8t_Dropper, RoyalRoad
Overview:
SonicWall Capture Labs Threat Research Team recently found a new sample for 8t_Dropper aka RoyalRoad. Royal Road is a tool shared by many targeted attack groups believed to belong to China. The sample below locates and downloads passwords using SQL queries into your current browsers stored database. (Google Chrome, Firefox, Thunderbird)
Threat Actor(s) Involved: Hellsing, Ice Fog, Pirate Panda, RANCOR, TA428, Tick, Tonto Team, Karma Panda
MITRE ATT&CK Information:
ID: T1055
Sub-techniques: T1055.001, T1055.002, T1055.003, T1055.004, T1055.005, T1055.008, T1055.009, T1055.011, T1055.012, T1055.013, T1055.014
Tactics: Defense Evasion, Privilege Escalation
Platforms: Linux, Windows, macOS
Data Sources: API monitoring, DLL monitoring, File monitoring, Named Pipes, Process monitoring
Defense Bypassed: Anti-virus, Application control
CAPEC ID: CAPEC-640
Sample, Static Information:
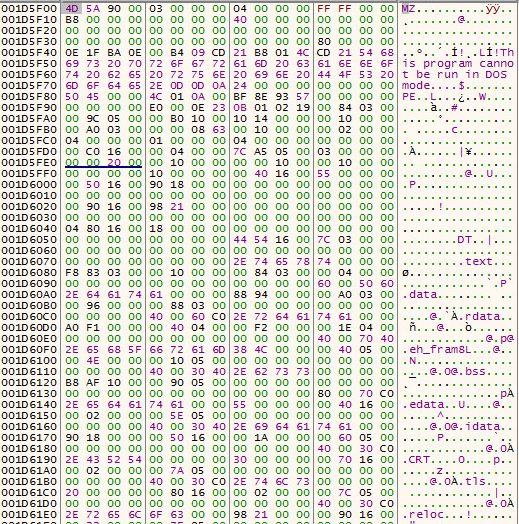
Checking for a valid PE File, red highlights will form within each PE member, if invalid data is found within the PE File. This sample passes, this check.
