Simda Process Injection into Winlogon DGA Found
Overview:
SonicWall Capture Labs Threat Research Team recently found a new sample and activity in August for Simda. Simda steals information and is capable of modifying websites through injection. Microsoft first detailed Simda long ago, the first use of the DGA was identified in 2012. However, the domains that are generated are active until the year 2106. The algorithm that generates the domain names uses an encrypted set of parameters describing how many characters the domain shall have and what TLD (Top Level Domain) to use. TLDs observed so far in this sample are “.com” only. However, other TLDs have been identified such as (.eu, .info, .com, .su, and .net).
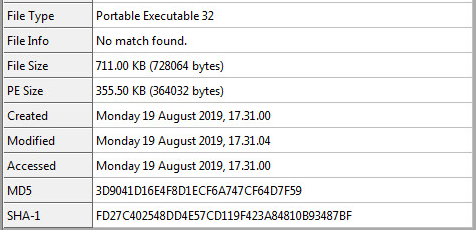
Sample Static Information:
Process Injection:
Within Windows Operating Systems there are multiple approaches to injecting code into a live process. This particular sample uses Dynamic-Link Library (DLL) injection. This involves writing multiple components of the injection process into the remote process with an API named “WriteProcessMemory” and “CreateRemoteThread”.
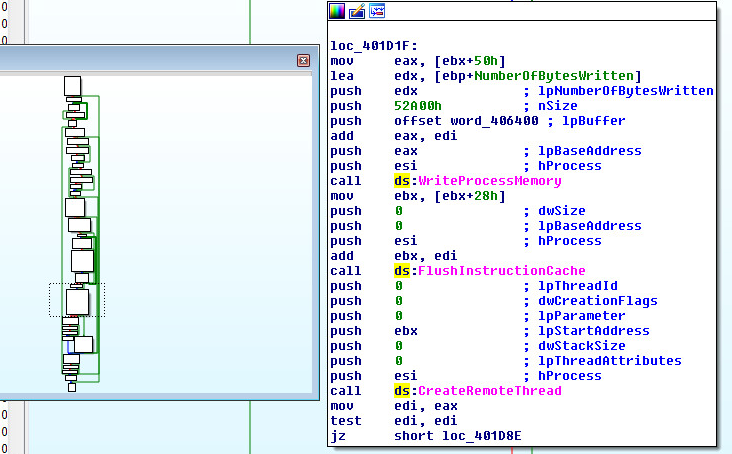
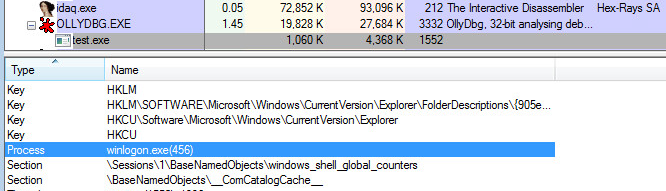
The remote process that will be supplying the code cave is called “Winlogon”. Winlogon has multiple responsibilities: Window Station and desktop protection, Standard SAS recognition, SAS routine dispatching, User profile loading, Assignment of security to user shells, Screen Saver control, Multiple Network Provider Support. Winlogon is also responsible for loading the GINA libraries which are responsible for collecting logon credentials from the user.
Code Cave with Stub aka ShellCode:
The code cave will call an array of Windows APIs to get the DLL loaded into the Winlogon process. Some of the APIs that are called are: RtlImageHeader, VirtualQuery, VirtualAlloc, GetModuleHandleA, LoadLibraryExA, and SetCurrentDirectoryA. The DLL that will be loaded is called “WinSCard.dll”.
