PDF Phishing campaign uses Google Docs to steal victim's Email credentials
SonicWall Capture Labs Threats Research team has discovered an ongoing phishing campaign which abuses genuine web-based software office suite platform like google docs. Upon opening the PDF file, a blurred image with instructions on how to view the document is displayed to the user:
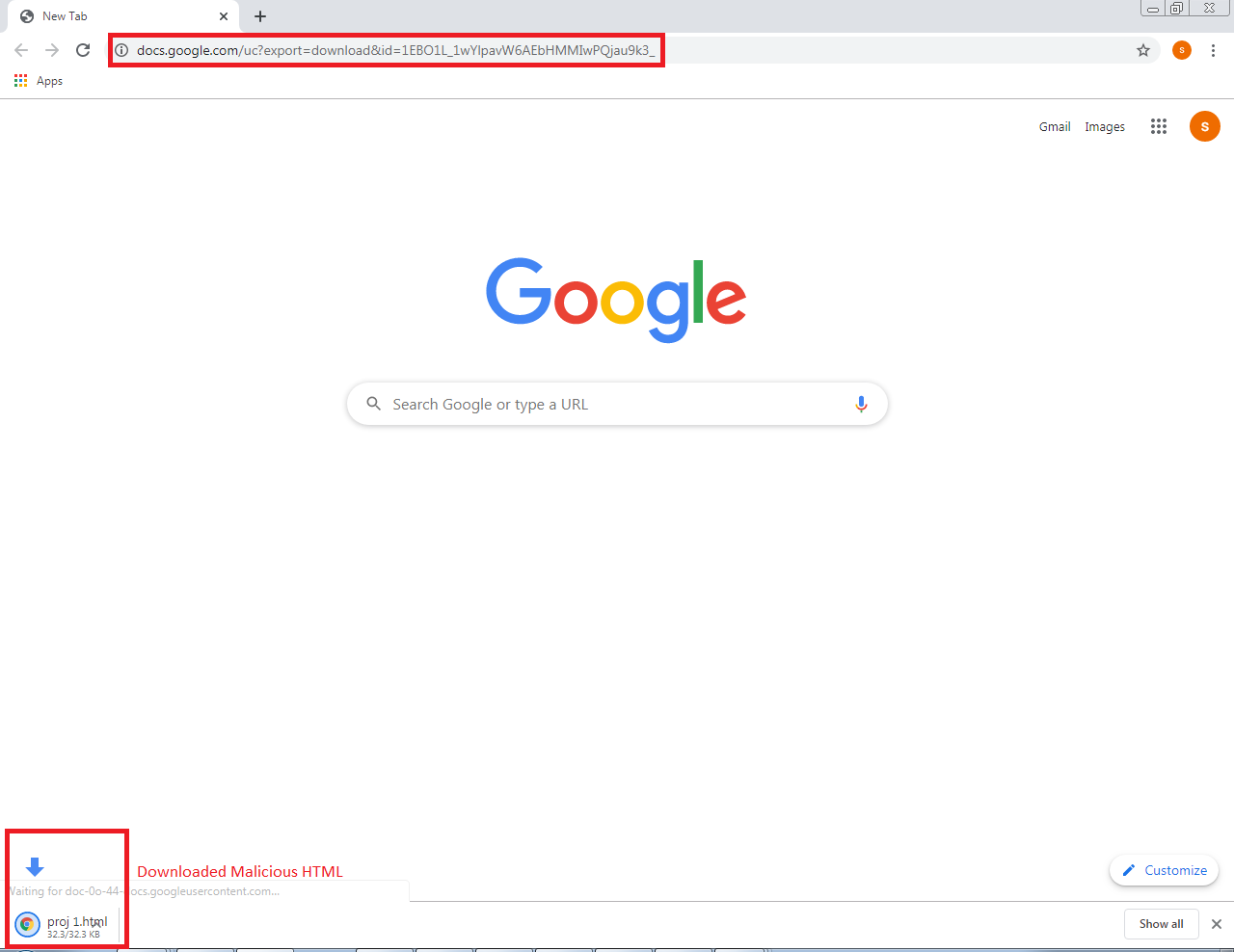
