RDP Vulnerability CVE 2019 0708
Overview:
The Microsoft Security Response Center (MSRC) stated, “On Microsoft’s Patch Tuesday”, that a remote code execution vulnerability exists in the Remote Desktop Services formerly known as Terminal Services when an unauthenticated attacker connects to the target system using RDP and sends a specially crafted Protocol Data Unit (PDU) aka packet request to the Terminal Server. The server component of RDS is the Terminal Server (termdd.sys) driver, which listens on TCP port 3389. Other components involved are the (rdpwd.sys) driver. This is where the Multipoint Communication Service (MCS) Stack is located. The heap or pool is allocated in (rdpwd.sys). This heap is corrupted in (termdd.sys) when the MS_T120 reference channel is processed within the context of a channel other than 31 as stated below. Lets see where the vulnerability is located below:
Finding (termdd.sys) inside the Windows Update:
When you download a Windows update from the (MSRC) you will end up with either one of the following files.
- .exe – XP, Windows 2000, 2003 server.
- .msu – Windows 7/8/10 and Server 2008/2012/2016.
Our testing was executed on Windows 7, so we are going to pay attention to the (.msu) update file. When we expand the file we see the following:
Looking at the (.cab) file, we will also expand this file next. We now have the following:
The 1,573 files are the updated files. This is what Microsoft calls a (Cumulative Update) which patches a variety of areas of the Operating System. We know the component we are looking for is called (termdd.sys) so we can do a simple search. Sure enough the file has been updated. The next part is to locate what has changed.
termdd.sys File Updates:
Using your favorite BinDiff tool. We can locate the functions that have changed.
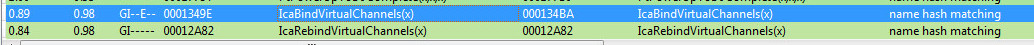
The two functions which have been updated are “_IcaBindVirtualChannels and _IcaRebindVirtualChannels”.
