Ransomware spares no one except if you are from Russia, Kazakhstan or Ukraine
The Sonicwall Capture Labs Research team has observed another ransomware being circulated in the wild recently. It was first spotted earlier this year but has not gained much traction then. Interestingly, this not so popular ransomware promises to decrypt your files if you are from Russia, Kazakhstan or Ukraine and does not impose a time limit on when victims can send payment to decrypt files.
Infection Cycle:
Erica ransomware comes as an executable that use the following icons:
![]()
Upon execution, it connects to a remote server 178.170.219.108.
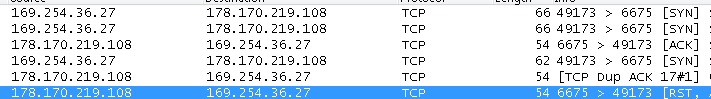
It spawns a legitimate file to carry out its malicious functionality. During our analysis it used cvtres.exe, a Microsoft Windows file which is part of the C++ tool chain. (See more details here).
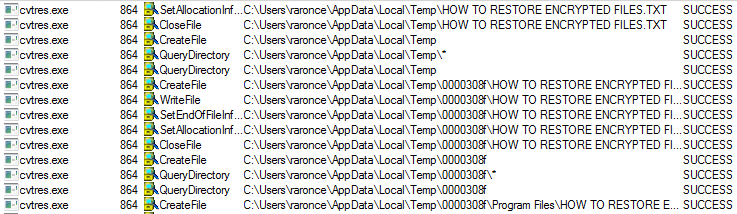
Cvtres.exe then encrypts the victim’s files and appends random characters to the file’s original name.
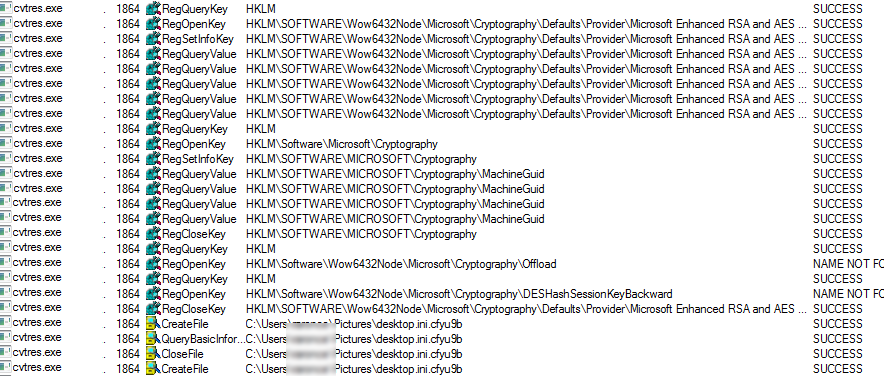
This ransomware uses the Microsoft Enhanced RSA and AES Cryptographic Provider to create keys and encrypt data using the RSA algorithms.
It then zips up the entire %users% directory and names it with a random name. This is then sent out to a remote server.
![]()
A ransom note is created in every directory with which files have been encrypted. They promise to help with decryption if you are from Russia, Kazakhstan or Ukraine. And also do not impose a time limit on when you decide to pay to decrypt your files.
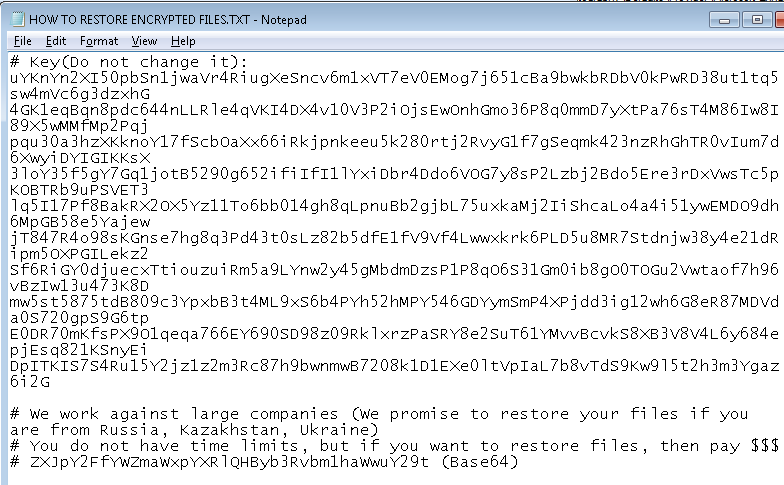
An email is included in the note but is base64 encoded and reads:
erica_affiliate @ protonmail.com
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Erica.RSM (Trojan)
- GAV: Erica.RSM_1 (Trojan)
- GAV: Erica.RSM_2 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.



