Lotus ransomware charges 1 BTC ($49K USD). Multi PC discount possible
The SonicWall Capture Labs threat research team has observed reports of a variant from the Crysis/Dharma ransomware family called Lotus. The operators of this malware charge 1 BTC ($49K USD at the time of writing this alert) for file recovery. However, the price appears to be negotiable after a conversation with the malware operator.
Infection Cycle:
Upon infection, the malware can be seen using the built-in mshta program to display the ransom message:
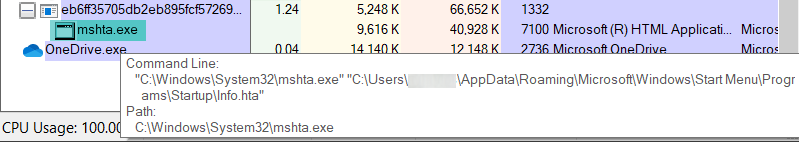
Files on the system are encrypted and the following extension is appended to their file names:
.id-E625BDD2.[paymei@cock.li].LOTUS
The following ransom message is displayed on the desktop:
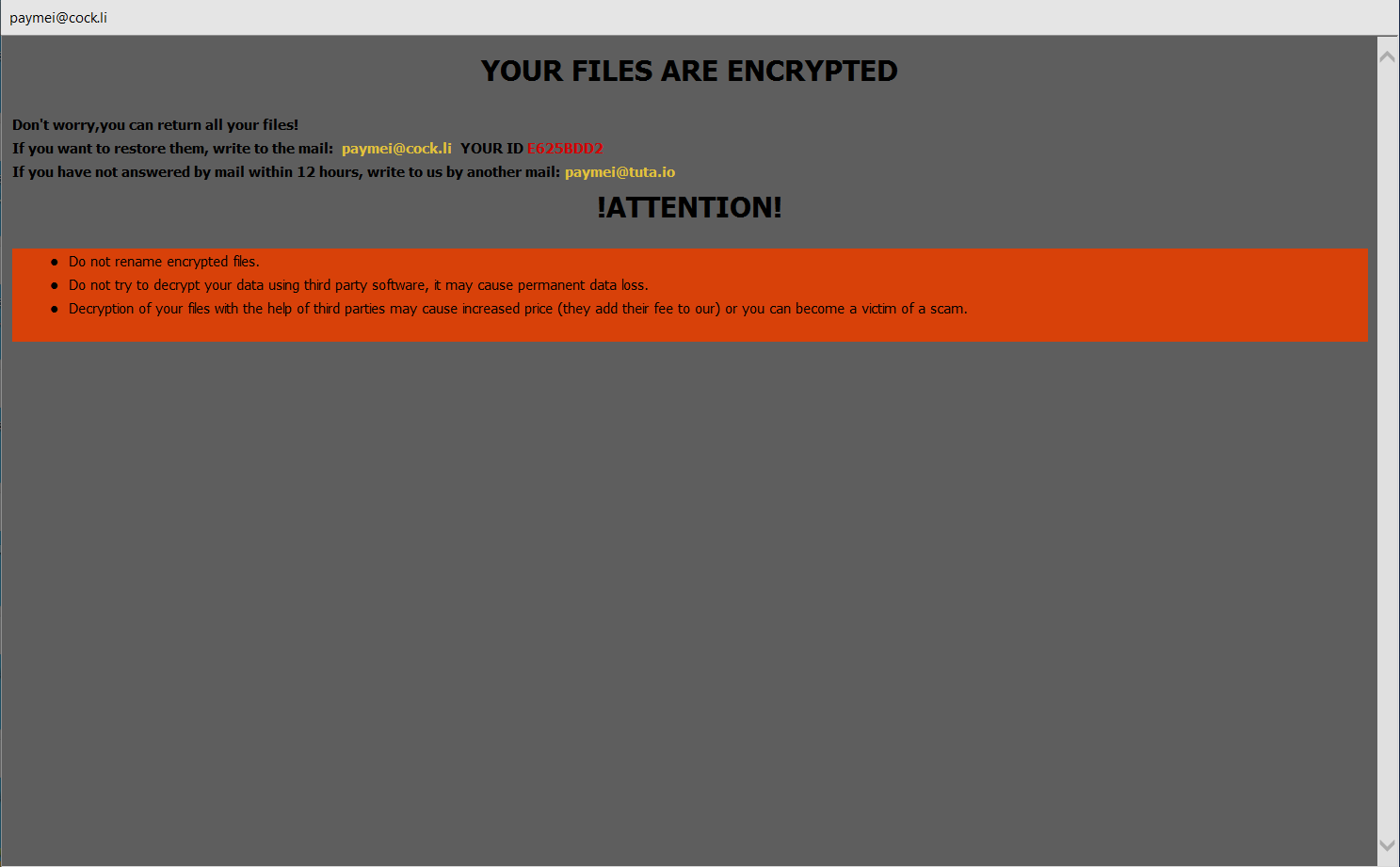
The following files are dropped on to the system:
- MANUAL.txt (in every directory containing encrypted files)