If the instructions as mentioned in the PDF file are followed, an HTML file is downloaded without user intervention from Google Docs URL as shown below:
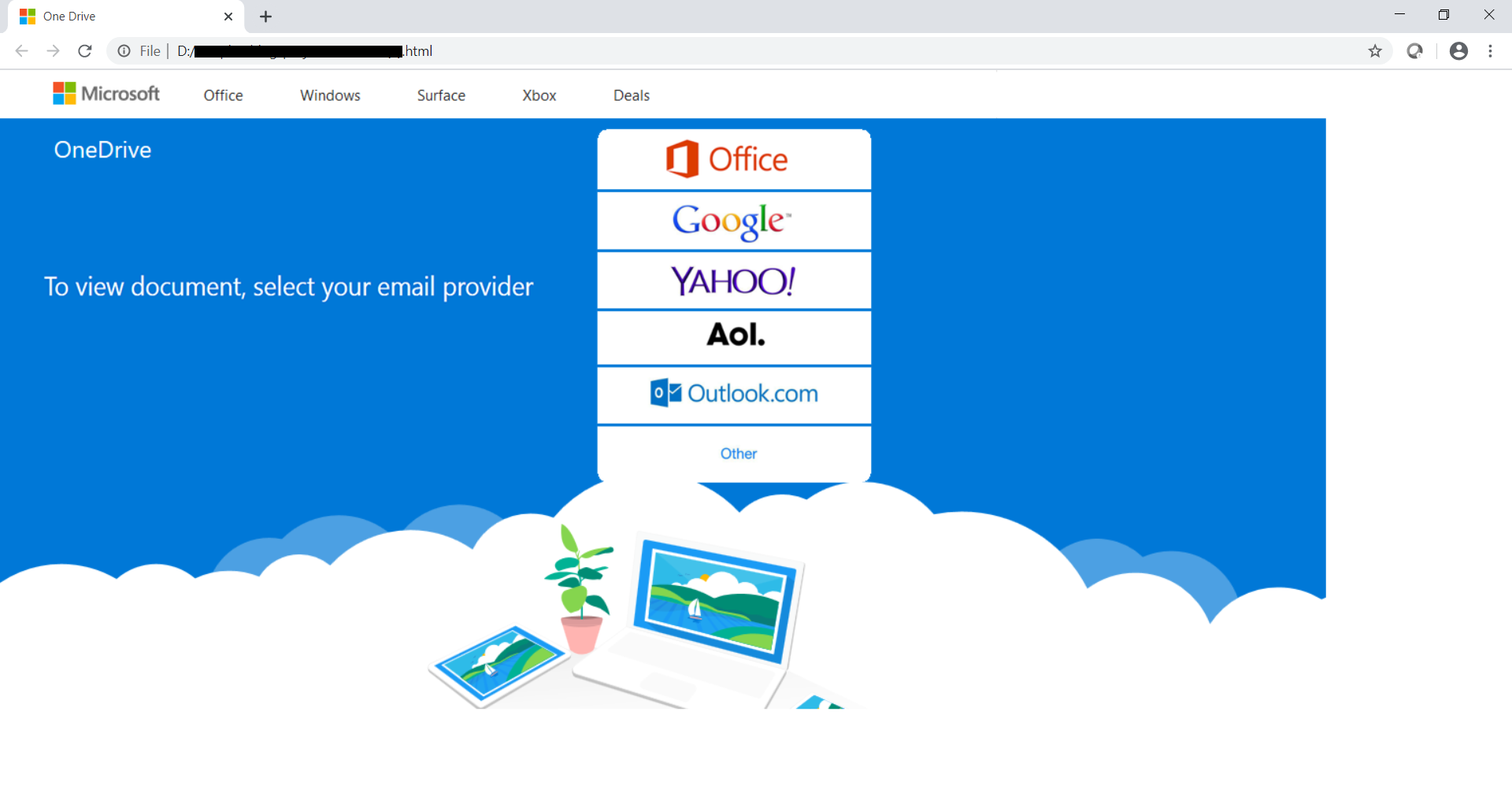
When the downloaded HTML file is opened, the user is shown a genuine looking webpage with options to select email providers like Yahoo, Google, Outlook, Office etc to view the document:
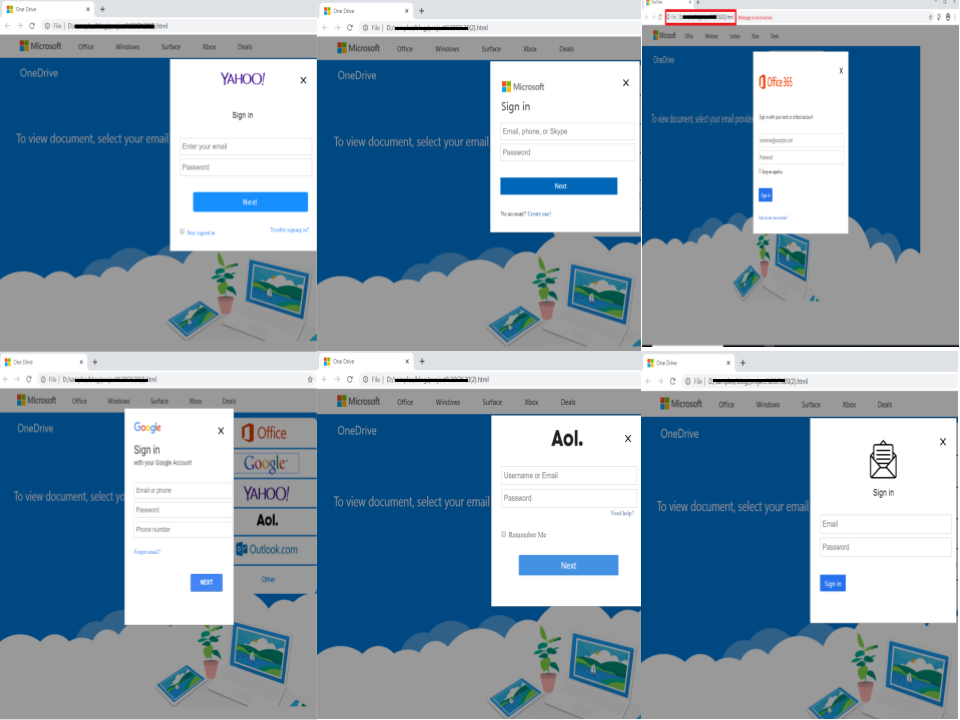
Depending upon the email provider chosen by the user, one of the following form would be displayed:
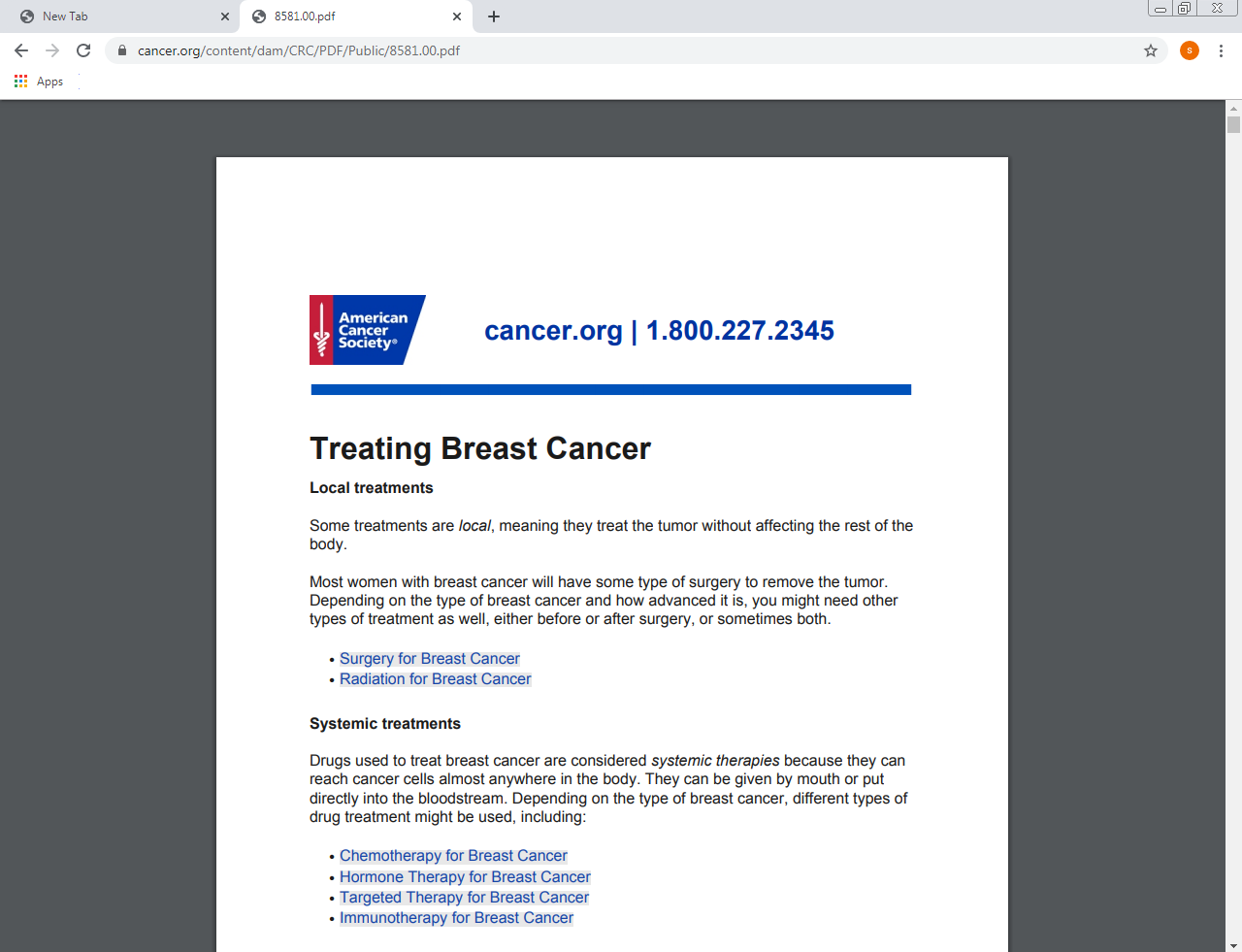
Upon entering the user credentials and clicking the sign-in button the user is displayed a clean PDF file downloaded from remote server to appear legitimate:
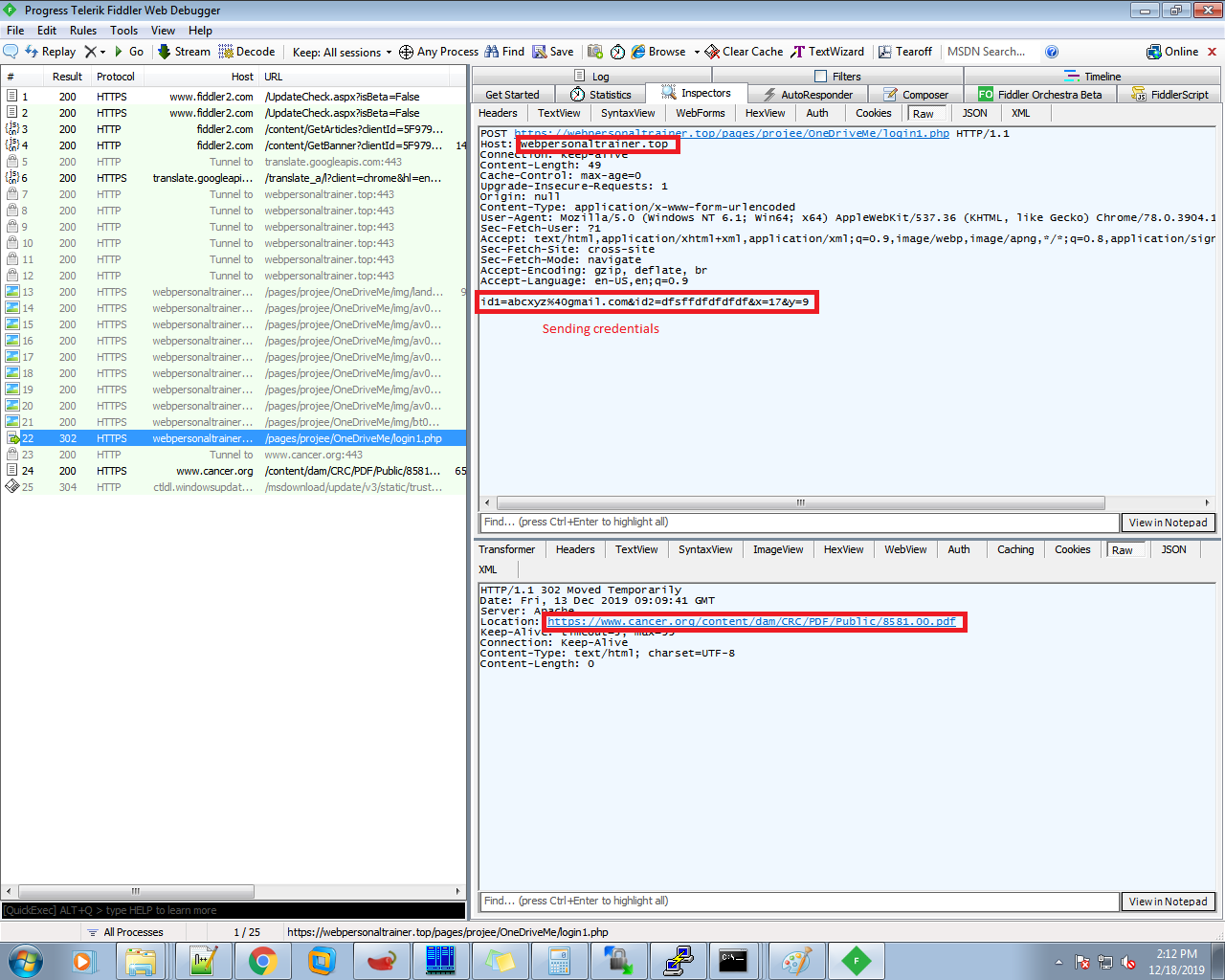
However in the background the malware author steals user credentials when the sign-in button is clicked and sends them to remote web server “hxxps://webpersonaltrainer[.]top” as shown below:
These PDF files are not detected by any vendor when checked on top threat intelligence sharing portals like virus total:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Downloader.FR (Trojan)
- GAV: Downloader.PD_18 (Trojan)