CoronaVirus Ransomware
SonicWall Capture Labs Threat Research Team has observed a ransomware taking advantage of the Coronavirus fear. As the world battles and seeks more information about the novel CoronaVirus , attackers are finding news news to take advantage of this.This particular ransomware threatens the user that CoronaVirus is here and should pay money to get rid of it .
Infection Cycle:
The ransomware does the following:
It encrypts and zips the files and renames it to coronaVi2022@protonmail.ch__<filename>.

It changes the drive name to CoronaVirus
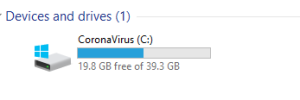
It drops CoronaVirus.txt in each and every folder of the infected system.

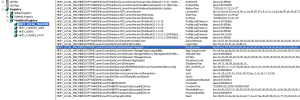
Modifies the following registry keys
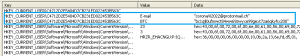
Adds the following registry keys
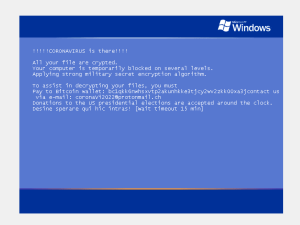
The malicious sample shows following ransom message.

It waits for 20 mins before it restarts the victim’s machine and displays another ransom note.
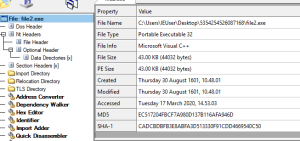
Taking a closer look at the ransomware sample its a 32 bit binary .
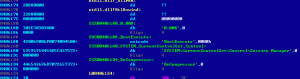
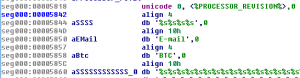
Dissembling the code to find it modifies the BootExecute information, adds Email and BTC wallet information.
IOC
3299f07bc0711b3587fe8a1c6bf3ee6bcbc14cb775f64b28a61d72ebcb8968d3
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: CoronaVirus.RSM_2
- GAV : CoronaVirus.RSM
This threat is also detected by SonicWALL Capture ATP.