- %APPDATA%\Roaming\{original malware file name} [Detected as: GAV: Lotus.RSM (Trojan)]
- %APPDATA%\Roaming\Info.hta (contains message shown above)
- %APPDATA%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Info.hta (contains message shown above)
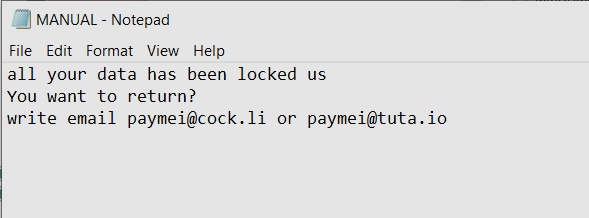
MANUAL.txt contains the following text:
We reached out to the supplied emails and had the following conversation with the ransomware operator:
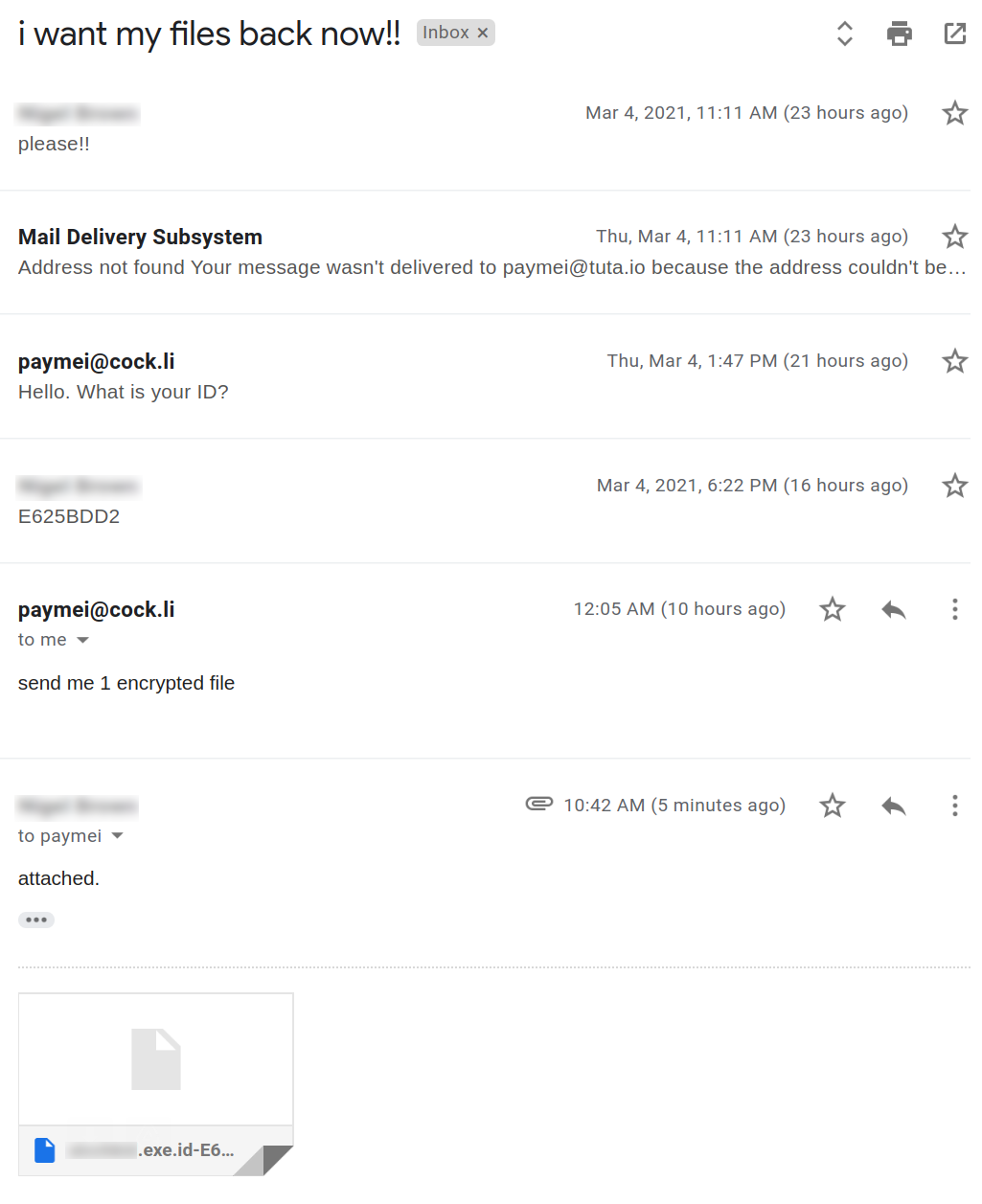
The operator asks how many pc’s we would like to recover. This leads us to believe that the malware is aimed at large organizations:
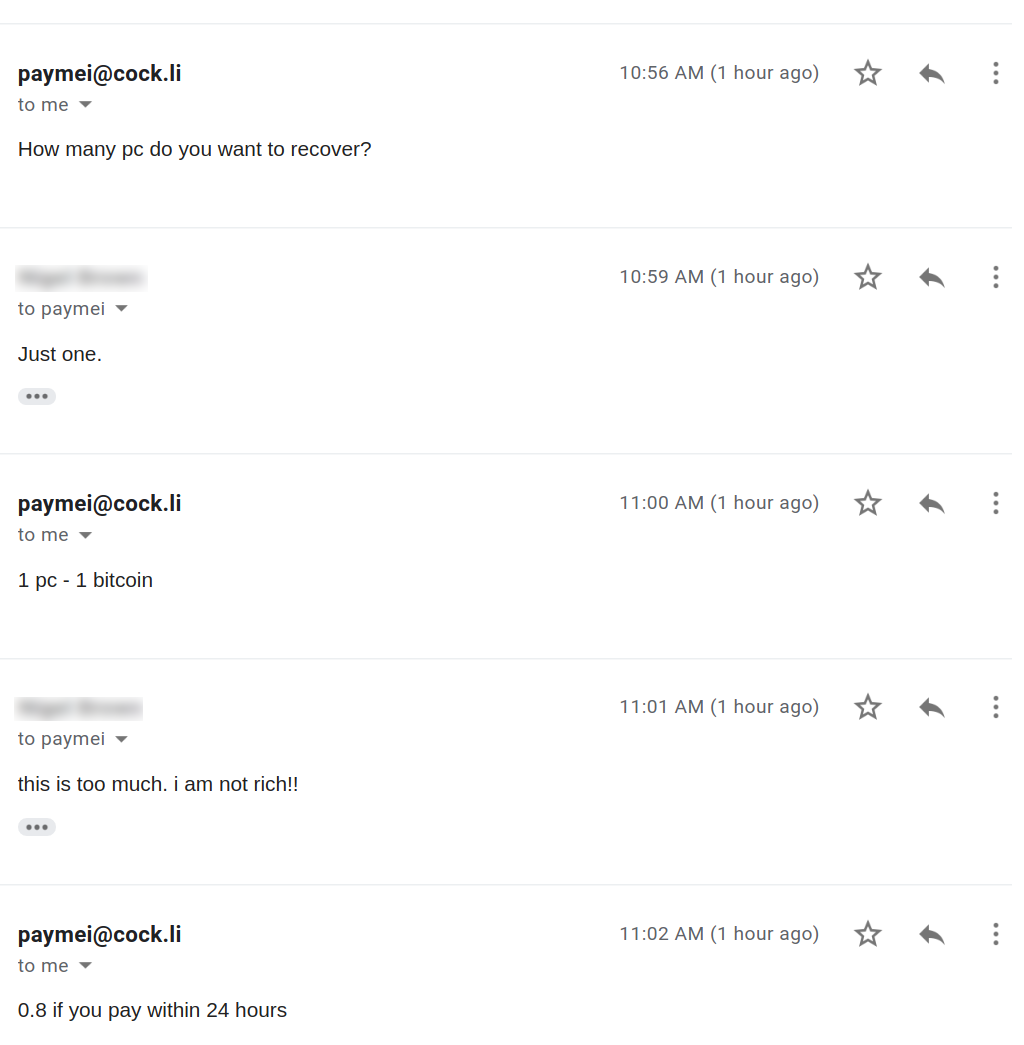
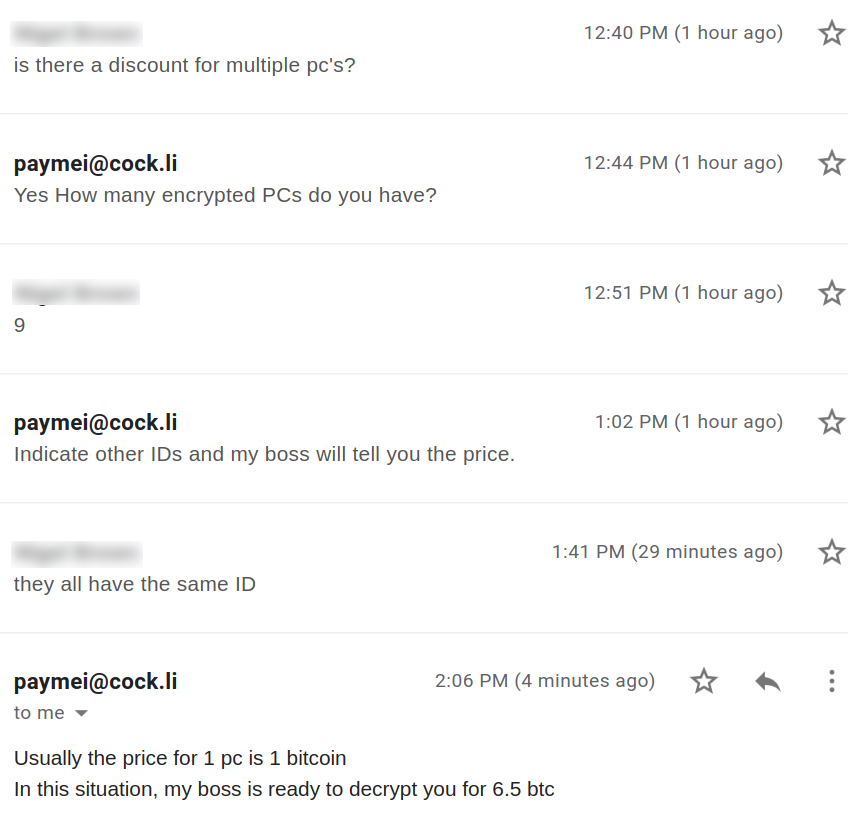
We see if we can negotiate further if we have multiple infected PC’s:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Lotus.RSM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.