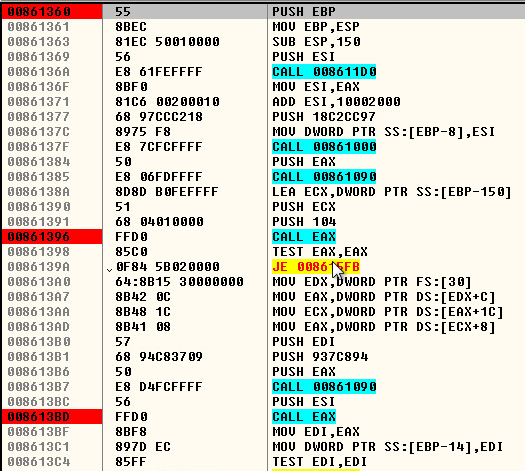
Here is what the code cave looks like in Ida Pro as a memory dump:
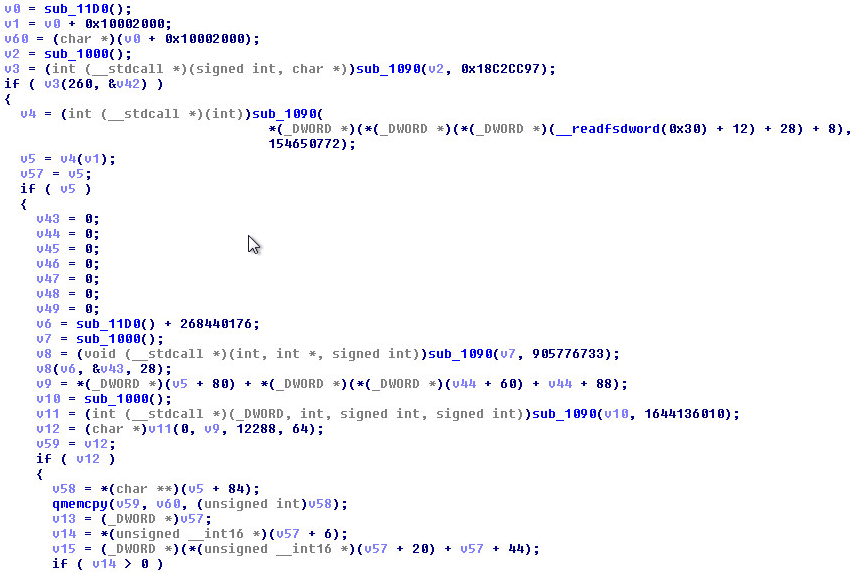
DLL Injection:
The “WinSCard.dll” dumped into Ida Pro. This shows the typical dll injection. It just calls one thread and executes everything in it.
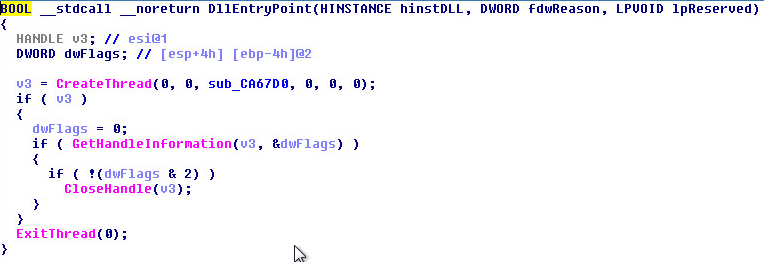
This is the top of the thread that gets called in DLL Main:
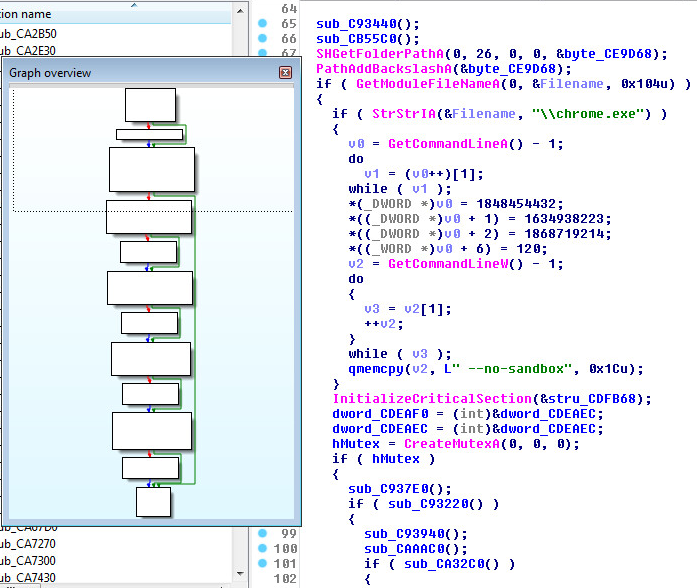
DGA (Domain Generation Algorithm) Found:
Adversaries may make use of Domain Generation Alogirthms (DGAs) to dynamically identify a destination for command and control traffic rather than relying on a list of static IP addresses or domains. This has an advantage of making it harder for defenders to block, track, or take over the command and control channel. This sample makes use of the following DGA:
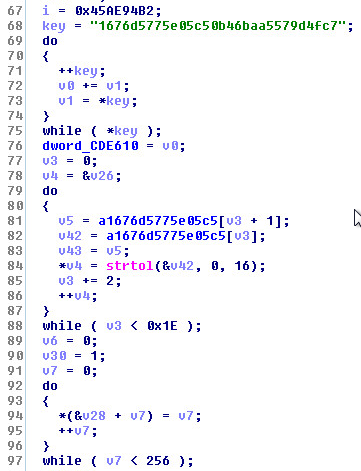
A little lower down in the same function:
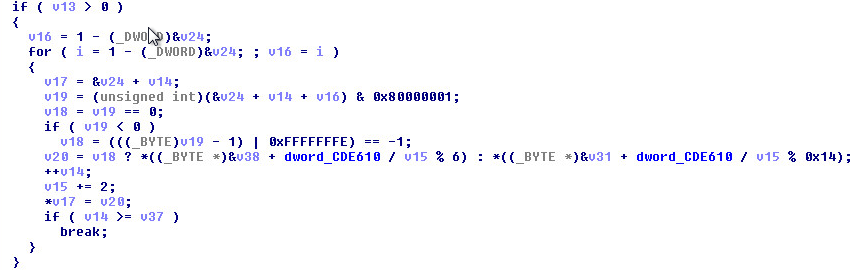
