Fake Android Zoom Video Meeting apps harbor malware/adware components
There has been a sharp rise in people working from home as a precautionary measure towards lowering the spread of Covid-19. As a result, work from home related tools have seen an uptick in demand and usage. The video-conferencing app Zoom has enjoyed a surge in demand the last few months and this has caught the attention of malware writers. We recently blogged about a malicious cryptominer that disguises itself as Zoom app.
SonicWall Capture Labs threats research team has observed malicious Android apps that use the name, user interface (UI) elements and parts of code of the legitimate Zoom app to infect unsuspecting users. We examine a few such cases in this blog.
Case I
- Md5: f6d554abd32fd32a1bc75f65aef23bad
- App Name: ZOOM Cloud Meetings
- Package Name: com.judf.zoom
After installation and execution the first thing we see are full screen advertisements:
Later we see a login screen, but its not for Zoom. The login screen when translated says “Mobile Cloud Office”. This appears to be an app that is repackaged to look like the ‘Zoom’ app, but there are no other similarities:
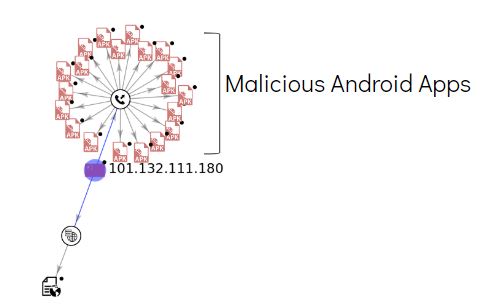
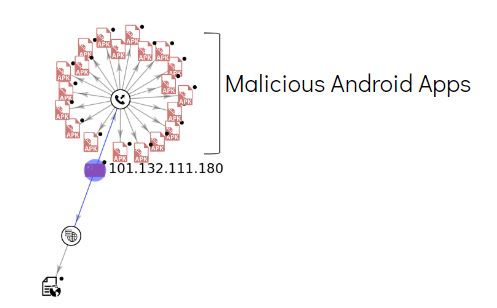
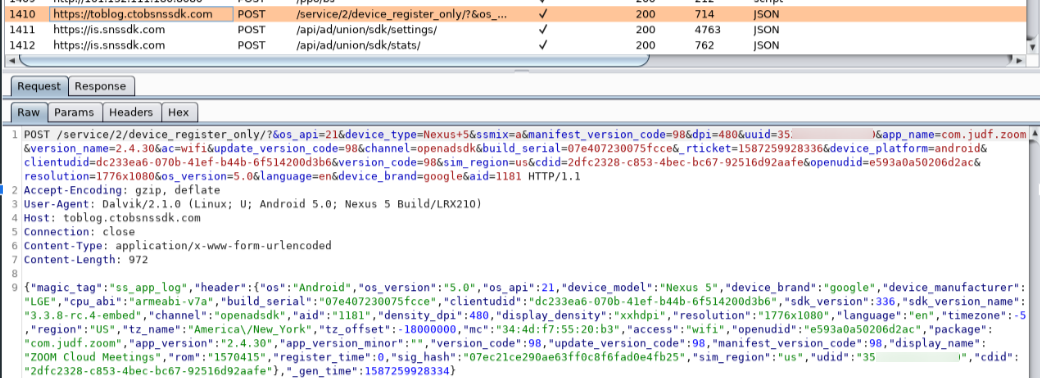
The malware communicates with the following domains that have malicious indicators:
