Android CoronaVirus Ransomware comes bundled with decryption code
With the sudden spike in CoronaVirus related threats it is no surprise that recent ransomware uses the same name. SonicWall Capture Labs Threats Research team observed an Android ransomware that uses scare tactics to make a quick buck.
Sample specifics
Application Name: Coronavirus Tracker
Package Name: com.device.security
Md5: d1d417235616e4a05096319bb4875f57
The permissions requested by the malware application are chosen to enable/start key functionality of the malware:
- “Receive boot completed” has been included to enable the service RebootReceiver
- “Request ignore battery optimizations” has been included to ensure that the malware is not hibernated into a low power state to conserve battery
Infection Cycle
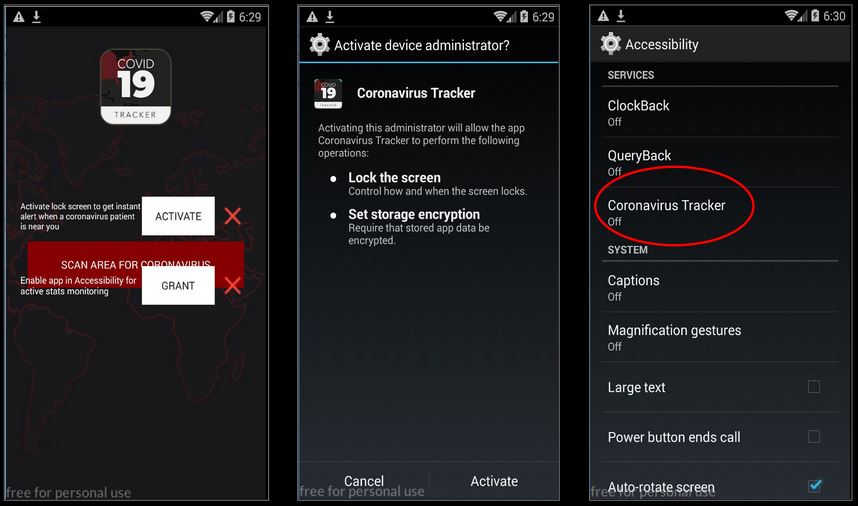
This ransomware spreads by posing itself as a CoronaVirus Tracker:
Once installed and executed it requests for Accessibility Services and Device Admin permission:
After a few minutes we are shown the ransom screen:
Behind the scenes
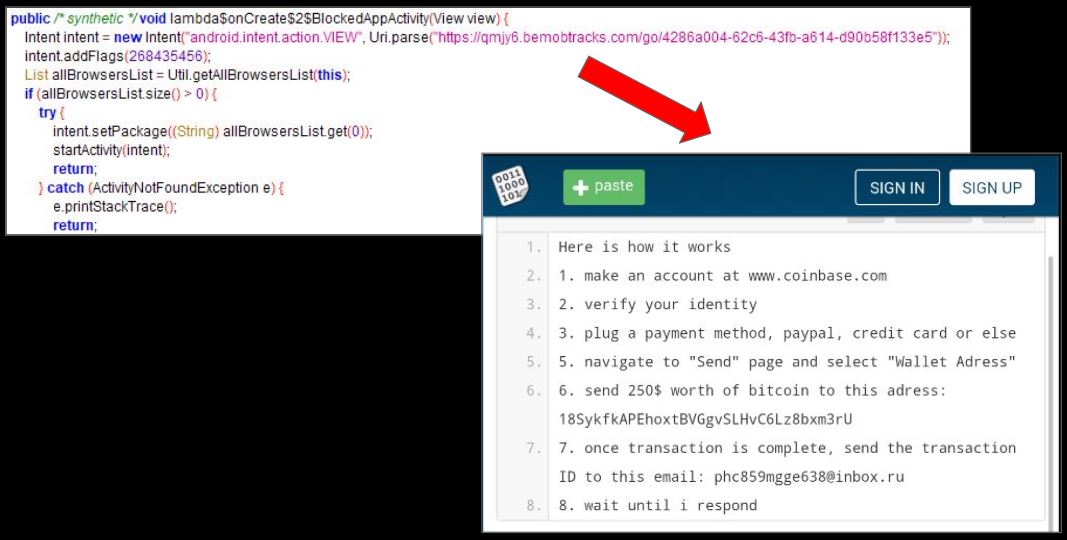
The ransom screen can be intimidating at first viewing, as there are threats to leak images and videos from the device if the ransom is not honored. The ransomware screen is picked from a hardcoded URL in the code which re-directs to a Pastebin page:
Even though this malware appears to be a ransomware, in reality this is just a scareware – a malware that uses scare tactics to coax the victim into paying a ransom. There is no evidence of any sort of file encryption or any way to steal/post the images or videos from the infected device.