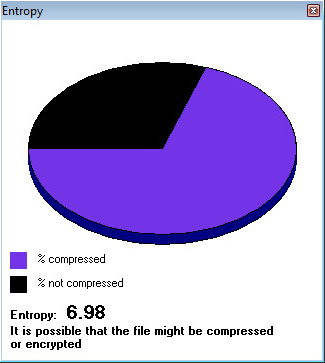
Entropy of sample:
First Stage, Dropper, Dynamic Information:
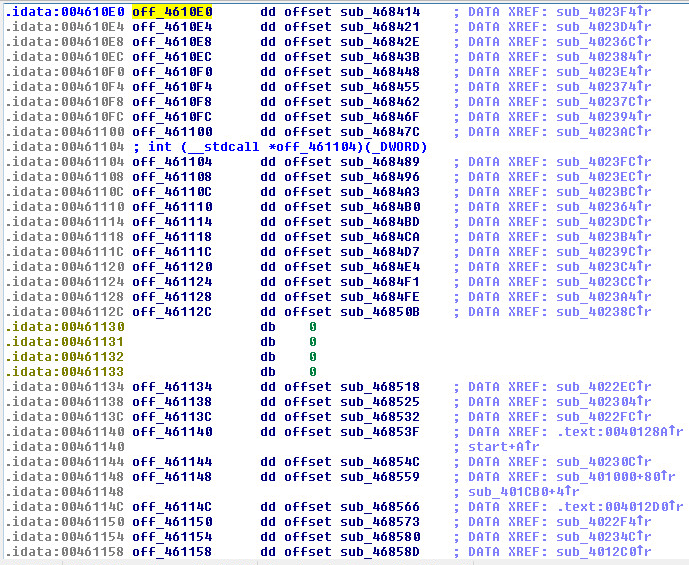
A List/Table of the shell coders function calls in IDA Pro, disassembled:
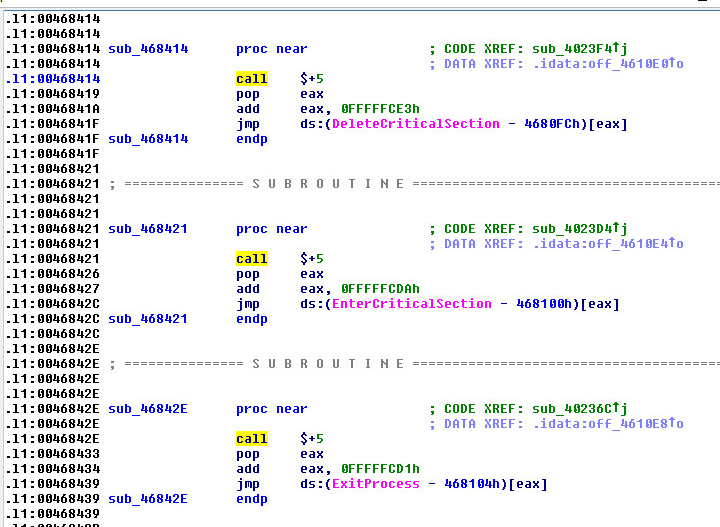
This trick is used a lot in malware, (Call+5), disassembled:
Shellcode Function Calls Disassembled in x32 Debug:
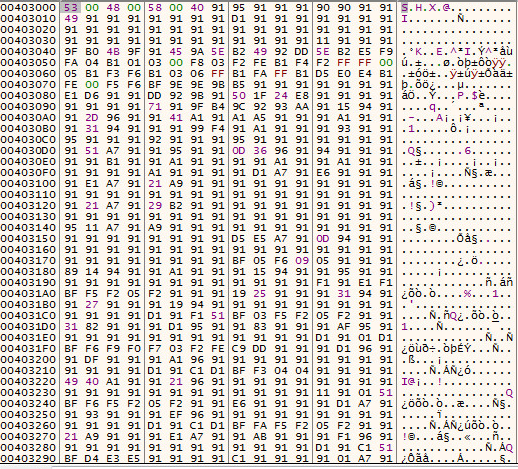
Encrypted Buffer:
Decrypted Buffer:
Dropped DLL:
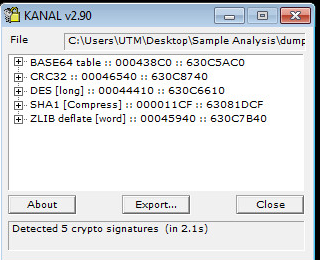
Encryption used in DLL:
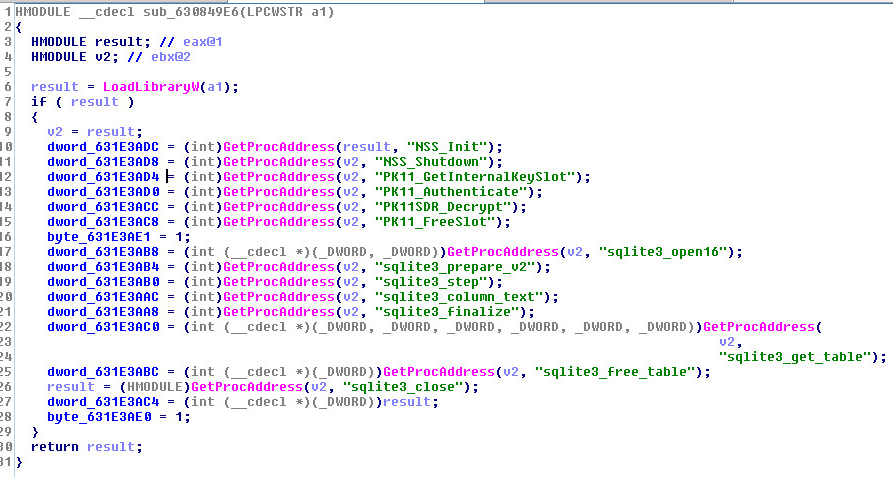
NSS Info:
NSS Overview:
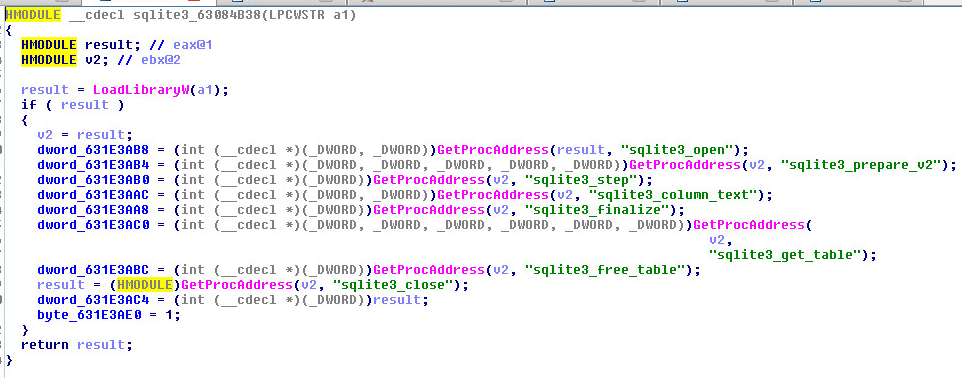
NSS Decompiled
SQL Functions Decompiled:
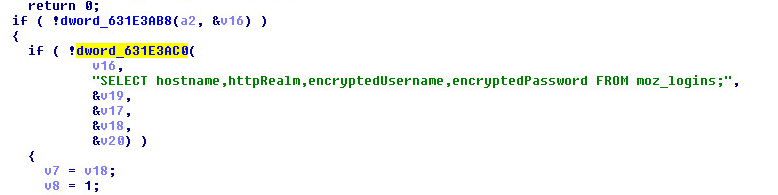
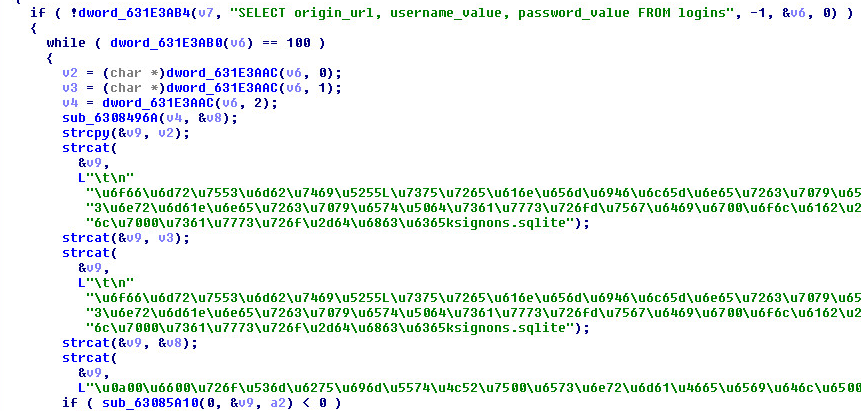
(SQL Query) – Thunderbird Password Captures:
(SQL Query) – Google Chrome Password Captures:
Supported Systems:
- Windows 10
- Windows 8.1
- Windows 8.0
- Windows 7
- Windows Vista
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: 8t_Dropper.A (Trojan)
Appendix:
Sample SHA256 Hash: 859443a72a9a9f53e3810efbddc79c68a243fcba0c52957c0a37846384477133