- 101.132.111.180
- sta.2980.com
- toblog.ctobsnssdk.com
Device specific information that is exfiltrated during network communication includes:
- Device type
- OS version
- IMEI (uuid in this case)
- Region
- OS version
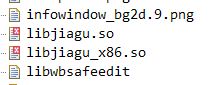
This malware contains a library file in the assets folder:
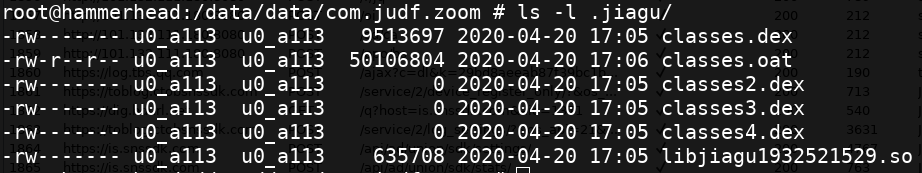
We saw this library file on the device (post app installation) in a hidden folder:
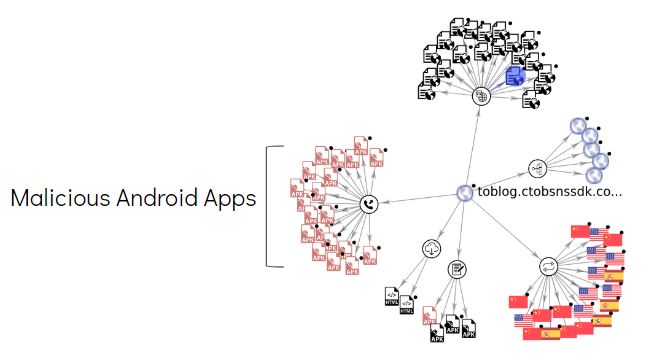
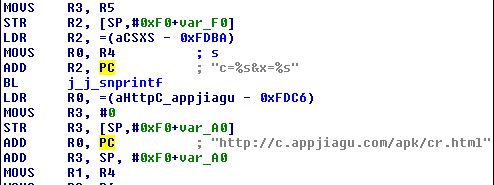
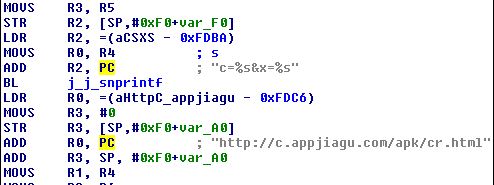
This library file contains the following link:
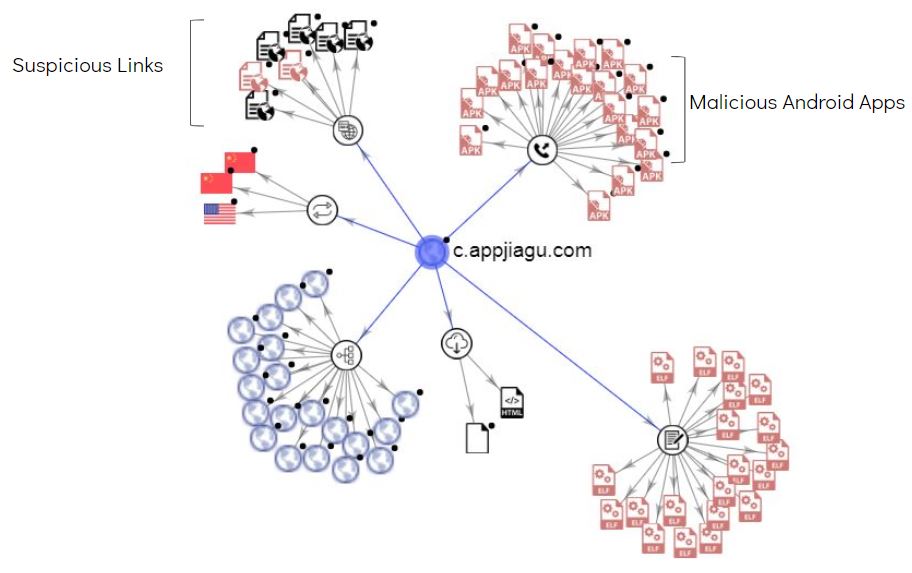
This link was not accessed during our analysis, however there are multiple suspicious links and malicious apk files associated with this domain:
Below are few suspicious links listed by VirusTotal for this domain:
- h[xx]p://c.appjiagu.com/ad/analy.html
- h[xx]p://c.appjiagu.com/apk/cr.html (Hard-coded in the sample we analyzed)
- h[xx]p://c.appjiagu.com/ad.html
- h[xx]p://c.appjiagu.com/root.html
Case II
- Md5: e640eb702de37deb80c0a763eb67dea6
- App Name: Zoom
- Package Name: net.droidjack.server
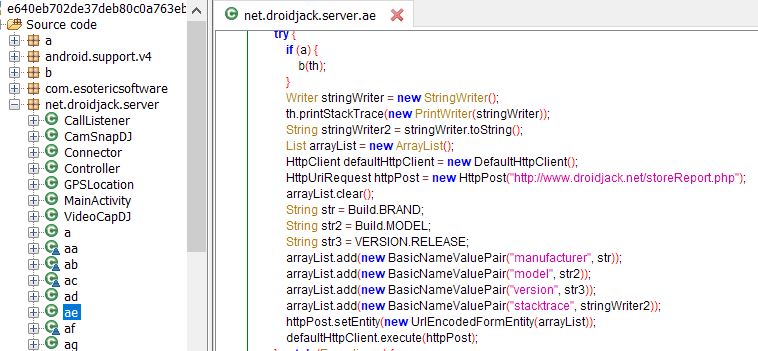
We saw few instances where the Android Remote Administration Tool (RAT) DroidJack embedded apps were named as Zoom.
