test
The SonicWall Capture Labs threat research team have observed reports of spam inviting people to view an “image” in which they are supposedly present. The “image”, which in our case was named IMG148150.jpg.js is actually a file containing malicious Javascript downloader code. Once executed, Avaddon is downloaded and run in the background.
Infection Cycle:
IMG148150.jpg.js contains the following script:
Upon running the script, sava.exe is downloaded from hxxp://217.8.117.63/sava.exe and executed. It displays the following message on the desktop background:
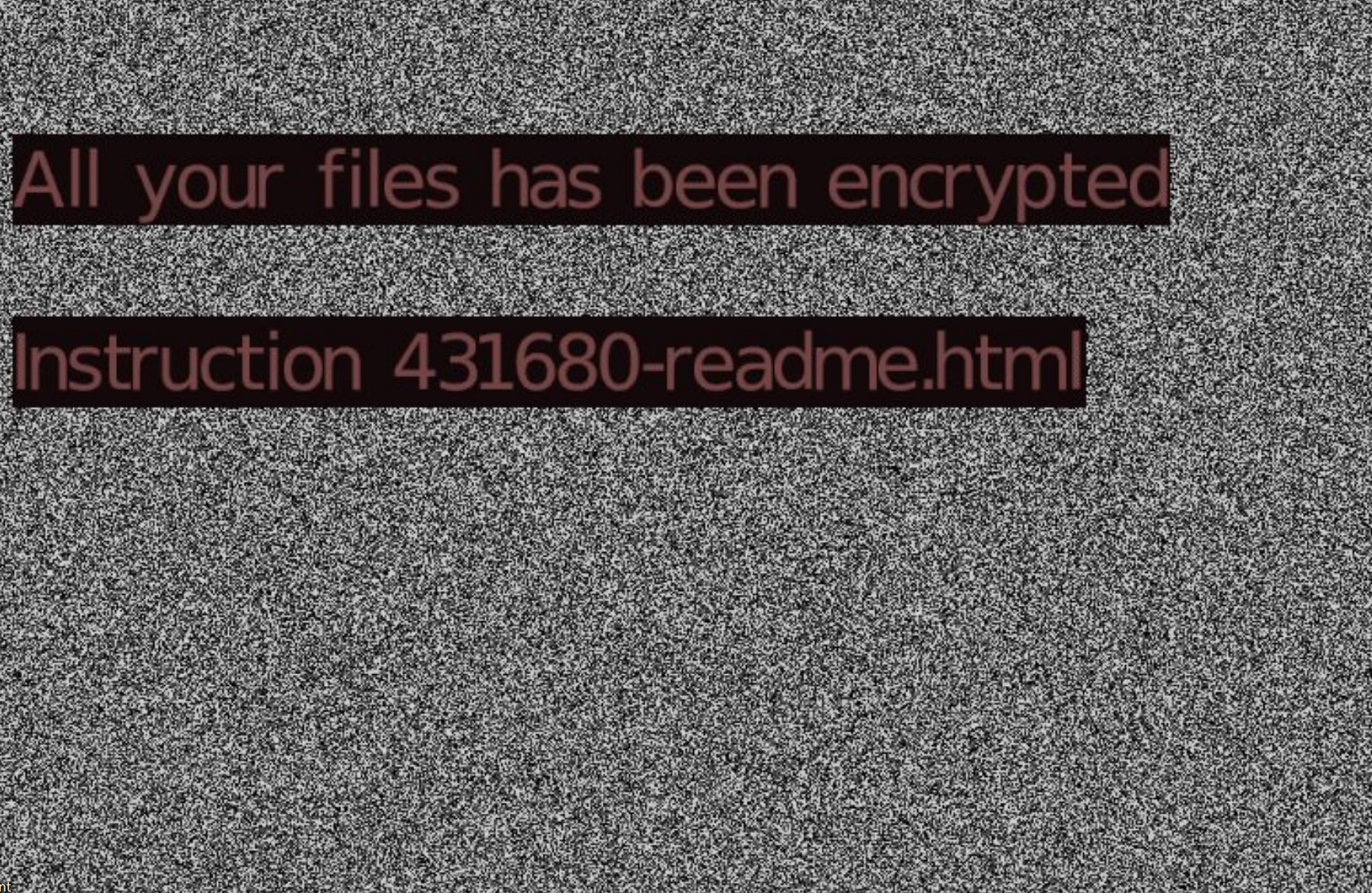
The following command is run to remove shadow copies on the system:
wmic.exe SHADOWCOPY /nointeractive and vssadmin.exe Delete Shadows /All /Quiet
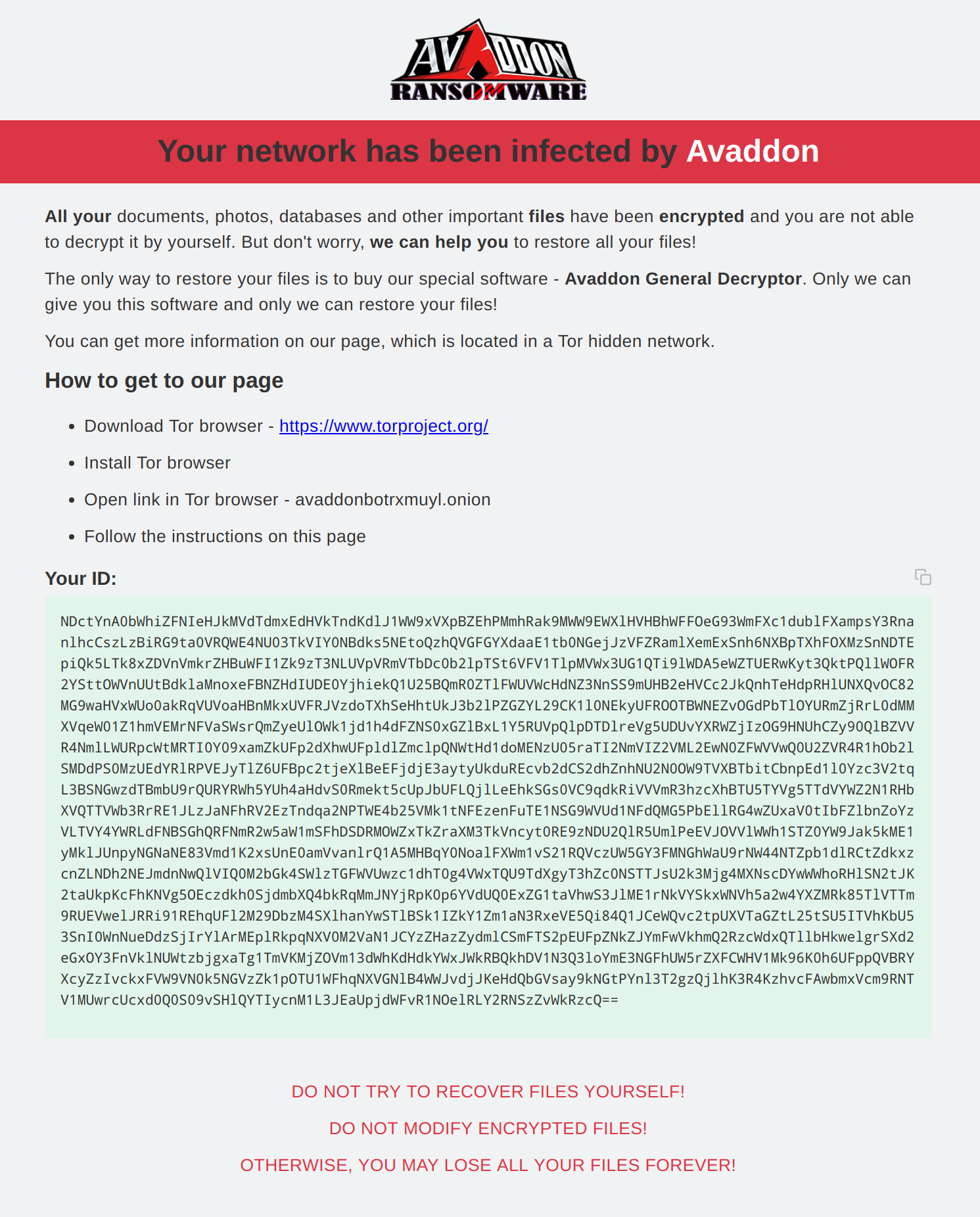
Files on the system are then encrypted by the malware. 431680-readme.html is copied into all directories containing encrypted files. 431680-readme.html contains the following page:
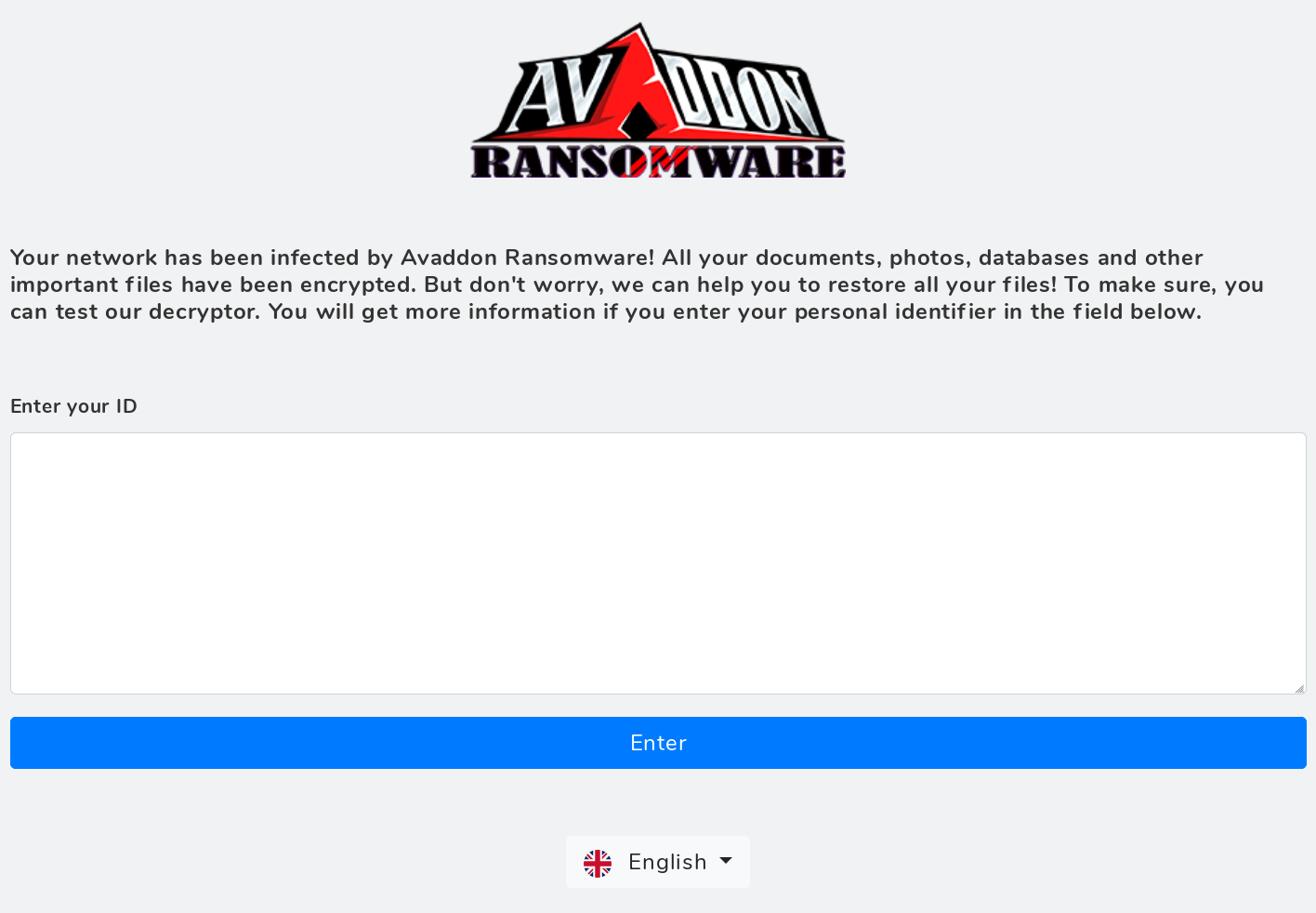
avaddonbotrxmuyl.onion leads to the following page hosted on the tOr network:
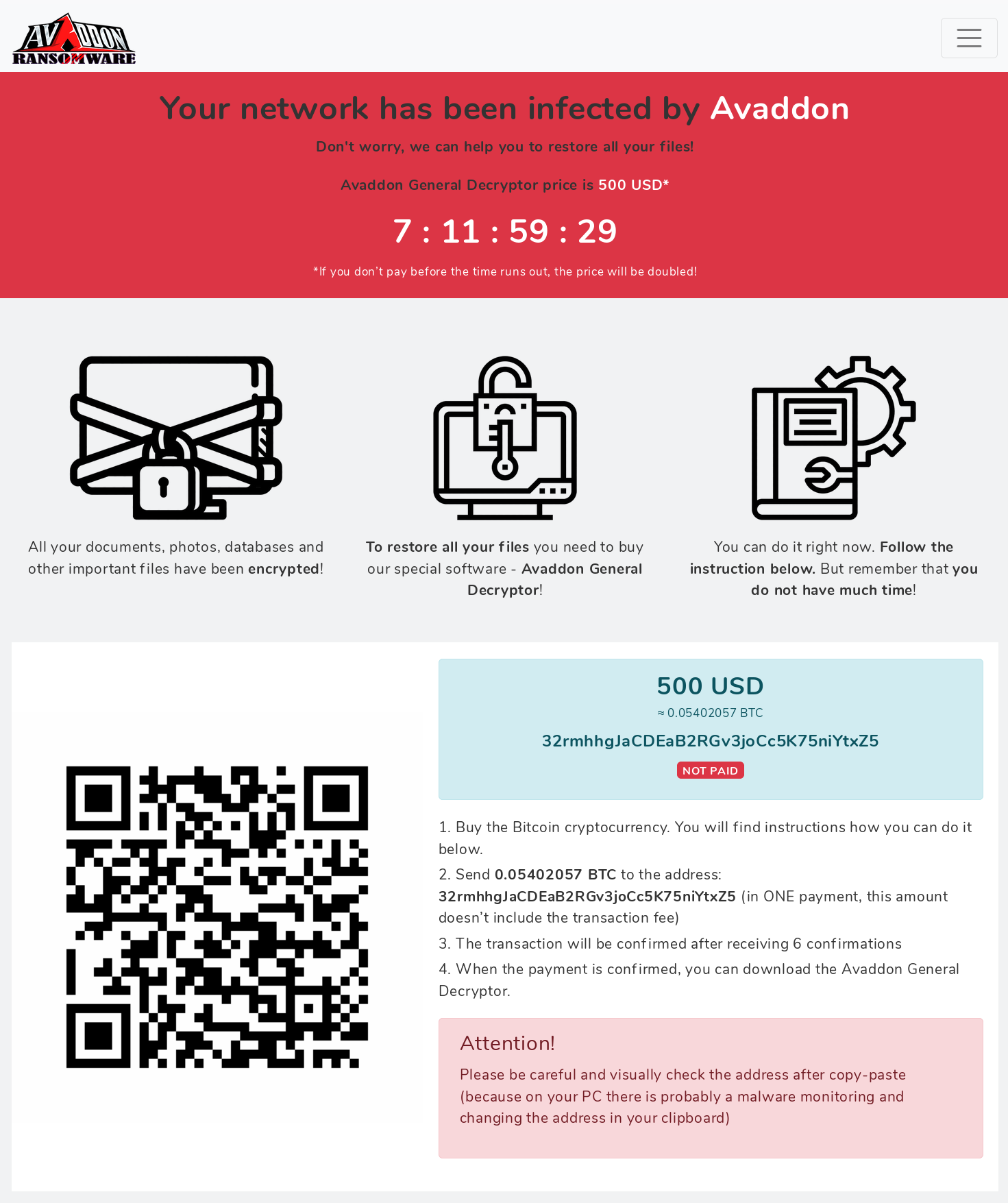
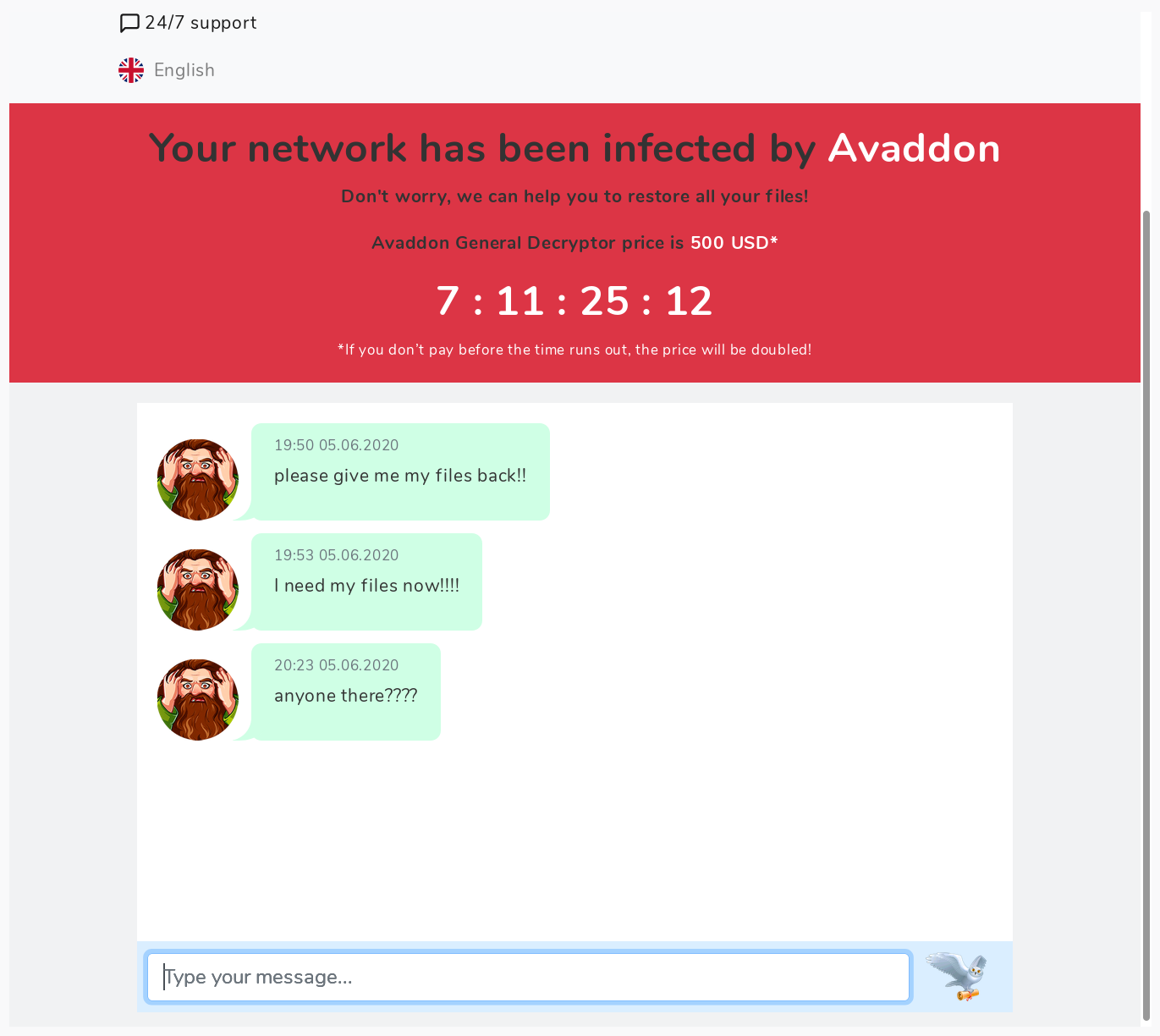
After entering the ID provided in the html page, the following page is presented asking for $500 USD in Bitcoin to be paid to 32rmhhgJaCDEaB2RGv3joCc5K75niYtxZ5:
The site provides a chat interface in order to communicate with the operators and possibly negotiate. We tried to reach out to the operators using this interface but received no response:
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: BitsAdmin.N (Trojan)
- GAV: Avaddon.RSM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