Let’s have a closer look at the changes. The patched versions are on the left side of the images, and the unpatched versions are on the right side of the image. You can open the images below in a new tab, by right clicking. This will make the code more readable.
_IcaBindVirtualChannels:
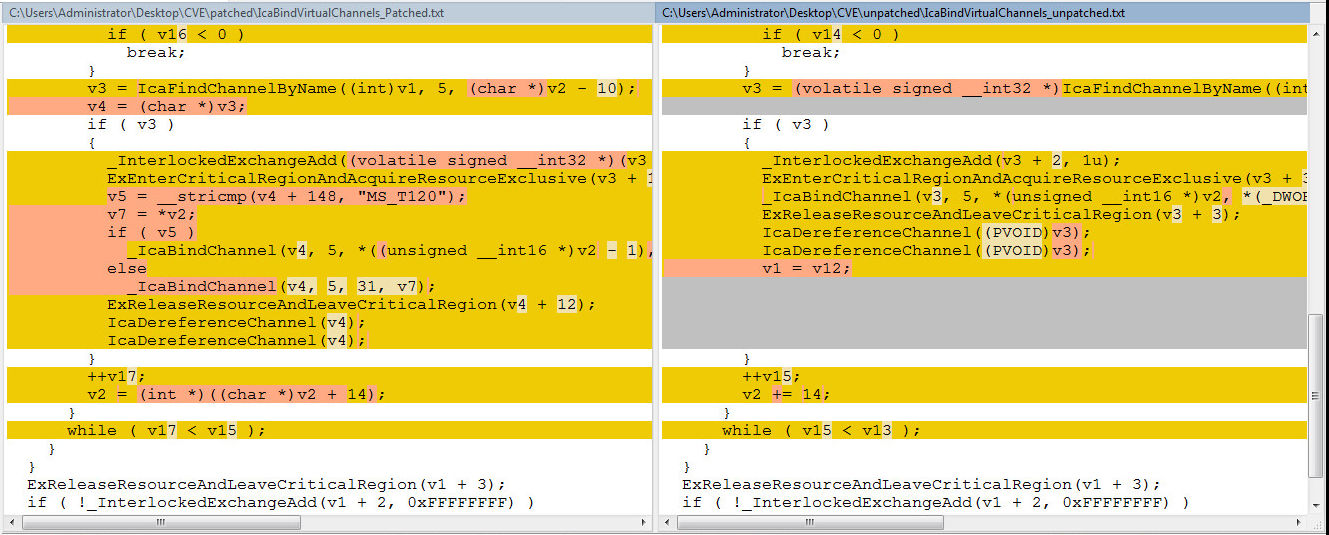
_IcaRebindVirtualChannels:
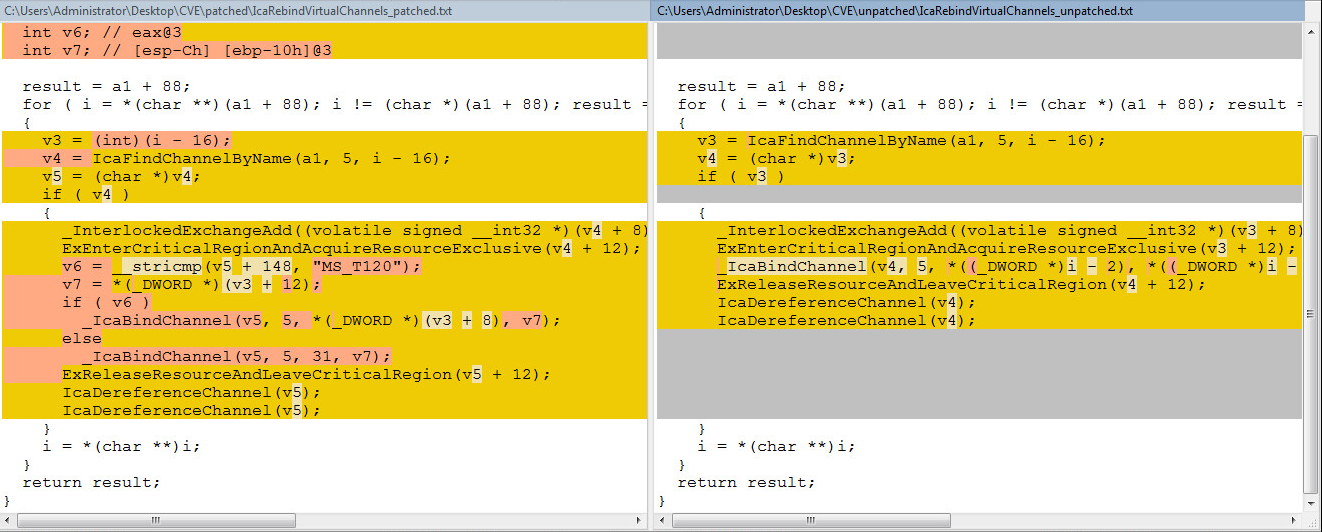
From the images above, Microsoft has now patched the functions by adding a string comparison check for a client connection request using the channel name of “MS_T120” and ensures it binds to channel 31 only.
Vulnerability Sequence:
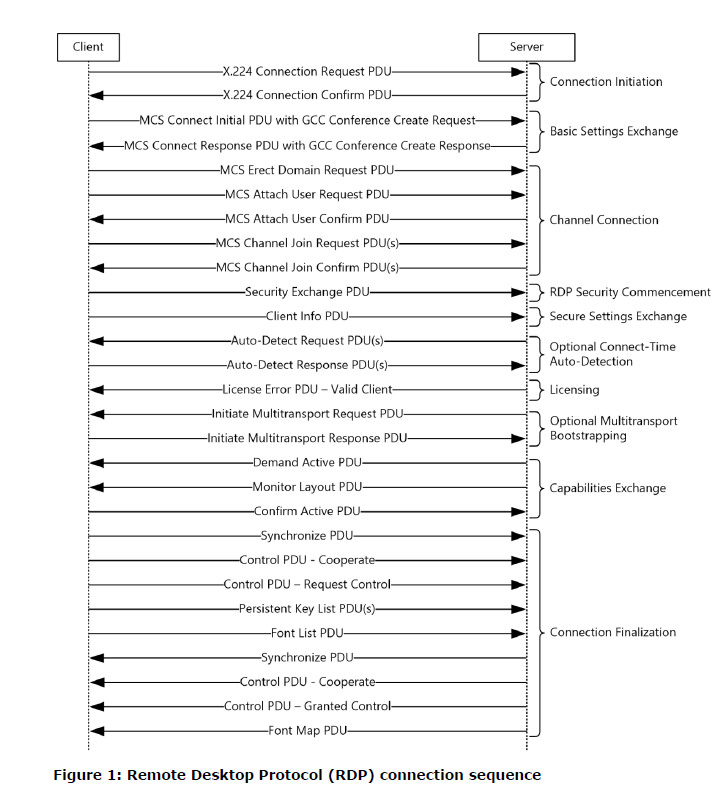
To recap, the “MS_T120” virtual channel is being bound as a reference channel to number “31” during the PDU packet request to the Server called “MCS Connect Initial PDU with GCC Conference Create Request”. This is labeled in the picture below as the “Basic Settings Exchange”. During this exchange the Client will supply the channel name which is not whitelisted by the server, meaning the attacker can setup another sequence named “MS_T120” on a channel other than 31. It’s this virtual channel use of “MS_T120” on a channel other than 31 that leads to the heap memory corruption and (RCE) Remote Code Execution.
Vulnerable Operating Systems:
- Windows 2003
- Windows XP
- Windows 7
- Windows Server 2008
- Windows Server 2008 R2
Summary & Recommendations:
- SonicWall, can confirm that a patched system will stop the (RCE)-Remote Code Execution exploit.
- Disabling of the RDP Services from outside of your network and limiting the RDP Services internally.
- RDP Client requests with “MS_T120” on any channel other than 31 during GCC Conference initialization should be blocked.
SonicWall, provides protection against this threat:
- IPS:14225 “Windows Remote Desktop Services Remote Code Execution (MAY 19)”




