Attackers actively targeting vulnerable Netgear DGN devices
SonicWall Capture Labs threat research team observed attacks exploiting an old vulnerability in Netgear DGN devices . Netgear produces networking hardware for consumers, businesses, and service providers. Netgear DGN are ADSL+ Modem Router that provide customers with an easy and secure way to set up a wireless home network with fast access to the Internet over a high-speed digital subscriber line.
Netgear DGN1000 and DGN2200 devices are prone to a remote authentication-bypass vulnerability. Remote attackers can exploit this issue to bypass the authentication mechanism and execute commands within the context of affected devices with elevated privileges.
NETGEAR DGN Devices Remote Command Execution Vulnerability
Below are some examples of exploits in the wild

The vulnerable device doesn’t check authentication for URLs containing the “currentsetting.htm” substring, so the following URL can be accessed without authentication.
http://<velnerable-device-ip>/setup.cgi?currentsetting.htm=1
The “setup.cgi” page can then be abused to execute arbitrary commands.
Lets take the following example
![]()
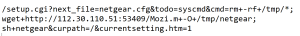
The URL leverages the “syscmd” function of the “setup.cgi” script to execute arbitrary commands. The attacker connects to malicious domain to downloads malicious file and saves it in the tmp directory to execute.
Following versions are vulnerable:
NetGear DGN1000 running firmware prior to version 1.1.00.48
Netgear DGN2200 v1
This vulnerability is patched.
SonicWall Capture Labs provides protection against this threat via following signature
IPS 13034: NETGEAR DGN Devices Remote Command Execution
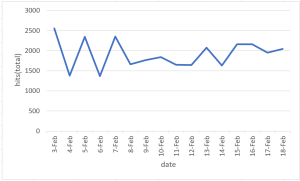
Threat Graph
Signature hits for 13034 for past week.
IoCs
112.30.110.51
113.118.133.39
115.50.245.72
117.242.208.60
119.123.239.63
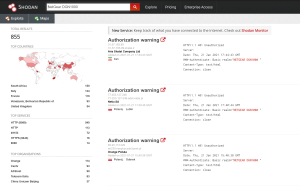
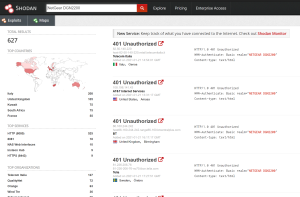
Quick check on shodan shows vulnerable devices