ORCA, Remote Access Trojan
Overview:
The SonicWall Capture Labs Threat Research Team, recently discovered the “ORCA” remote access Trojan. ORCA, allows an attacker to manipulate various processes and services from the command line. The attacker can execute arbitrary commands allowing the capability to upload and download files along with various other tasks involving the file system.
The following IP addresses and DNS information are seen after the Trojan executes itself.
adda.lengendport.com
tsl.gettrials.com
auty.organiccrap.com
11.38.64.251
123.120.99.228
147.96.68.184
176.31.24.184
202.2.108.142
203.146.251.11
213.147.54.170
23.19.39.19
62.73.174.134
71.183.67.163
91.198.50.31
Static Information:
Encryption Routine & Key:
Inside Ida Pro, we can locate the following key information for how this Trojan was named. Inside function “401200” we see the following xor routine:
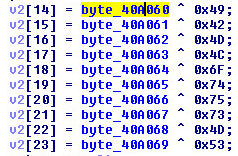
By using the byte array “byte_40A060” as a key to the xor routine. We can now decode the information:
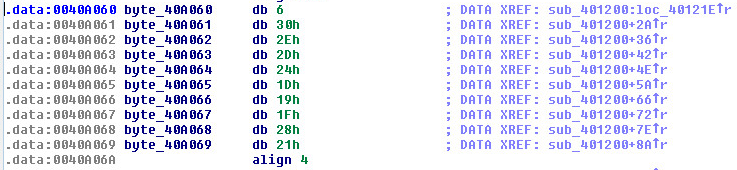
- 0x06 ^ 0x49 = 0x4f = O
- 0x30 ^ 0x42 = 0x72 = r
- 0x2E ^ 0x4D = 0x63 = c
- 0x2D ^ 0x4C = 0x63 = a
- 0x24 ^ 0x6F = 0x4B = K
- 0x1D ^ 0x74 = 0x69 = i
- 0x19 ^ 0x75 = 0x6C = l
- 0x1F ^ 0x73 = 0x6C = l
- 0x28 ^ 0x4D = 0x65 = e
- 0x21 ^ 0x53 = 0x72 = r
String: “OrcaKiller”
The “OrcaKiller” Trojan calls the Windows Crypto API to generate a pseudo random number of around 6 bytes.
This random generated number concatenates itself to the string “OrcaKiller”. We now have “[6 bytes]OrcaKiller”.
With both parts of the generated string known. The Trojan now uses this information to encrypt other pieces of information.
Network Information
The following image shows the dns, header content and type along with the port number used by the Trojan
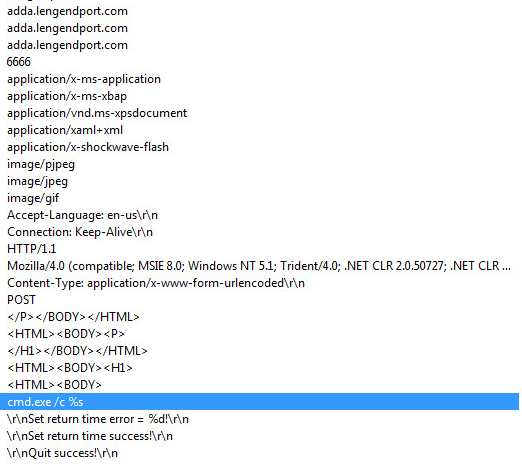
The Trojan looks for specific sets of HTML tags. The first set can be seen in the image below as “P” and the terminating tag “/P”. Once the Trojan has found the correct tags it drops in to the first command and control function. It then extracts the payload text between the HTML tags and runs it through the decryption routine. The same encryption key used above is used to decrypt the text. Once the payload text has been decrypted the Trojan treats this as a binary executable file, which is then written to the disk and executed.
Summary of Capabilities:
- System/network information gathering
- Keystroke logging
- Screenshots
- File upload/download/execute
- Command shell
SonicWall Gateway AntiVirus, provides protection against this threat:




