Fake ransomware decryptor spreads Zorab ransomware
Sonicwall Capture Labs threat research team observed Zorab ransomware posing as DJVU ransomware decryptor .
When a user’s computer files are encrypted by a ransomware,he desperately looks for tool to decrypt files instead of paying ransom. One such decyptor called DecryptorDjvuMlagham.exe instead of removing the DJVU ransomware infection, it spreads Zorab ransomware.
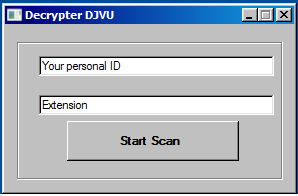
Upon clicking the application it launches a console and asks for relevant information.
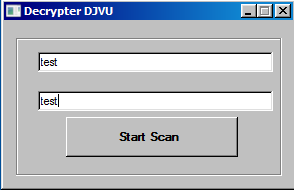
But it accepts any input and does not validate it.
Once you click Start Scan instead of scanning it extracts another executable called crab[.]exe at users\AppData\Local\Temp
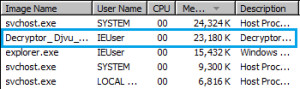
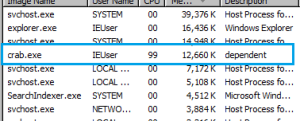
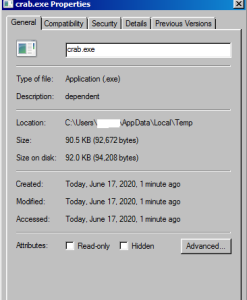
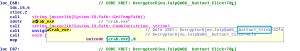
Dissembling the code one can see that on the button click crab.exe is extracted.
This executable then starts encrypting files. The encrypted files have extension .ZRB
It also encrypts the already encrypted files and changes the extension to .ZRB
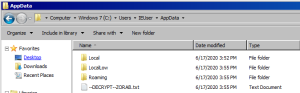
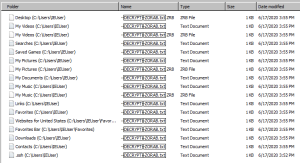
The attacker keeps a ransom note in each folder called -DECRYPT~ZORAB.txt
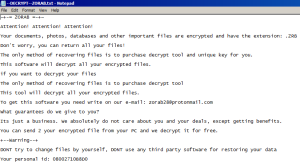
The ransomware note reads the following and boasts that this is just a business and they don’t care about the victim. They also demand to write an email to zorab28@protonmail.com for information about how to decrypt files.
At the time of writing this alert we had not yet received a response to the email that we sent to the attacker.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Zorab.RSM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




