Discord services misused to host malware including Android bankers
Discord is a digital distribution platform geared towards building communities. But malware authors are misusing this as a medium to host malicious applications, these hosted applications can be accessed and downloaded even without having an account on Discord.
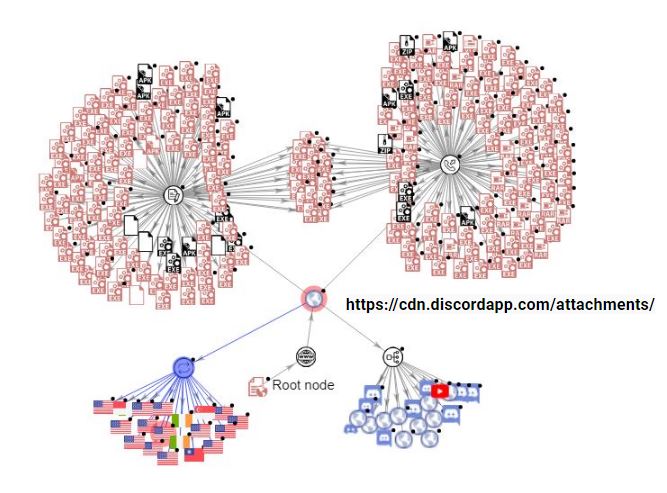
While investigating an Android banker, the Sonicwall Capture Labs Research team observed that it was hosted on Discord server cdn.discordapp.com. Further investigations revealed that this server is hosting/communicating (at the time of writing this blog) with a large number of malicious applications. We observed the following types of malicious apps in connection with this server:
- Android apks
- Executables
- Compresses RAR’s
Below is a Virustotal Graph for this observation:
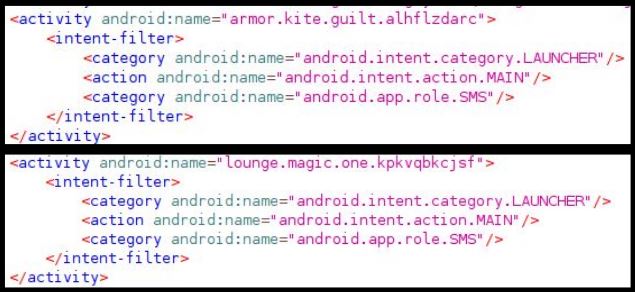
We analyzed few Android apps which share similar functionality and obfuscation measures designed to hide their true functionality from automated security scanners.
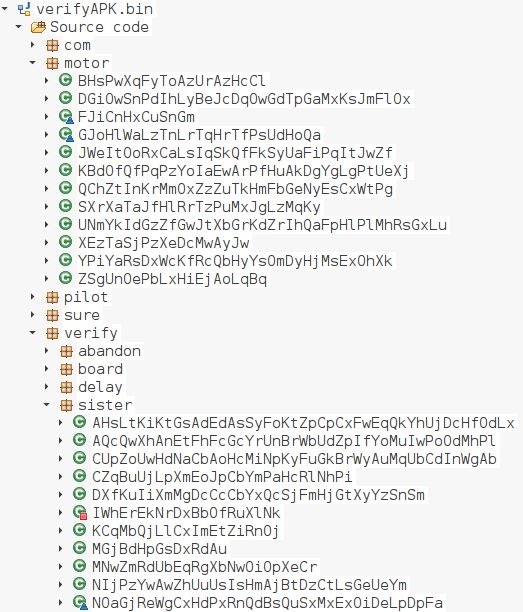
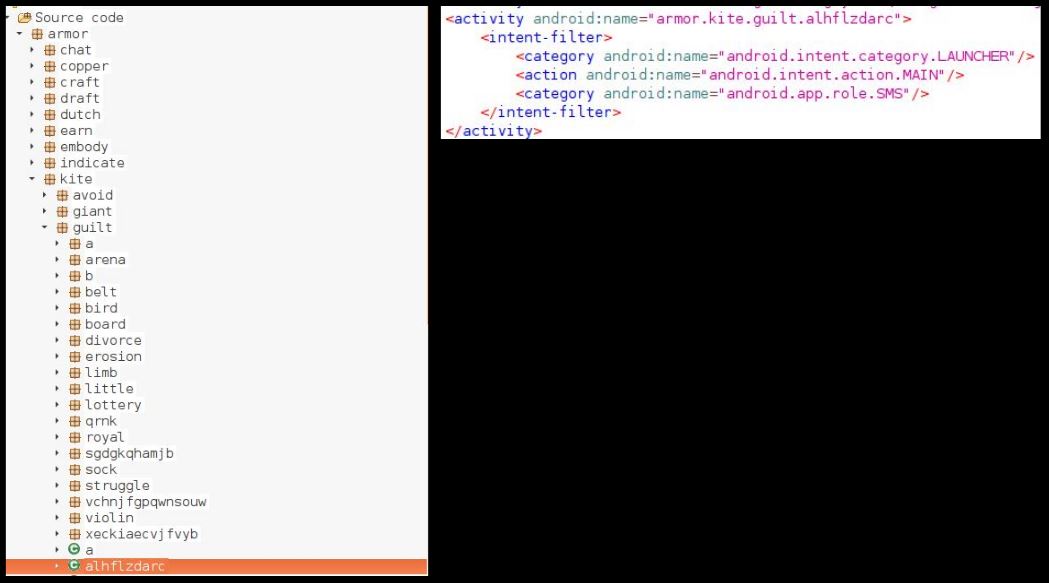
In both cases the Main activity mentioned in the AndroidManifest.xml file is not present in the decompiled code of the app. This indicates that most likely a separate dex file might be dropped on the system which contains decrypted code which gets invoked:
Upon execution the apps request for Accessibility Services, until the permission is granted the request screen keeps showing up intermittently:
The malware contains obfuscated code, not providing much information about its functionality:
However when the malware runs on the device, it drops a .json file in the FOLDERNAME. This is a .dex file in reality as indicated by the initial file header:
Upon renaming the file and opening it in a .dex file viewer like Jadx we can see readable code, there is junk code along with legible code. We can finally see the Main Activity class that is specified in the Manifest file which was previously unknown:
The malware is capable of accepting and executing the following commands:
- grabbing_lockpattern
- run_record_audio
- run_socks5
- update_inject
- stop_socks5
- rat_connect
- change_url_connect
- request_permission
- clean_cache
- change_url_recover
- send_mailing_sms
- run_admin_device
- access_notifications
- url
- ussd
- sms_mailing_phonebook
- get_data_logs
- get_all_permission
- grabbing_google_authenticator2
- notification
- grabbing_pass_gmail
- remove_app
- remove_bot
- send_sms
- run_app
- call_forward
- patch_update
This malware is yet another good example that shows the dangers of granting Accessibility Service to an application. If the permissions is not granted a malware may keep requesting for this permission, this is a tell-tale sign that something is not right.
Android malware occupies a small slice among the myriad malicious apps hosted on Discord. There have been conversations about malware being hosted on Discord for a while but the issue still appears to persist.
SonicWall Capture Labs provide protection against this threat with the following signatures:
- AndroidOS.Obfuscated.ST (Trojan)
- AndroidOS.Banker.CM (Trojan)
Indicators of Compromise (IOC’s):
- e8a0b4aa368473a5a0d1183fb79e127b
- 2e87bd0a77bfdf78ff50634b0ec1c7ae