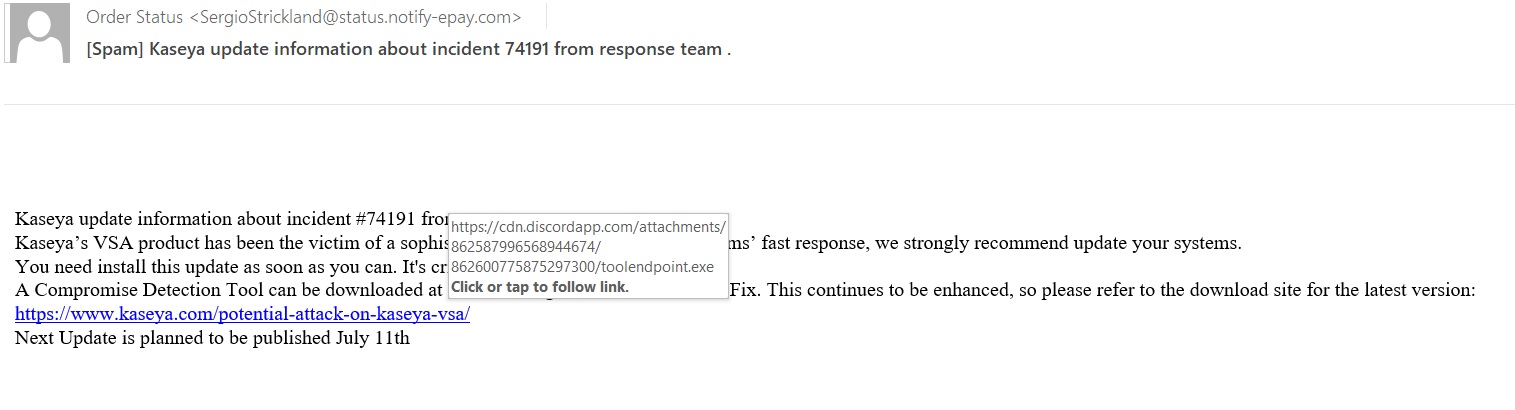
It purports to be coming from Kaseya’s “response team” with a download link to a tool that is a “critical fix” for the recently reported issue. The tool appears to be hosted on the legitimate Kaseya.com website but clicking on the link takes you to a different URL. Discord has been a popular choice for hosting malicious payloads lately.
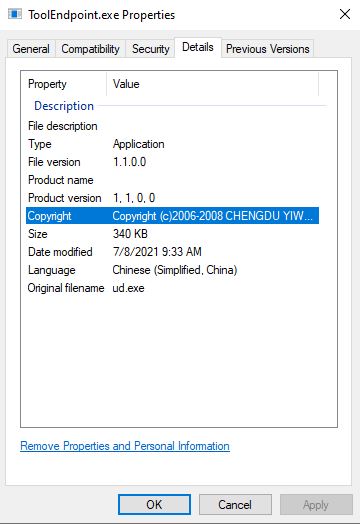
The malware uses a legitimate sounding filename, but this particular sample has the following file properties
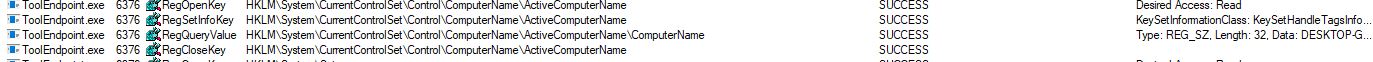
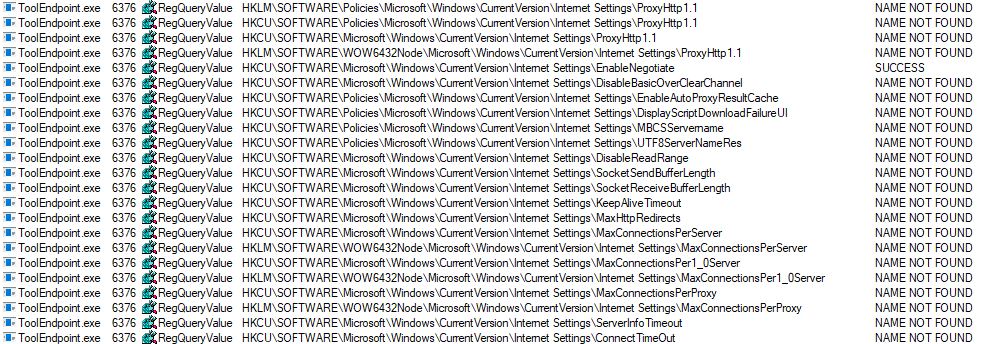
Upon execution, the malware goes through the registry and appears to be scoping the system looking through system policies and services. Many are very specific that were not found in our test system.
It then goes on to download another file.
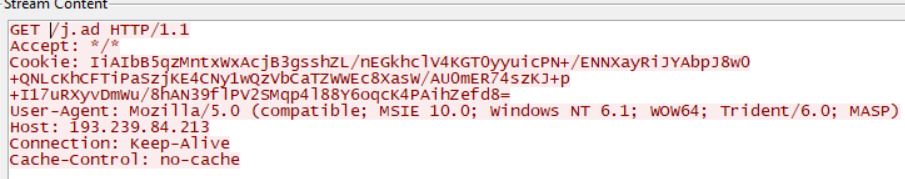
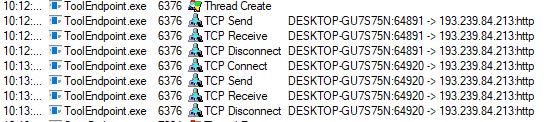
And then intermittently just keeps connecting to a remote server.
Since there isn’t an official fix from Kaseya yet, some users might fall for this in an attempt to protect their networks from being a target of a possible attack. Kaseya has issued a statement regarding this to remind their customers to not click on any link if they are not certain of the source.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Malagent.FT (Trojan)
This threat is also detected by SonicWall Capture ATP with Real-Time Deep Memory Inspection (RTDMI) and the Capture Client endpoint solutions.