Analyzing Gretel A7 Android device for pre-installed malware – Part I
Mobile devices and that applications run on mobile devices increasingly represent a source of threats to networks of all sizes. The SonicWall Capture Labs Threat Research Team therefore monitors numerous sources to identify new and emerging threats coming through mobile devices.
A common security tip for users of Android mobile devices is to install apps only from the official Google Play store. This is because apps in the Google Play store go through multiple layers of automated and manual security checks. Although malicious apps do still make their way onto the Google Play store on occasions, it generally is considered the safest option.
But what if a mobile device is infected even before the user starts using it? Cases of Android devices with pre-installed malware have cropped up from time-to-time. The SonicWall Capture Labs Threats Research Team came across a more recent story on Reddit where a user talked about how his new Android device was displaying unwanted ads and had new apps appear even though the user never installed them, all resulting in a slowdown of the operating system. The user suspected that malicious apps were pre-installed on his device, and eventually identified the app causing the slowdown. The user shared the findings with the community, and we took the opportunity to further analyze the app to better understand the potential threats. The following are our findings:
Sample Specifics
MD5: 79272fcfbcfe359d5f2f554f87e3cf06
Package Name: com.uctsadtxasch.quyry
Initial Observations
The following permissions are requested by the app during installation:
- access_coarse_location
- change_wifi_state
- internet
- read_phone_state
- write_external_storage
- access_network_state
- access_wifi_state
- change_network_state
- read_external_storage
- receive_boot_completed
- wake_lock
- write_settings
On installation of the app on our test device, the first thing we noticed was that this app’s icon is not visible in the device app drawer. Also on further examination we did not see a Main activity for the app in the AndroidManifest.xml file, for that matter there were no activities for this app, which means that the app does not present a screen to the user. The Main activity of an app is the first screen that is shown to the user once the app starts, and absence of activities indicates that the app operates in the background without showing any sort of screen/view to the user.
On further examination of the Manifest file we saw that a BroadcastReceiver com.uctsadtxasch.quyry.util.WkcRvc is registered to trigger at critical events:
- Boot Complete
- Connectivity change
- Timezone change
A receiver getting triggered on Boot complete ensures that the receiver is activated whenever a phone boots up, this is a common technique used by a number of malicious apps to make sure that the app starts as soon as the device starts.
Network Communication
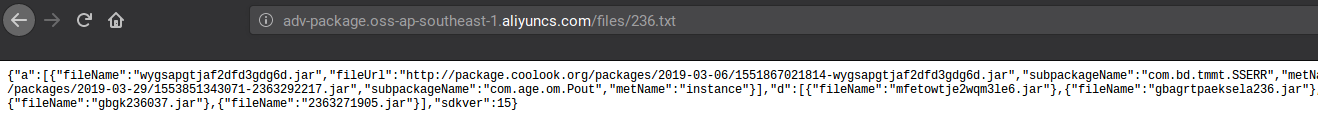
Once we started the application, it contacted a URL for a text file – adv-package.oss-ap-southeast-1.aliyuncs.com/files/236.txt
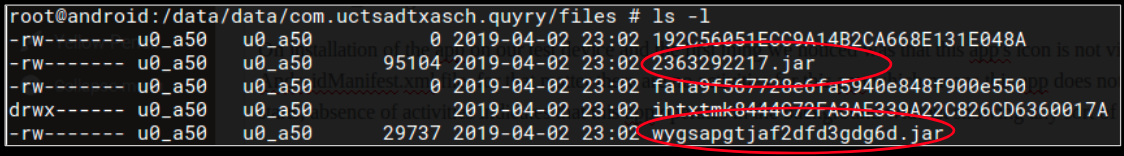
Few of the .jar files visible above were then downloaded and stored on the device locally as seen below:
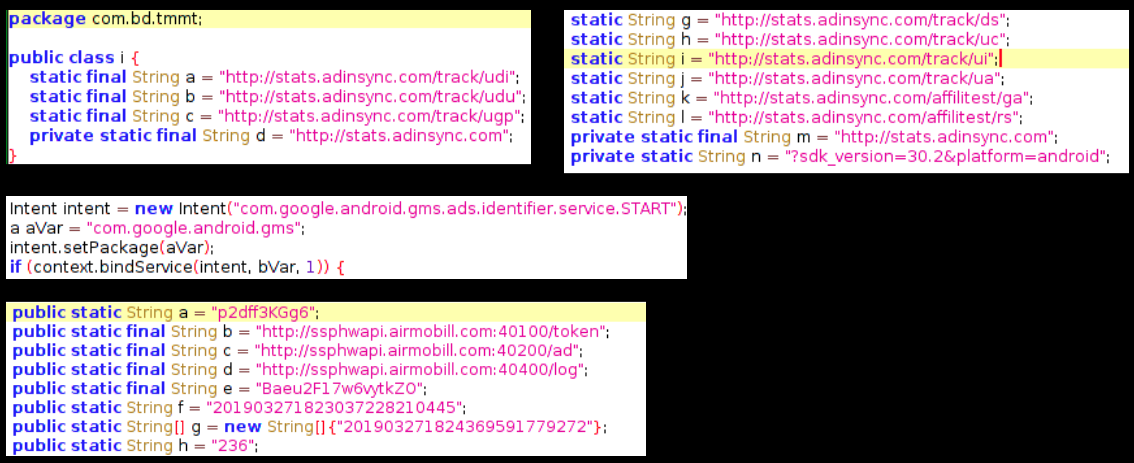
Contents of both the .jar files shows code related to adware components as visible below:
We did not see advertisements on our device during the analysis but we did see a number of URLs being contacted in the background, which have been marked as adware/malicious/phishing on VirusTotal:
- datastatis.coolook.org – IMEI is sent to this domain
- pv.sohu.com
- stats.adinsync.com
- ssphwapi.airmobill.com – IMEI, list of installed apps is sent to this domain
- offers-api.adflushlife.com
- click.howdoesin.net
- tknet.smardroid.com
- track.mob193.com
- tracking.volo-mobile.com
- offers-api.adflushlife.com
- 18.136.119.136
- 52.77.167.159
- click.trk-indexmobi.com
- tracking.lenzmx.com
- wathspap.com
- trk.iskyworker.com
Overall we confirm that the sample we analyzed is a malicious adware. Although we did not independently verify it, the user reported this app was not installed by him.
To further research this issue, we procured an actual Gretel A7 device and we will blog about our findings soon, so stay tuned!
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: AndroidOS.Gretel.PIN
Indicator of Compromise (IOC):
- 79272fcfbcfe359d5f2f554f87e3cf06