China’s “Winnti” Spyder Module
Overview:
SonicWall’s Capture Labs Threat Research Team, recently captured and evaluated a new malicious sample termed Spyder, from China’s “Winnti” hacking group. This backdoor is written in C++ and designed to run on 64-bit Windows. This module is being used for targeted attacks on information storage systems, collecting information about corrupted devices, executing mischievous payloads, coordinating script execution, and C&C server communication. The module is loaded by the MSDTC system service using a well-known DLL Hijacking method. The function names within the modules export table are related to the exported functions of the apphelp.dll system library.
Static Information & Error Checking Information:
Dynamic Information:
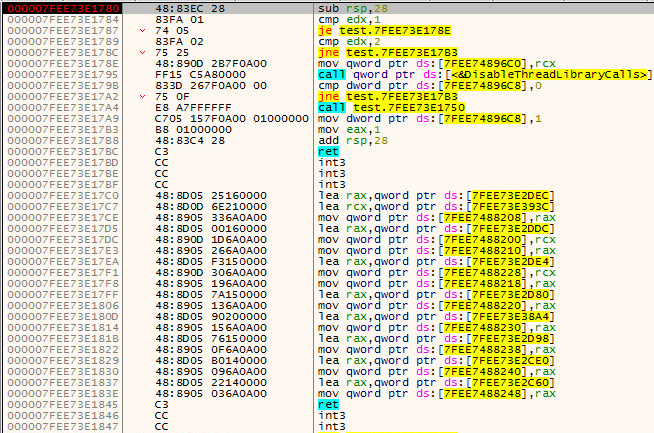
Dll Main inside x64 debug:
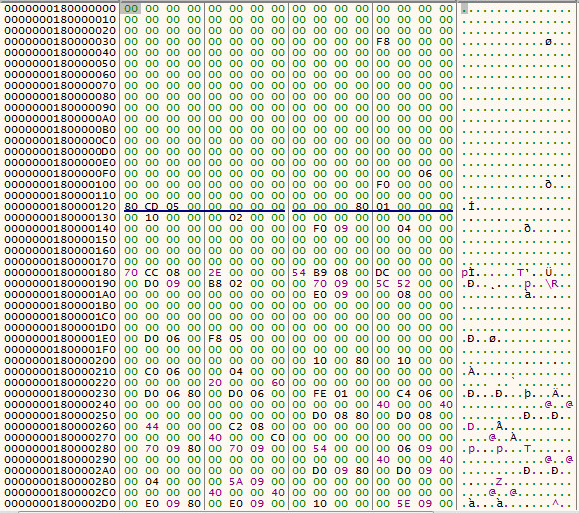
Encrypted PE File in memory:
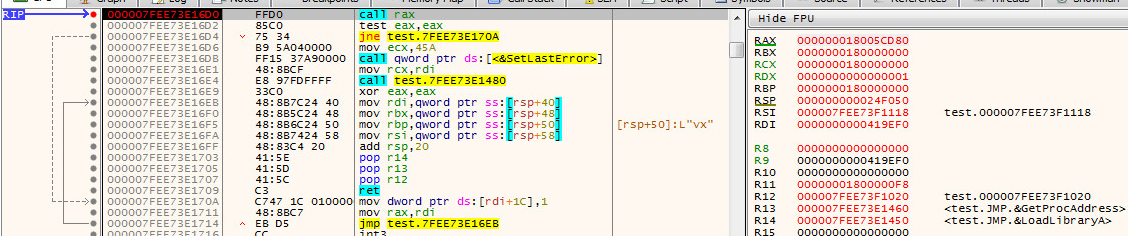
Call to Shellcode see RAX:
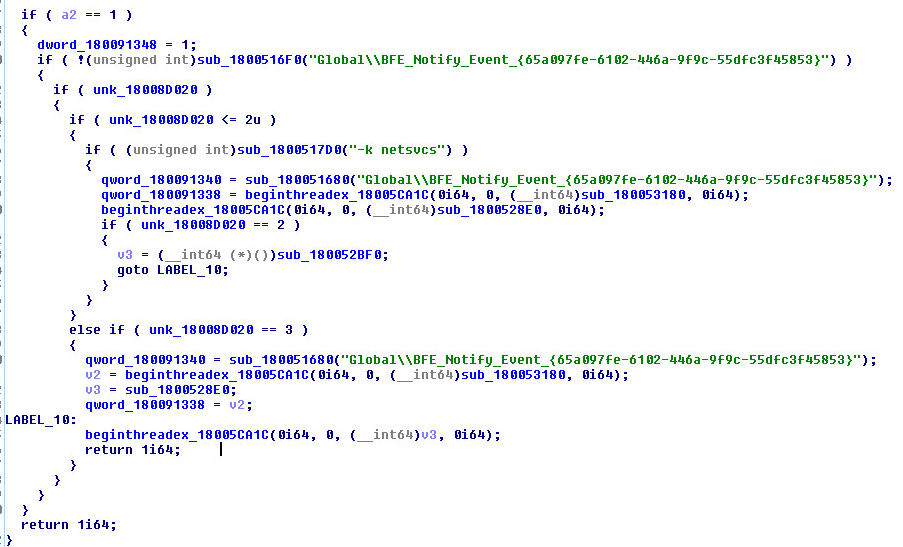
Dll Main inside Encrypted PE File:
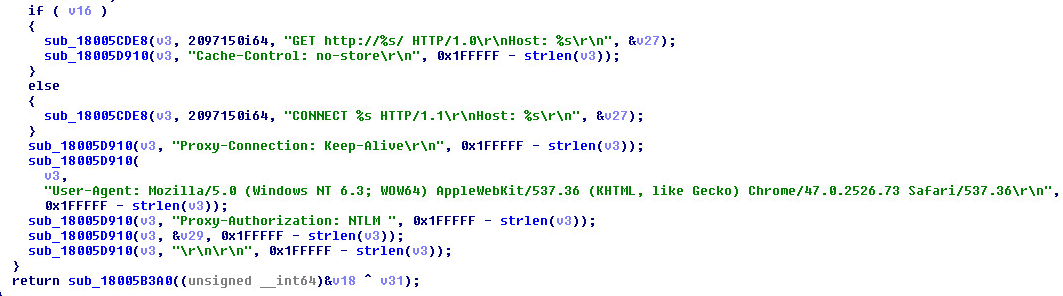
Network Artifacts:
Get Request:
Possible domains in the wild:
- sidc.everywebsite.us
- snoc.hostingupdate.club
- wntc.livehost.live
- hccadkml89.dnslookup.services
- koran.junlper.com
- nted.tg9f6zwkx.icu
- sidcfpprx14.in.ril.com
- sidcfpprx01.in.ril.com
- sidcfpprx25.in.ril.com
- sidcfpprx10.in.ril.com
Supported Systems:
- Windows 10
- Windows 8.1
- Windows 8.0
- Windows 7
- Windows Vista
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: Spyder.DN (Trojan)
Appendix:
Sample SHA-1 Hash: 41777d592dd91e7fb2a1561aff018c452eb32c28