Ransomware: "I'm not a Jigsaw variant!"
Since we have first reported seeing Jigsaw Ransomware back in 2016, we have seen several spinoffs of this ransomware. And because its source code can easily be downloaded from the world wide web we have reported variants we’ve seen like the Zapre ransomware here and was even possibly used here to teach ethical hacking.
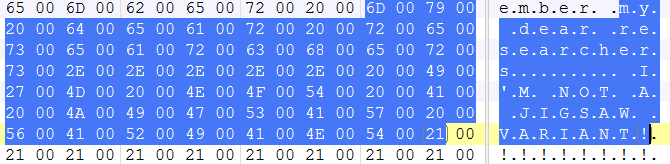
This week the Sonicwall Capture Labs Research team has seen yet another Jigsaw ransomware variant but who’s writer shamelessly denying its just another variant. In its ransom note it addresses security researchers and says “My dear researchers, I’m not a Jigsaw variant!!!!”
Infection Cycle:
This ransomware arrives as a seemingly harmless setup file using the following icon and file properties.
![]()
Once executed it creates the following directories using the number “0” to name Micr0soft and Wind0ws folders and drops a copy of itself:
- %APPDATA%\Local\MICR0SOFT\dllhost.exe
- %APPDATA%\Roaming\WIND0WS\svchost.exe
It then encrypts all files with the following file extensions:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sdf, .sql.dwg, .dxf.c, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js.aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as.txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm.wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .mkv.dat, .csv, .efx, .sdf, .vcf, .xml, .ses.rar, .zip, .zipx, .7zip
It creates a list of all encrypted files into a txt file and saves it into the following directory:
- %APPDATA%\Roaming\MICR0SOFT_FILES\EncryptedFileList.txt
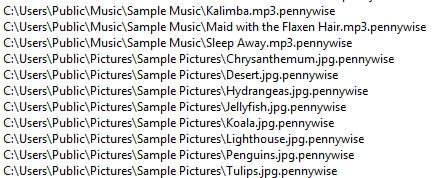
It appends “.pennywise” extension to all encrypted files.
Upon successful encryption it launches this ransom note window.
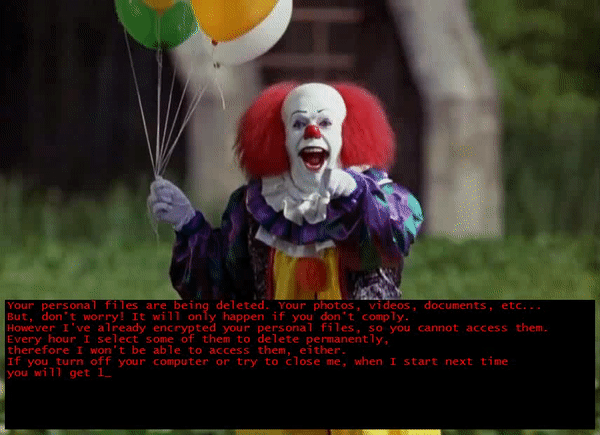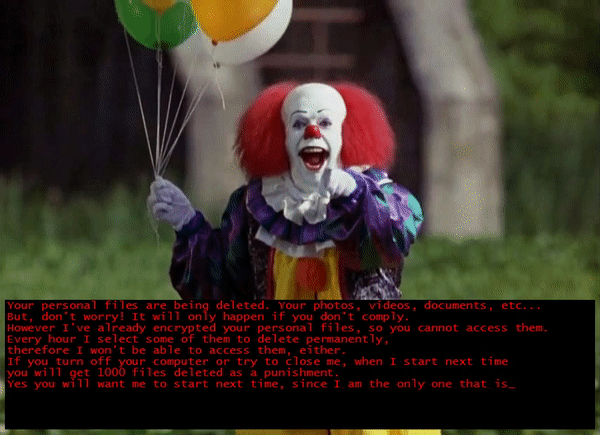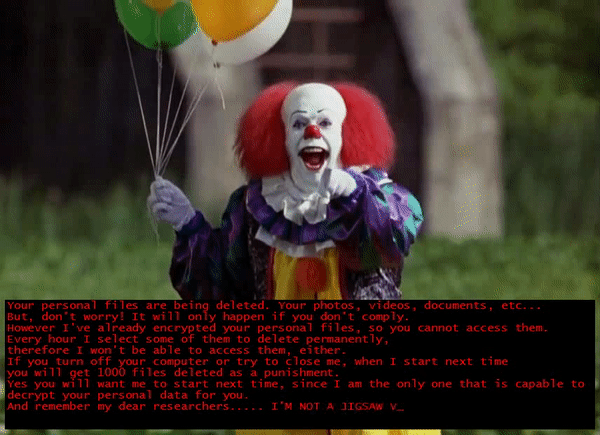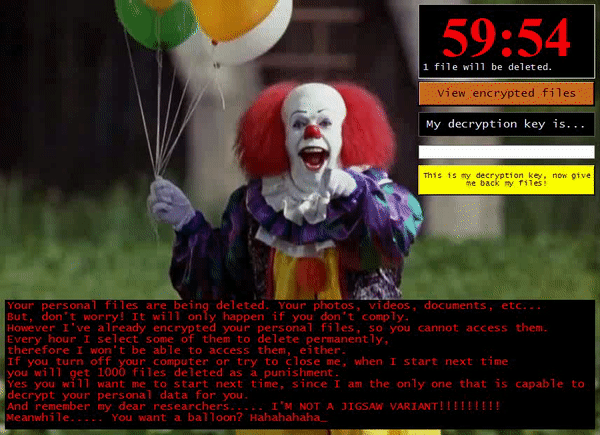
The ransom note just tells the victim that their files are now encrypted and that files will then be deleted after non-compliance but did not provide any clear instructions on how victims can get their files back. And after reminding security researchers that this is not another Jigsaw ransomware variant, it then starts a countdown before it deletes one file after every hour.
However, further analysis revealed that the decryption key was easily found in its strings – “PsTqQNhR77oKJXvBWE3YZc”.
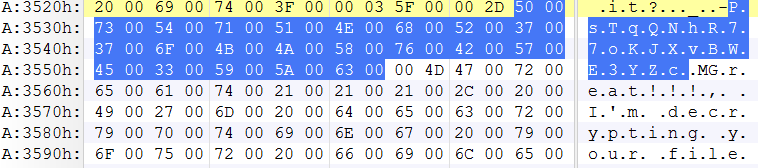
Copying this key into the decryption key box will start decrypting all the files. It also deletes all copies of itself and thus cleaning up the infected machine.
Because of the prevalence of these types of malware attacks, we urge our users to back up their files regularly.
SonicWALL Capture Labs provides protection against this threat via the following signature:
- GAV: Jigsaw.RSM_26 (Trojan)






