3S Smart Software Solutions CoDeSys Vulnerability
Overview:
3S Smart Software Solutions CoDeSys is an IEC 61131-compliant PLC program development environment for multiple programming languages. CoDeSys supports PLC devices from over 250 device manufacturers. The CoDeSys Gateway Server is a service which facilitates enumeration, programming and interaction over TCP with devices, which themselves do not feature network connectivity.
A stack buffer overflow vulnerability exists in 3S Smart Software CoDeSys. The vulnerability is due to insufficient boundary checking when parsing requests and allows overflowing a stack buffer with an overly long string.
A remote unauthenticated attacker could exploit this vulnerability by sending crafted requests to the vulnerable service on ports 1211/TCP and 1210/TCP. Successful exploitation could result in code execution with SYSTEM privileges. Unsuccessful attack attempts could cause the affected service to terminate abnormally, causing a denial of service (DoS) condition.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2012-4708.
Common Vulnerability Scoring System (CVSS):
Base score is 10.0 (AV:N/AC:L/Au:N/C:C/I:C/A:C), based on the following metrics:
• Access vector is network.
• Level of authentication required is none.
• Impact of this vulnerability on data confidentiality is complete.
• Impact of this vulnerability on data integrity is complete.
• Impact of this vulnerability on data availability is complete.
Temporal score is 7.4 (E:U/RL:OF/RC:C), based on the following metrics:
• The exploitability level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
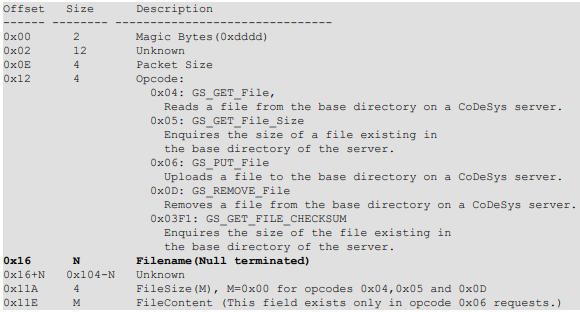
While the IEC 61131 specification is not publicly available, The following general structure of the file service related requests are (Opcodes 0x04,0x06 and 0x03F1), sent to the Gateway Server over the ports TCP/1211 and TCP/1210:
All multi-byte integers are in little-endian byte order.
An opcode 0x06 request, GS_PUT_File, can be used to upload a file to the base directory on a CoDeSys server. The contents of the file is sent in the FileContent field of an opcode 0x06 request. If the request is for a Filename that already exists on the server, the contents of the existing file will be replaced by the new contents sent within the request.
A stack buffer overflow vulnerability exists in 3S CoDeSys Gateway Server. The vulnerability is due to insufficient validation of the length of the Filename string within opcode 0x04, 0x06 and 0x03F1 requests. The vulnerable code appends the user-controlled Filename to the base directory string “C:\WINDOWS\Gateway Files” and then copies the whole path string to a one of the three size stack buffers. Depending on the opcode of the request, the vulnerable code uses a stack buffer with the following sizes:
• 0x1c0 (448) bytes for the opcode 0x03F1.
• 0x128 (296) bytes for the opcode 0x06.
• 0x210 (528) bytes for the opcode 0x04.
The vulnerable function uses 36 (0x24) bytes of the allocated space for other purposes. Providing an overly long Filename overflows the stack buffer overwriting other data on the stack, including the return address and the SEH.
A remote, unauthenticated attacker can exploit this vulnerability by sending a malicious opcode 0x04, 0x06 and 0x03F1 request to a vulnerable server. Successful exploitation would allow the attacker to execute arbitrary code in the security context of the affected service, which is SYSTEM. If the attack fails, the service may terminate abnormally, leading to a denial-of-service condition.
Triggering the Problem:
The target host must have the vulnerable version of the software installed and running.
• The attacker must have network connectivity to the target server.
Triggering Conditions:
An attacker connects to the server and sends a crafted request containing a malicious Filename to the target host. The vulnerability is triggered when the affected product parses the malicious request.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• 3S Smart Software Solutions CoDeSys Gateway Server Protocol, over port 1210/TCP
• 3S Smart Software Solutions CoDeSys Gateway Server Protocol, over port 1211/TCP
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 4888 CODESYS Gateway Server Buffer Overflow 1
Remediation Details:
Listed below are a number of actions that may be taken in order to minimize or eliminate the risks:
• Upgrade to a non-vulnerable version of the product.
• Restrict network access to the vulnerable ports to trusted hosts only.
• Filter attack traffic using the IPS signature above.
The vendor has released a security patch that mitigates this vulnerability (requires customer login):
Vendor Advisory