Emotet malware delivered through spam emails
SonicWall Capture Labs Threat Research team has observed a spam email campaign sending fake remittance advice emails that spreads Emotet malware through malicious Word document attachments. The message claims that a recent payment has been made to the victim, luring them to open the attached Word document.
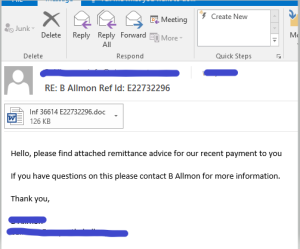
Infection Cycle:
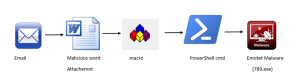
The attached document when opened looks like a warning prompting the victim to enable content. The document has hidden macros in it.
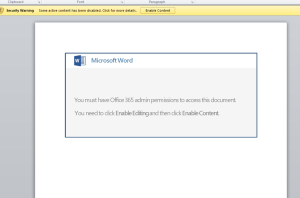
This will launch a PowerShell command upon enabling the ‘active content’. The PowerShell command downloads the Emotet malware on the victim’s computer.

![]()
789.exe is the Emotet malware.
![]()
SonicWall Capture Labs Threat Research team provides protection against this exploit with the following signatures:
GAV Downloader.CQC_9 (Trojan)
GAV: Emotet (Trojan)
SonicWall Capture Advanced Threat Protection (ATP) with RTDMI provides protection against this threat.
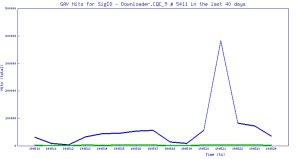
Threat Graph:
IoC:
Doc:
e9e9f78904bfff3c083ac80f14b6b67eb9548de76c70c074436c5c3be0fcd6e6
a82a5bb9f568bf1c2dbb0cfa775f6d86a71cfca1e783dd790434c7691d3c573d
241a37ec6cb4c435bcea7e4f9c74edec59a3d8bd803e271a32f2a0e8e1f88549
9f36d3b724b46fa352ca56e371fd3322f7fea335fe59a71c36a046fb29c034cc
2030bb87b7253368bd608882d2c4d2b365aeccd41e40679148d171a1fd96f9c7
24b50a35f37950ea20fd32c7a206e7e75a16304fc5740a12e78a5b051354cae3
16b073a56a77d960ee2a7c6426a4da145ca030e2fe9212df4ca41108ee86435b
ce0de64b9421a663165e5edad87c2d77e530a1c55c8c7323d13caa898d5d0699
2030bb87b7253368bd608882d2c4d2b365aeccd41e40679148d171a1fd96f9c7
Malware:
48ebd06305d102461a3f3028734536b8b631b88685ac819509b17036520ab378
Email :
bb6bbe6839749ea9dfd1ce64fdb691d6d10985820ffb7f03d8f7cd1f411b6ac2





