Mustang Panda Group Side Loading DLL
Overview:
SonicWall, Capture Labs Threat Research Team; observed new activity from MUSTANG PANDA, using a unique infection chain related to the PlugX Trojan. The legitimate vulnerable binary is part of Adobe’s Suite which will load any library named “hex.dll”.
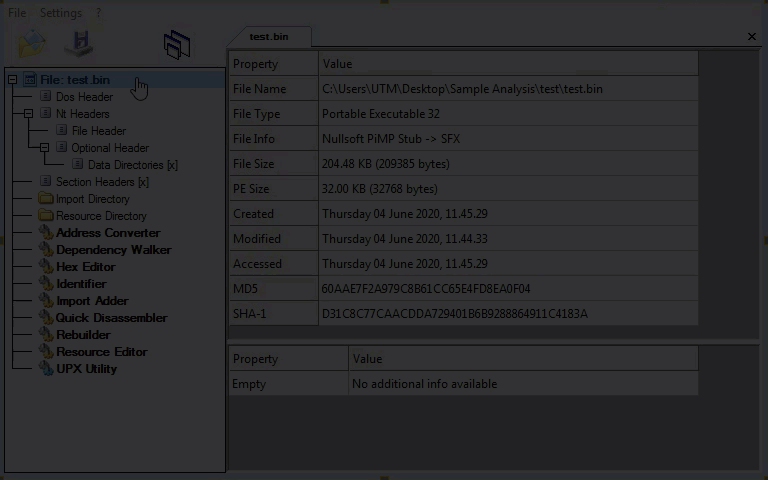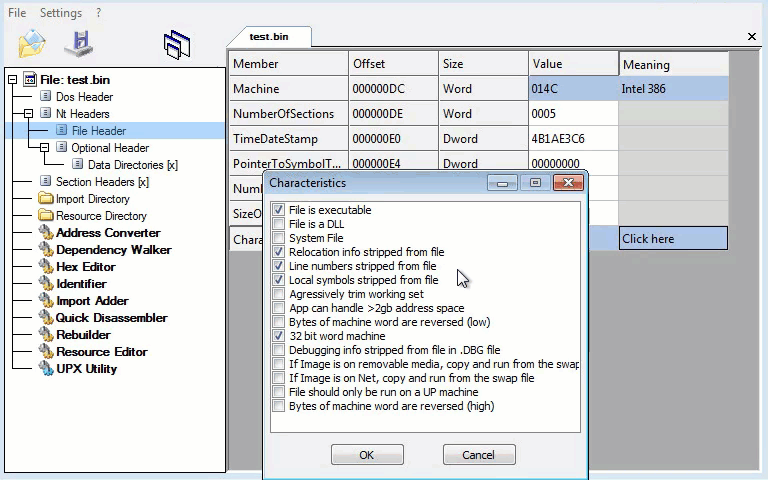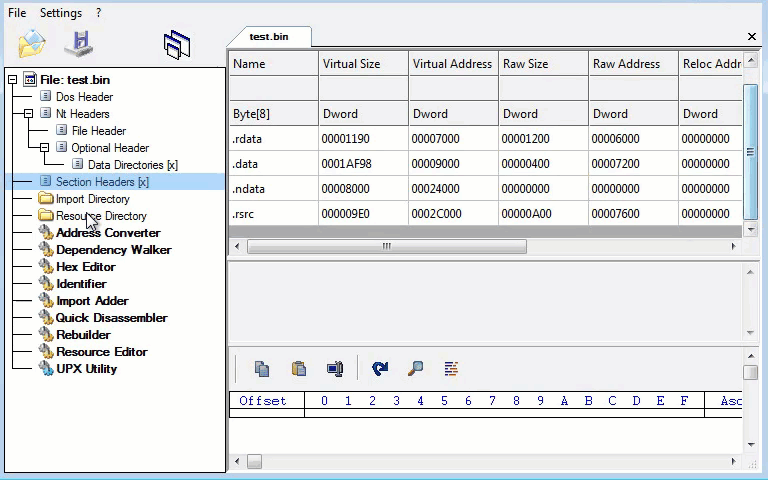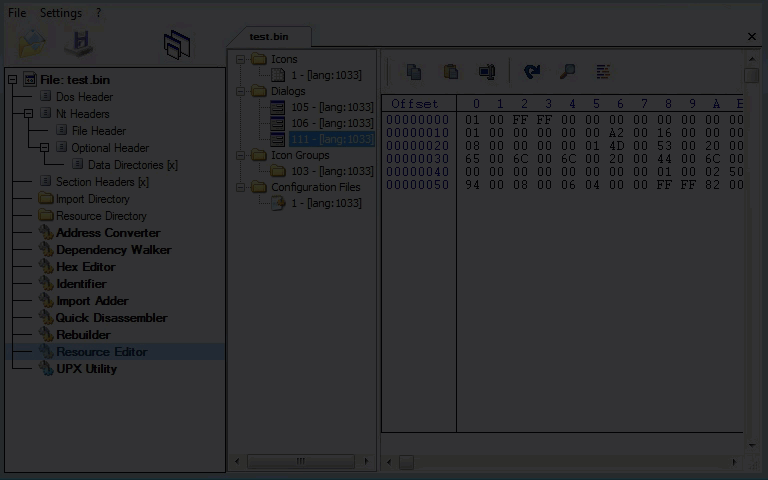
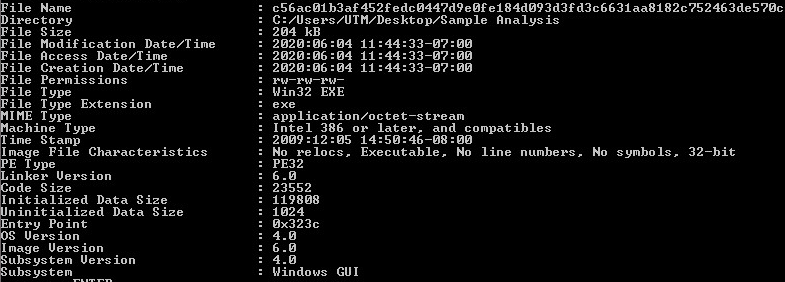
Sample 1st Layer, Static Information:
Looking at the first layer in CFF Explorer, checking for corruption. The first layer is a Win32 binary.
Command-Line Static Information:
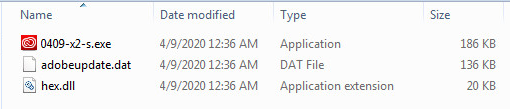
Extracted Files From Binary:
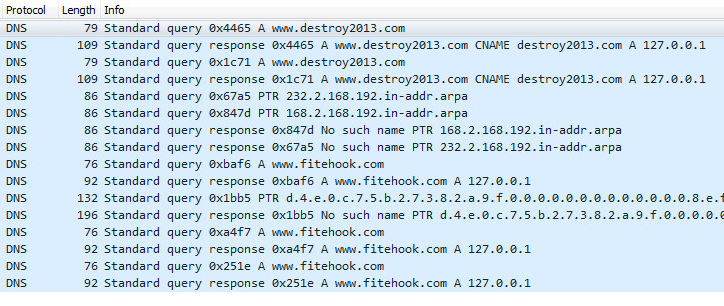
HTTP Network Artifacts:
Dynamic Artifacts:
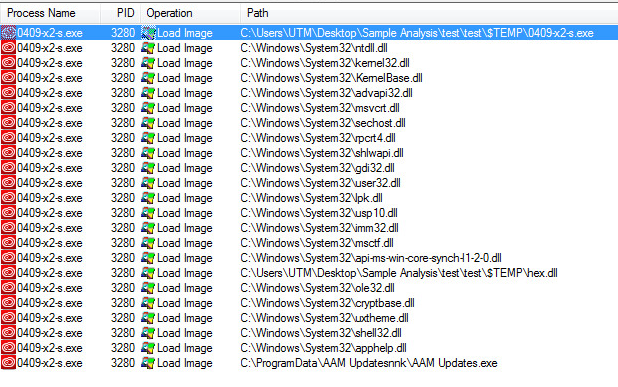
Loaded Modules:
- See hex.dll in the list.
Process:
- Command-Line String Used: “C:\ProgramData\AAM Updatesnnk\AAM Updates.exe” 862
- Autostart string active
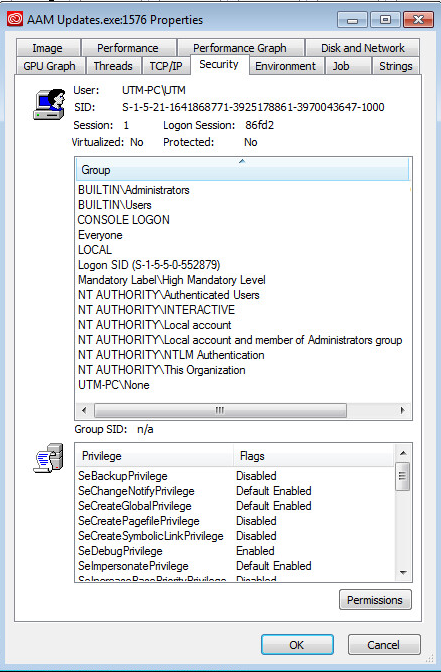
Process Security:
Setting SeDebugPrivilege gives you the ability to start using hacking techniques used in malware. By default, users can debug only processes that they own. In order to debug processes owned by other users, you have to possess the SeDebugPrivilege privilege. Once this privilege is granted you gave away the farm. This allows code injection.
- SeDebugPrivilege
- Group NT AUTHORITY
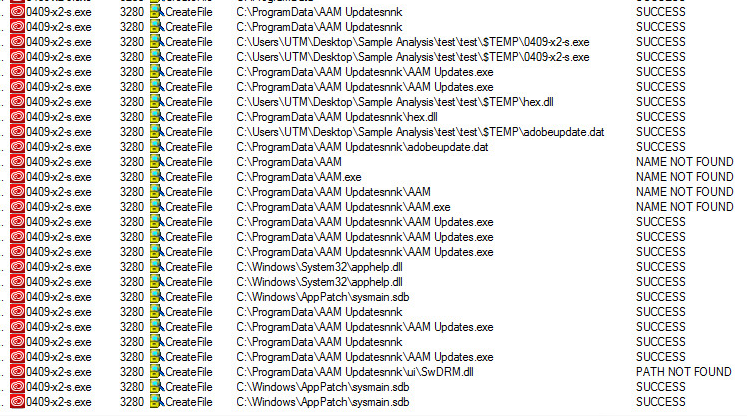
CreateFile Artifacts:
- Folder Created: AAM updatesnnk
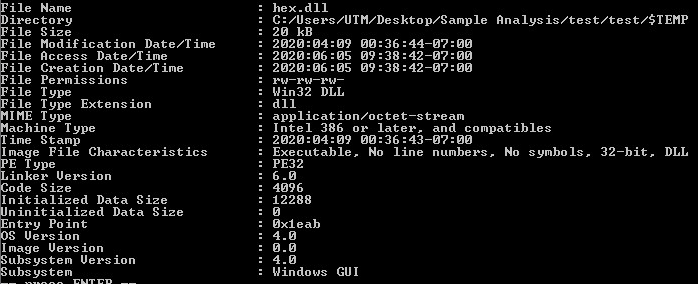
Hex DLL Static Information
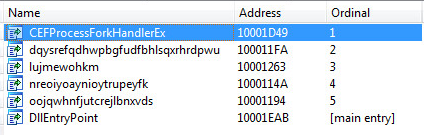
Side-Loaded DLL Exports:
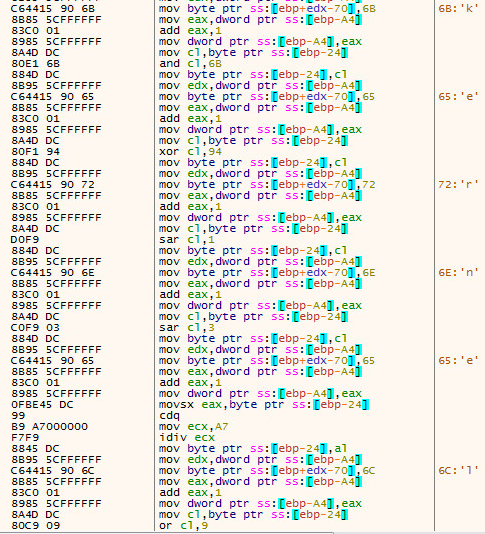
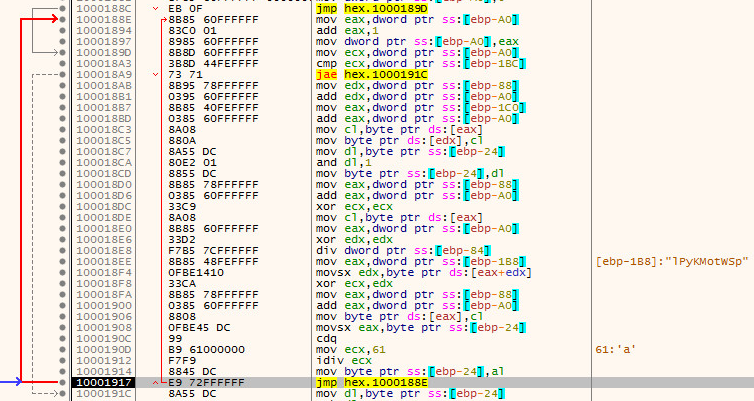
Shellcode:
The malware author tries to hide the loading of Kernel32 dll, However you can see it within a debugger. This slow loading one character at a time is needed to bypass signature filters. You can also see the junkcode between the characters of Kernel32 dll. It’s always interesting to watch how malware authors bypass signature enforcement within their shellcode.
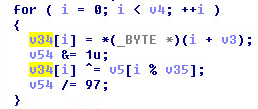
Decryption of Shellcode:
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: Mustang.PAN (Trojan)
Appendix:
Sample Hash: c56ac01b3af452fedc0447d9e0fe184d093d3fd3c6631aa8182c752463de570c