MFC Virus uses PROPagate Injection
Overview:
SonicWall Capture Labs Threat Research Team discovered another generic MFC Virus which is capable of copying itself and has a detrimental effect on the system it’s executed on by corrupting the system and destroying the data saved on your hard disk. The sample is written in MFC using C++ and uses the new PROPagate Injection technique to infect other processes running on the system.
The Virus has the following network information:
- www.ezdun.com
- 180.101.75.58
The virus scans the hard drive in search for “League of Legends” account details. If none exist the virus will keep copying itself and re-executing itself over and over until the hard-drive is completely full. During each iteration the processor will reach 100%. Meaning, you will not be able to use the computer while the copying process is in effect.
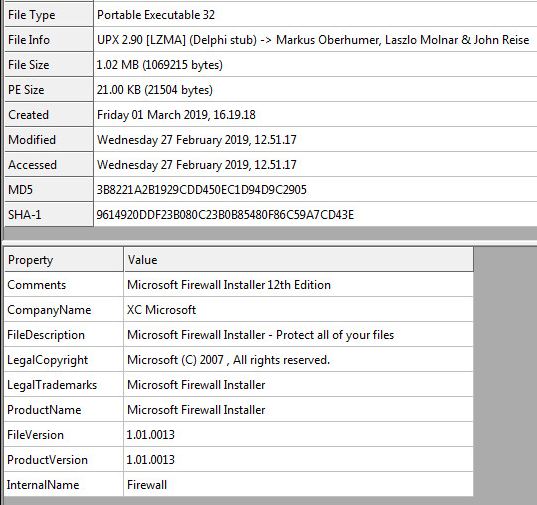
Sample Static Information:
Being that this Virus copies itself and executes over and over.
The static hashes for this file will continuously change for each iteration the sample copies itself.
Entropy, Compiler and Packer:
The sample is packed with in-line function VMProtect snippets of code:
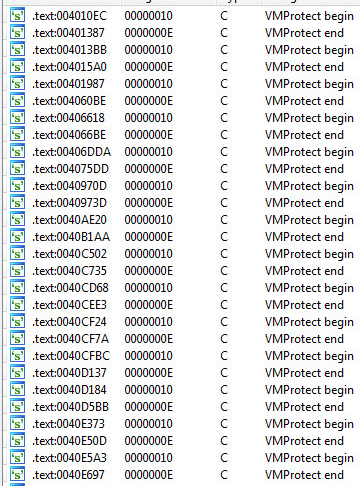
This will give a lower entropy as the whole file isn’t virtualized.
However, someone will still be able to see 90% of the code base in Ida Pro.
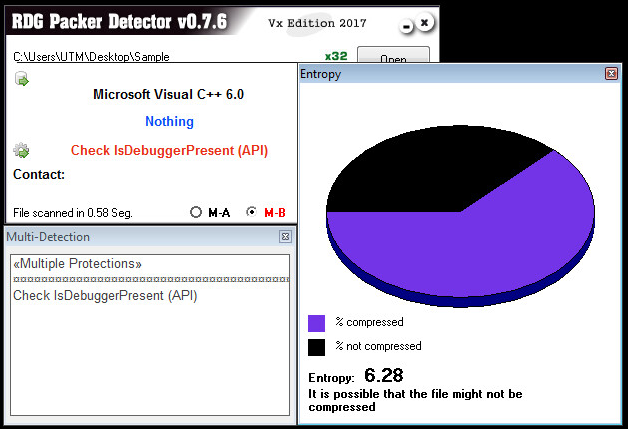
Encryption Used:
The following crypto signatures usually means the sample is linked with a few different libraries like OpenSSL.
In this case the sample is linked with the libraries, deflate 1.1.3 and inflate 1.1.3 among others like libpng 1.6.9.
When this happens you will see a variety of encryption signatures inside KANAL:
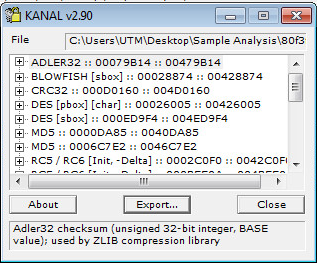
There is also a variety of xor encryption throughout the sample as seen below:
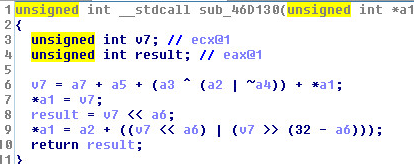
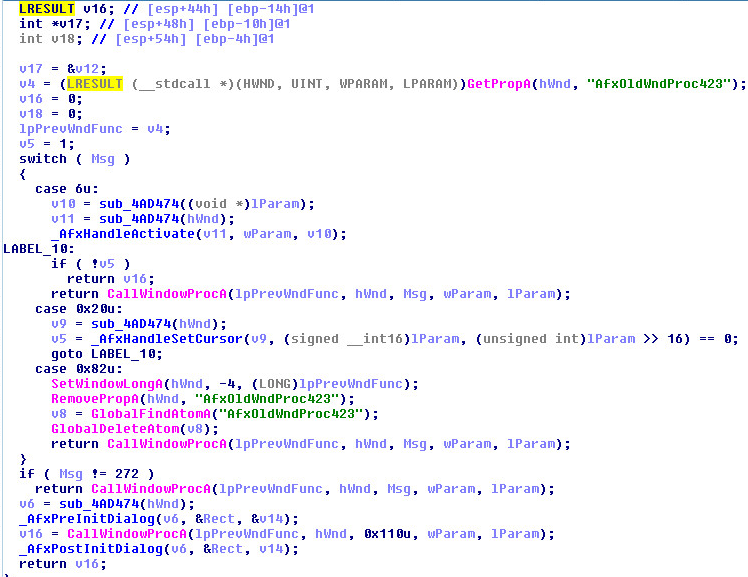
Injection & Hooking Technique:
When the Windows SetWindowSubclass API is called it uses the Windows SetProp API to set one of the following structure members (UxSubclassInfo, or CC32SubclassInfo) to point to an area in memory. When the new message routine is called, it will then call the Windows GetProp API for the given window and once the function pointer is retrieved the memory area will be executed.