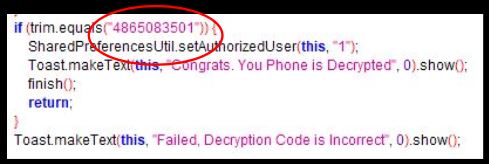
The malware author demands payment in exchange of a decryption code. However checking the code revealed the presence of this decryption code in clear text:
On entering this code 4865083501 we saw the message “Congrats. You Phone is Decrypted”.
Success Rate
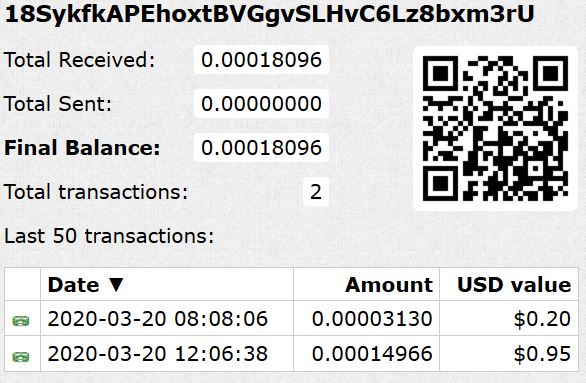
We checked the Bitcoin wallet address mentioned in the ransom note and confirmed that there is not presently significant traffic to this wallet. This indicates that the malware authors have not yet had significant success with this ransomware:
A note of Caution
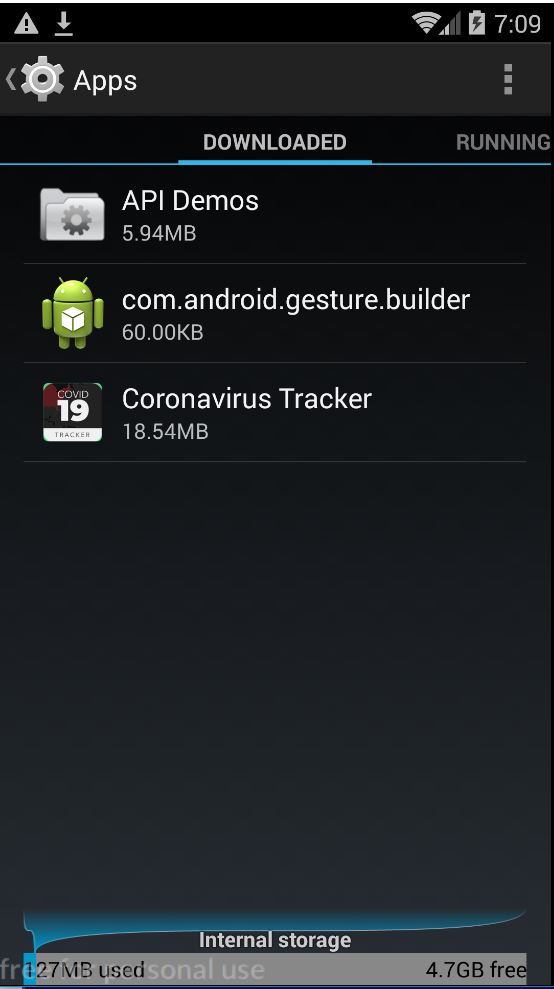
For anyone who has a device infected by this ransomware, the decryption code is 4865083501. After entering this code the app disappears from the app drawer. This gives the user the impression that the app is no longer on the device. But in reality the app keeps running in the background and can be seen in the list of downloaded apps on the device:
Uninstalling the app is not straightforward because of the Device Admin privilege, and the Uninstall button appear greyed out. The only way to remove the app is to first revoke the Admin rights given to this app via Security ->Device Administration -> Untick Coronavirus Tracker.
SonicWall Capture Labs provides protection against this threat with the following signatures:
- GAV: AndroidOS.Decrypt.RSM (Trojan)
- GAV: AndroidOS.CoronaTracker.RSM (Trojan)
Indicators Of Compromise (IOC):
- d1d417235616e4a05096319bb4875f57