Reversing the DGA into C/C++:
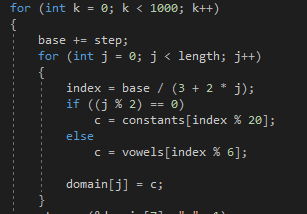
A small list from the DGA output is as follows:
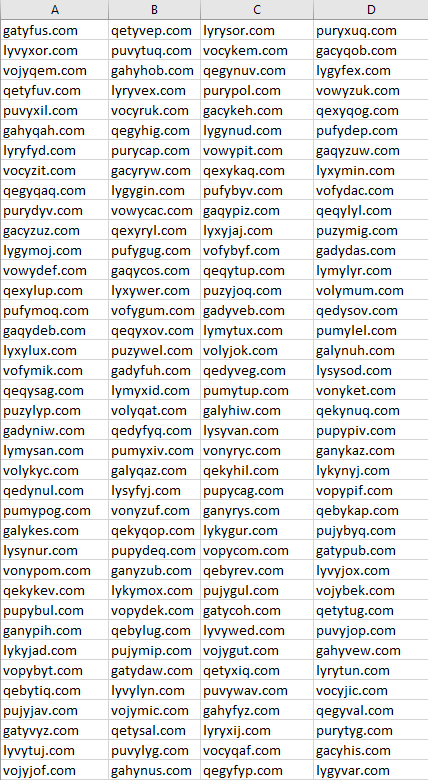
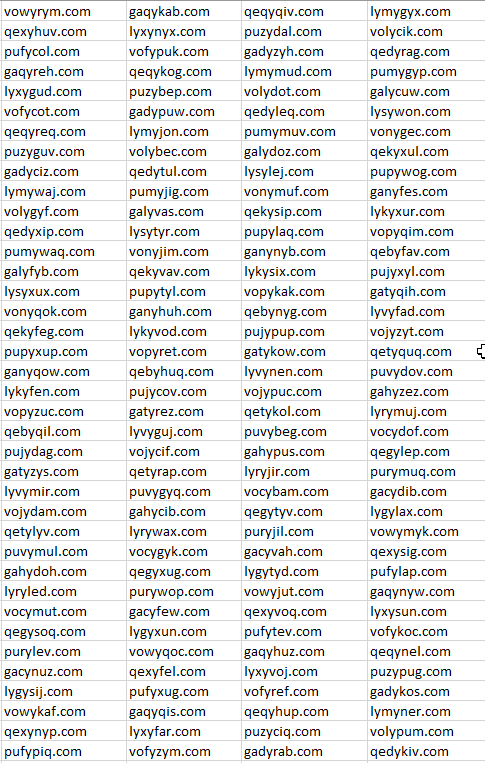
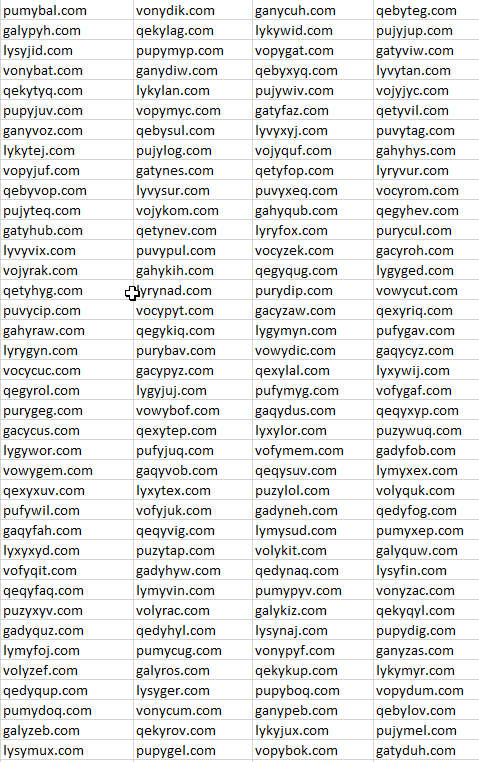
The Domain Generation Algorithm will produce 1,000 active Domains. The domains will be active until the year 2106.
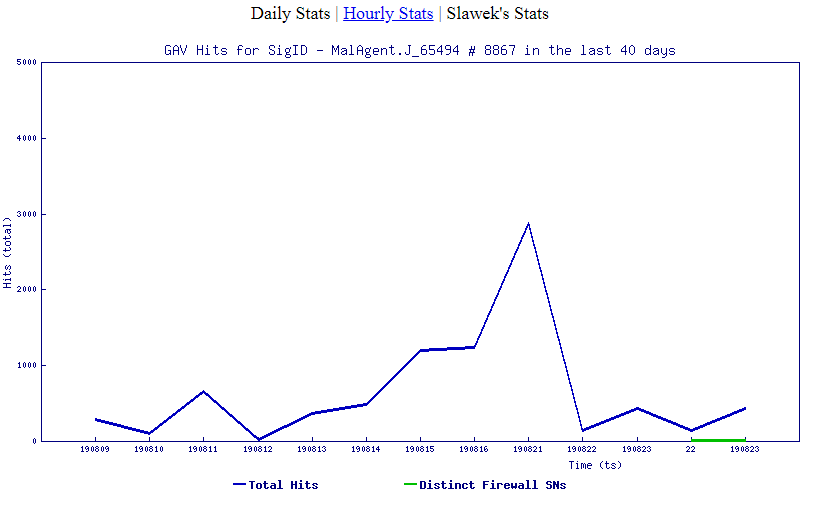
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: Simda.S
- GAV: MalAgent.J_65494