When it comes to the process at the lower of equal integrity level the Microsoft documentation states:
- SetProp is subject to the restrictions of User Interface Privilege Isolation (UIPI). A process can only call this function on a window belonging to a process of lesser or equal integrity level. When UIPI blocks property changes, GetLastError will return 5.
There are plenty of processes that we can choose from to modify their window property!
Using the technique described above we can freely modify the property of a window belonging to another process.
All we need is a structure that UxSubclassInfo/CC32SubclassInfo properties are using. This is actually pretty easy – you can check what SetProp is doing for these subclassed windows. You will quickly realize that the procedure is stored at the offset 0x14 from the beginning of that memory region (the structure is a bit more complex as it may contain a number of callbacks, but the first one is at 0x14).
So, injecting a small buffer into a target process, ensuring the expected structure is properly filled-in and and pointing to the payload and then changing the respective window property will ensure the payload is executed next time the message is received by the window (this can be enforced by sending a message).
1st Part:
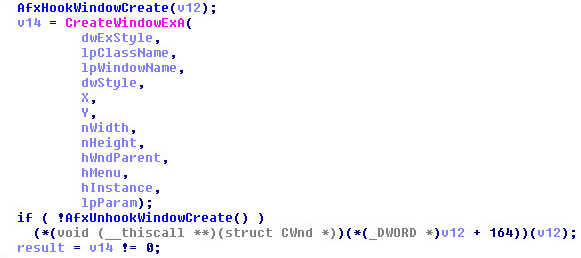
2nd Part:
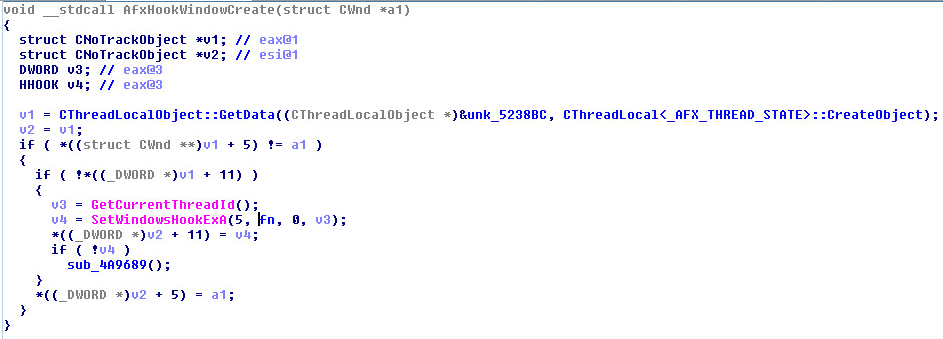
3rd Part:
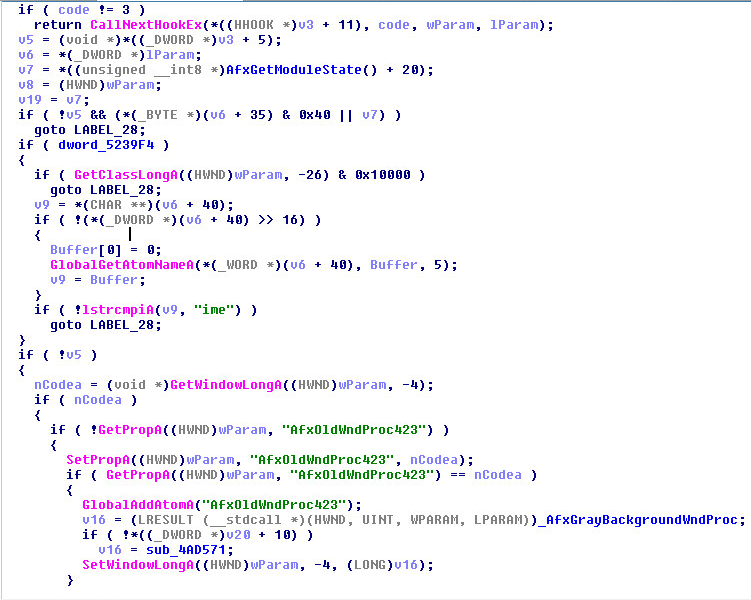
4th Part:
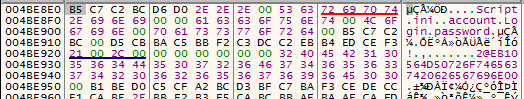
INI Configuration:
Sample Testing System:
Windows 7 Professional x86 32-bit
SonicWall Gateway AntiVirus, provides protection against this threat:
- GAV: MalAgent.H_11825 (Trojan)
- GAV: MalAgent.J_58357 (Trojan)
- GAV:Neshta.A_68 (Virus)