These apps do not contain any Zoom related assets (icons and other UI elements) as we have seen in other such fake apps. DroidJack infested apps are common and we have written blogs in more depth about such fake apps in the past. On a high level DroidJack has the following capabilities:
- Read and delete call logs
- Make calls
- Read, write and delete SMS messages
- Read, create and delete contacts
- Take pictures from the front/back camera
- Record videos from front/back camera
Case III
- Md5: 30a1a22dcf7fa0b62809f510a43829b1
- App Name: Zoom Package
- Name: us.zoom.videomeetings
On installation and execution this app looks similar to the legitimate Zoom application. The icons, UI elements are on point:
However, reviewing the AndroidManifest.xml file gives clues about the malicious additions. On comparing this xml file of the malicious app against the clean Zoom app we see a distinct addition in the malicious counterpart. A new receiver – us.zoom.videomeetings.byfsl.Qrfde – and service – us.zoom.videomeetings.byfsl.Qxohs – are present as shown below:
Code comparison of the two apps show the distinct additions:
The code contains encoded parts which are added to keep the malicious components hidden from automated scanner tools and to make it difficult for security researchers to analyze the code.
Case IV
- Md5: fb5243138a920129dd85bb0e1545c2be
- App Name: Zoom Package
- Name: us.zoom.videomeetings
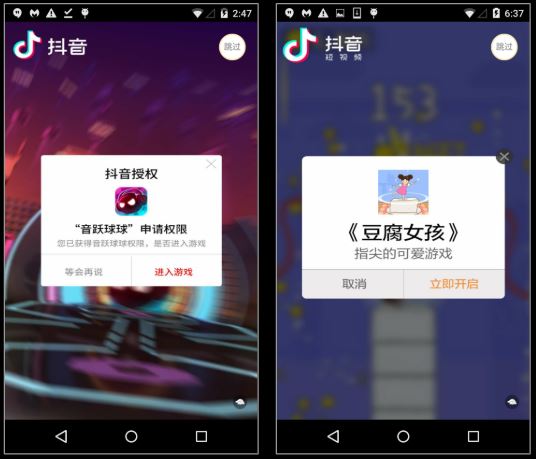
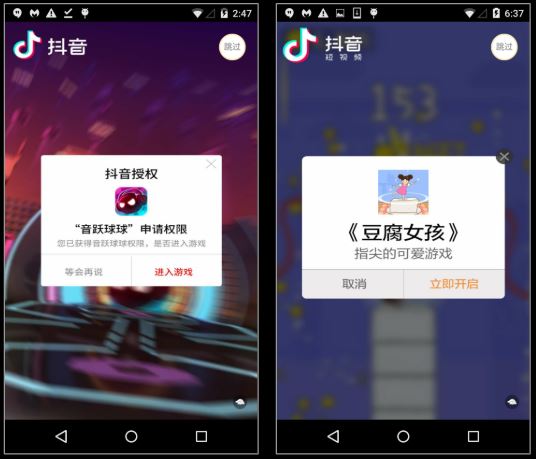
This malicious app copies the icon and name of Zoom app well, but immediately upon execution we are shown advertisements instead of the Zoom login screen:
It downloads and shows ads related configuration from the domain – hxxp://sf3-ttcdn-tos.pstatp.com/obj/ad-pattern/renderer/package.json.This domain has a number of malicious indicators as seen on VirusTotal:
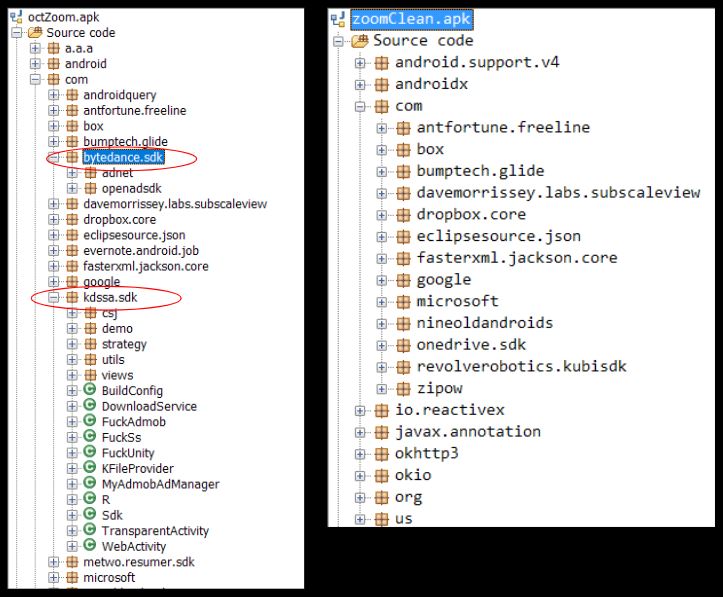
This adware contains additional components when compared to the original Zoom app:
SonicWall Capture Labs provides protection against this threat with the following signatures:
- GAV: AndroidOS.Zoom.FK (Trojan)
- GAV: AndroidOS.DroidJack.RT (Trojan)
- GAV: AndroidOS.Zoom.FKE_2 (Trojan)
- GAV: AndroidOS.Ad.UA (Trojan)
Indicators Of Compromise (IOC):
- fb5243138a920129dd85bb0e1545c2be
- 30a1a22dcf7fa0b62809f510a43829b1
- e640eb702de37deb80c0a763eb67dea6
- f6d554abd32fd32a1bc75f65aef23bad